Over the weekend rumours circulated on social networks of an unpatched safety gap within the Sign messaging app that might permit a distant hacker to grab management of your smartphone.
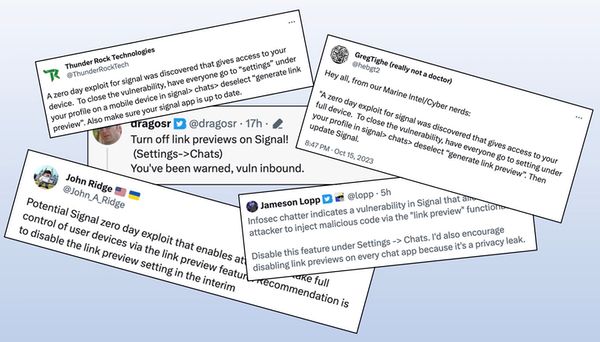
The rumours, which quickly unfold additional than the cybersecurity group into the broader public, claimed that the Sign encrypted messaging app contained a flaw associated to its “Generate Hyperlink Previews” characteristic that may very well be exploited by hackers.
As somebody as soon as mentioned, a lie can journey midway world wide earlier than the reality has bought its boots on. And the state of affairs is even worse within the twenty first century, the place anybody has the ability to submit a declare on Twitter, and watch it’s retweeted and reshared 1000’s and 1000’s of instances earlier than anybody takes the time to ask a troublesome query.
Some individuals did trouble to reply to the rumours, asking for extra particulars or a supply that may affirm there was a problem. Which appears fairly affordable. In spite of everything, an encrypted messaging app like Sign is utilized by privacy-conscious people who wish to hold their communications secret.
Nevertheless, within the threads I noticed on-line, anybody asking for extra particulars of the so-called vulnerability have been fobbed off with “I heard it from a trusted supply” or imprecise references to unnamed people inside the US authorities.
In brief, there have been no actual particulars of a zero-day vulnerability having been present in Sign in any respect.
And the concept that the hyperlink preview characteristic of Sign is likely to be linked to the alleged vulnerability appeared unlikely.
Though it is true that previously different messaging apps have been discovered to disclose a person’s location via preview hyperlinks, it is not the case with Sign.
Sign generates hyperlink previews (when the characteristic is enabled) earlier than the hyperlink is distributed to the opposite Sign person – not after.
In different phrases, disabling “hyperlink previews” in Sign (the recommendation being given within the faulty warnings posted on social media) solely prevents creation of hyperlink previews in your machine, you’re nonetheless capable of obtain them from others.
Earlier in the present day, Sign posted a message on Twitter stating that it had seen no proof that the vulnerability was actual.
It went on to say that it had “checked with individuals throughout US Authorities, because the copy-paste report claimed USG as a supply. These we spoke to haven’t any data suggesting it is a legitimate declare.”
Sign’s President, Meredith Whittaker, commented that “the imprecise and viral type of the report has the hallmarks of a disinfo marketing campaign.”
I do not know if the seemingly baseless rumours of a Sign flaw have been begun maliciously or not, however it actually is the case that Sign has loads of enemies who would like to see its status tarnished.
Even when there is not a zero-day vulnerability in Sign as the net rumours described, it nonetheless is sensible to apply protected computing, make sure that your privateness settings are configured as you count on them to be, and that you’re guaranteeing that your apps are correctly up to date.

