
The Android ‘SpyNote’ malware was noticed in assaults concentrating on Italy utilizing a faux ‘IT-alert’ public alert service that contaminated guests with the information-stealing malware.
IT-alert is a reliable public service operated by the Italian authorities, particularly the Division of Civil Safety, to supply emergency alerts and steerage to the inhabitants throughout imminent or ongoing disasters reminiscent of wildfires, floods, earthquakes, and many others.
Italian researchers on the D3Lab first noticed the faux IT-alert website, which is warning of an elevated chance of an upcoming volcano eruption, urging guests to put in the app to stay knowledgeable.
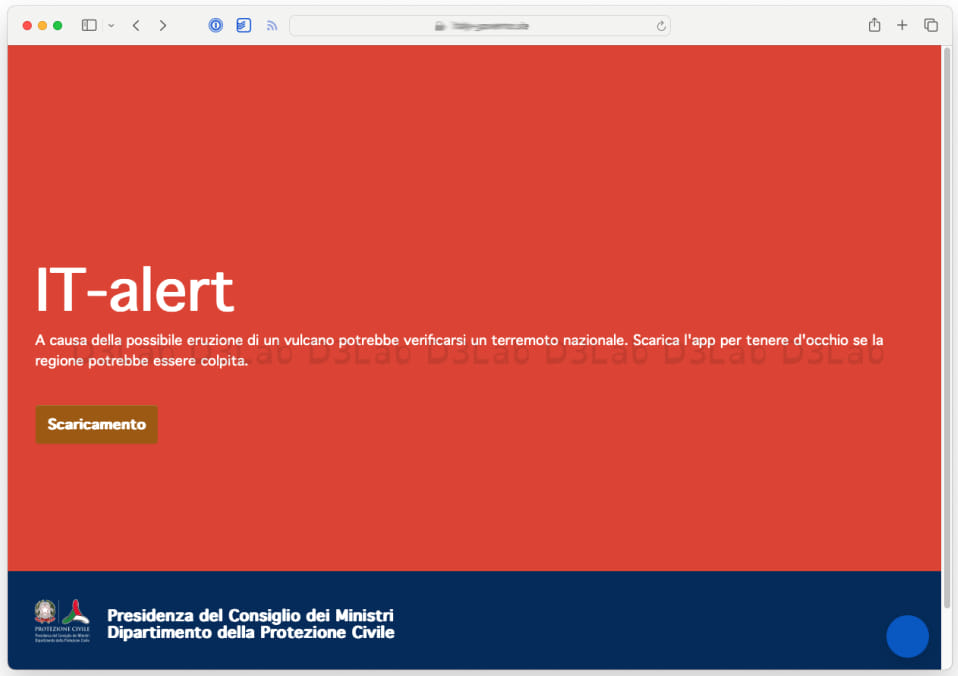
If the obtain button is clicked from an iOS machine, the person is redirected to the true IT-alert website, however Android customers making an attempt to obtain the app straight obtain ‘IT-Alert.apk.’
The APK (Android package deal) file installs SpyNote malware on the machine, granting it permission to make use of Accessibility companies, which allow the attackers to carry out a variety of harmful and invasive actions on the compromised machine.
(D3Lab)
SpyNote may carry out overlay injection assaults to steal person credentials when the sufferer opens banking, cryptocurrency pockets, and social media purposes.
Different documented capabilities of the actual malware embrace digicam recording, GPS and community location monitoring, normal keylogging, screenshot capturing, telephone name recording, and concentrating on Google and Fb accounts.
SpyNote spikes after supply code leak
The SpyNote Android malware was first documented in 2022 and is now in its third main model, which is offered to cybercriminals via Telegram.
In January 2023, a ThreatFabric report warned that SpyNote detections spiked following the supply code leak of one among its variants, codenamed ‘CypherRat.’
A few of those that received their arms on the leaked supply code created customized variants concentrating on particular banks, whereas others opted to masquerade it as Google’s Play Retailer, Play Shield, WhatsApp, and Fb.
Late final week, a report from F-Safe highlighted the rising prominence of SpyNote, offering an in depth evaluation of its options and capabilities.
To defend from these threats, keep away from downloading and putting in APKs from outdoors the Play Retailer until you particularly belief the writer.
