
Cisco disclosed a brand new high-severity zero-day (CVE-2023-20273) immediately, actively exploited to deploy malicious implants on IOS XE gadgets compromised utilizing the CVE-2023-20198 zero-day unveiled earlier this week.
The corporate mentioned it discovered a repair for each vulnerabilities and estimates it will likely be launched to prospects through the Cisco Software program Obtain Heart over the weekend, beginning October 22.
“Fixes for each CVE-2023-20198 and CVE-2023-20273 are estimated to be accessible on October 22. The CVE-2021-1435 that had beforehand been talked about is now not assessed to be related to this exercise,” Cisco mentioned immediately.
On Monday, Cisco disclosed that unauthenticated attackers have been exploiting the CVE-2023-20198 authentication bypass zero-day since at the least September 18 to hack into IOS XE gadgets and create “cisco_tac_admin” and “cisco_support.”
As revealed immediately, the CVE-2023-20273 privilege escalation zero-day is then used to realize root entry and take full management over Cisco IOS XE gadgets to deploy malicious implants that allow them to execute arbitrary instructions on the system.
Over 40,000 Cisco gadgets working the susceptible IOS XE software program have already been compromised by hackers utilizing the 2 still-unpatched zero-days, in response to Censys and LeakIX estimations. Two days earlier, VulnCheck estimates have been floating round 10,000 on Tuesday, whereas the Orange Cyberdefense CERT mentioned in the future later that it discovered malicious implants on 34,500 IOS XE gadgets.
Networking gadgets working Cisco IOS XE embrace enterprise switches, entry factors, wi-fi controllers, in addition to industrial, aggregation, and department routers.
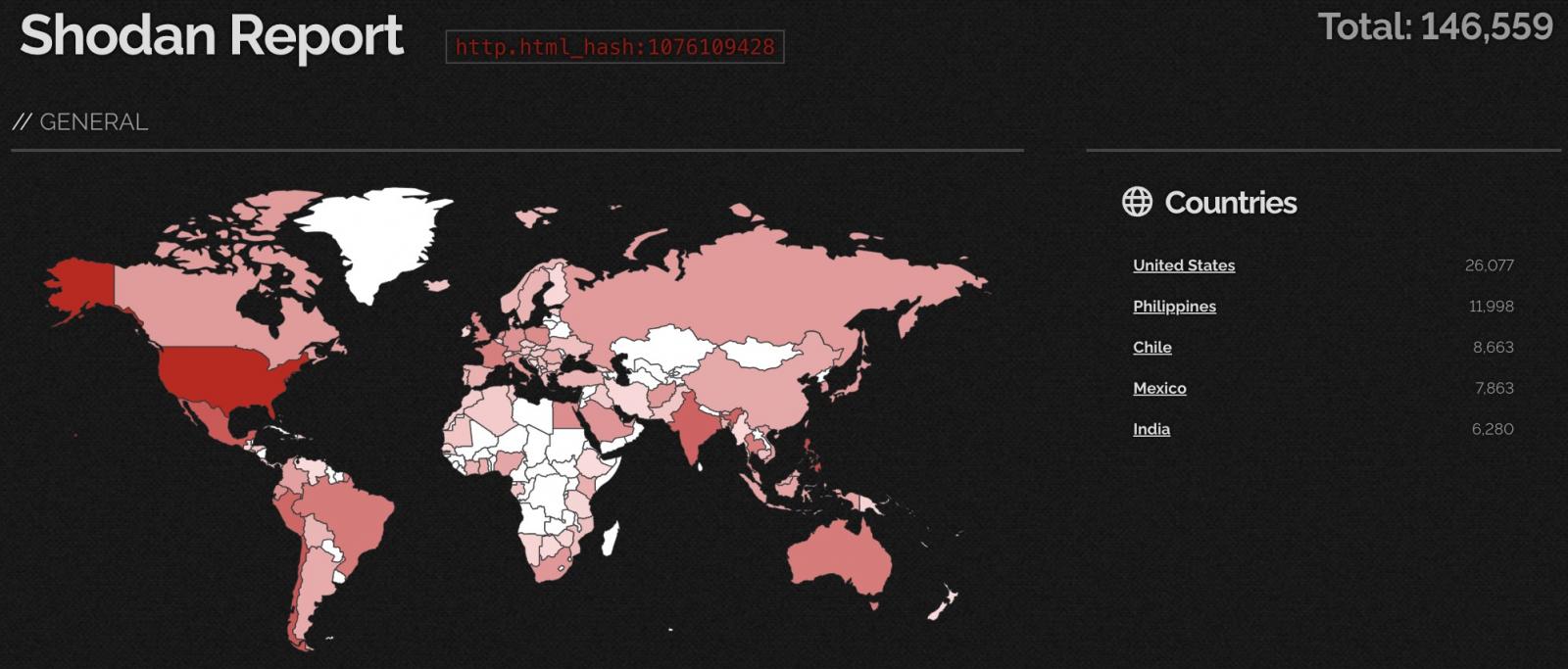
Whereas it is arduous to get the precise variety of Web-exposed Cisco IOS XE gadgets, a Shodan search presently exhibits that greater than 146K susceptible techniques are uncovered to assaults.
Cisco has cautioned directors that, regardless that safety updates are unavailable, they will nonetheless block incoming assaults by disabling the susceptible HTTP server function on all internet-facing techniques.
“We strongly urge prospects to take these speedy actions as additional outlined in our up to date safety advisory and Talos weblog,” a Cisco spokesperson informed BleepingComputer.
Admins are additionally strongly suggested to search for suspicious or just lately created person accounts as potential indicators of malicious exercise related to these ongoing assaults.
One solution to detect the malicious implant on compromised Cisco IOS XE gadgets requires working the next command on the system, the place the placeholder “DEVICEIP” represents the IP tackle underneath investigation:
curl -k -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"
Final month, Cisco warned prospects to patch one other zero-day bug (CVE-2023-20109) in its IOS and IOS XE software program, additionally focused by attackers within the wild
