The variety of Cisco IOS XE units hacked with a malicious backdoor implant has mysteriously plummeted from over 50,000 impacted units to only some hundred, with researchers uncertain what’s inflicting the sharp decline.
This week, Cisco warned that hackers exploited two zero-day vulnerabilities, CVE-2023-20198 and CVE-2023-20273, to hack over 50,000 Cisco IOS XE units to create privileged person accounts and set up a malicious LUA backdoor implant.
This LUA implant permits the menace actors to remotely execute instructions at privilege degree 15, the very best privilege degree on the gadget.
Nonetheless, this implant doesn’t embody persistence, that means a reboot will take away the backdoor. Nonetheless, any native customers created in the course of the assault will stay.
Because the launch of this information, cybersecurity companies and researchers have discovered roughly 60,000 out of the 80,000 publicly uncovered Cisco ISO XE units to be breached with this implant.
Mysterious drop in detected Cisco implants
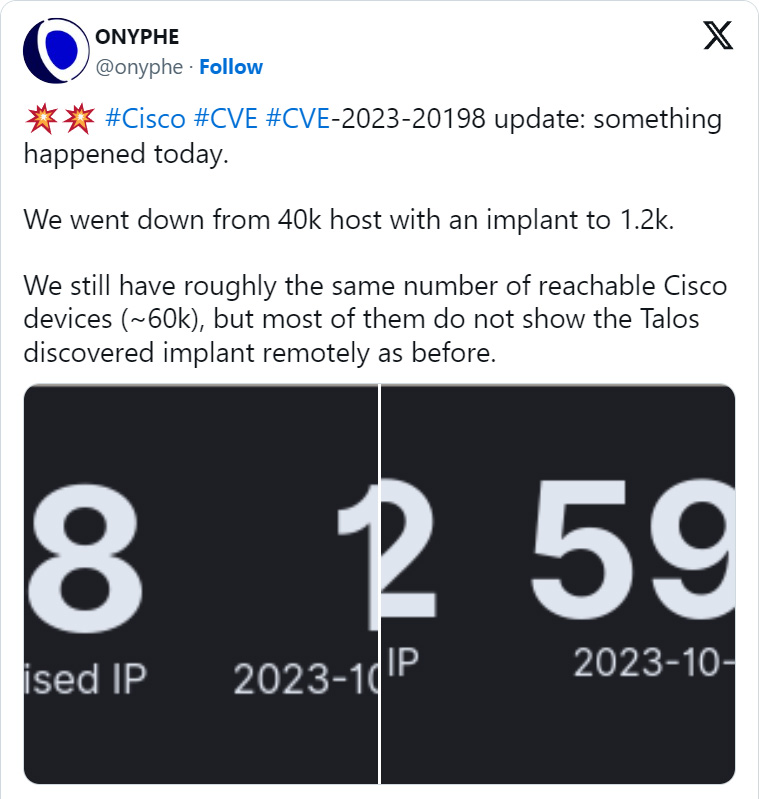
On Saturday, a number of cybersecurity organizations reported that the variety of Cisco IOS XE units with a malicious implant has mysteriously dropped from roughly 60,000 units to solely 100-1,200, relying on the completely different scans.
Onyphe Founder & CTO Patrice Auffret informed BleepingComputer that he believes the menace actors behind the assaults are deploying an replace to cover their presence, thus inflicting the implants to be now not seen in scans.
“For the second day in a row, we see the variety of implants have drastically dropped in a short while (see screenshots hooked up). Principally, they seem to have been virtually all rebooted (because the recognized implant does not survive a reboot) or have been up to date.”
“We consider it’s the motion from the unique menace actor which is attempting to repair a difficulty that ought to not have been there from the start. The truth that the implant was really easy to detect remotely was a mistake from their aspect.
“They’re in all probability deploying an replace to cover their presence.”
Piotr Kijewski, the CEO of The Shadowserver Basis, additionally informed BleepingComputer that they’ve seen a pointy drop in implants since 10/21, with their scans solely seeing 107 units with the malicious implant.
“The implant seems to have been both eliminated or up to date not directly,” Kijewski informed BleepingComputer by way of electronic mail.
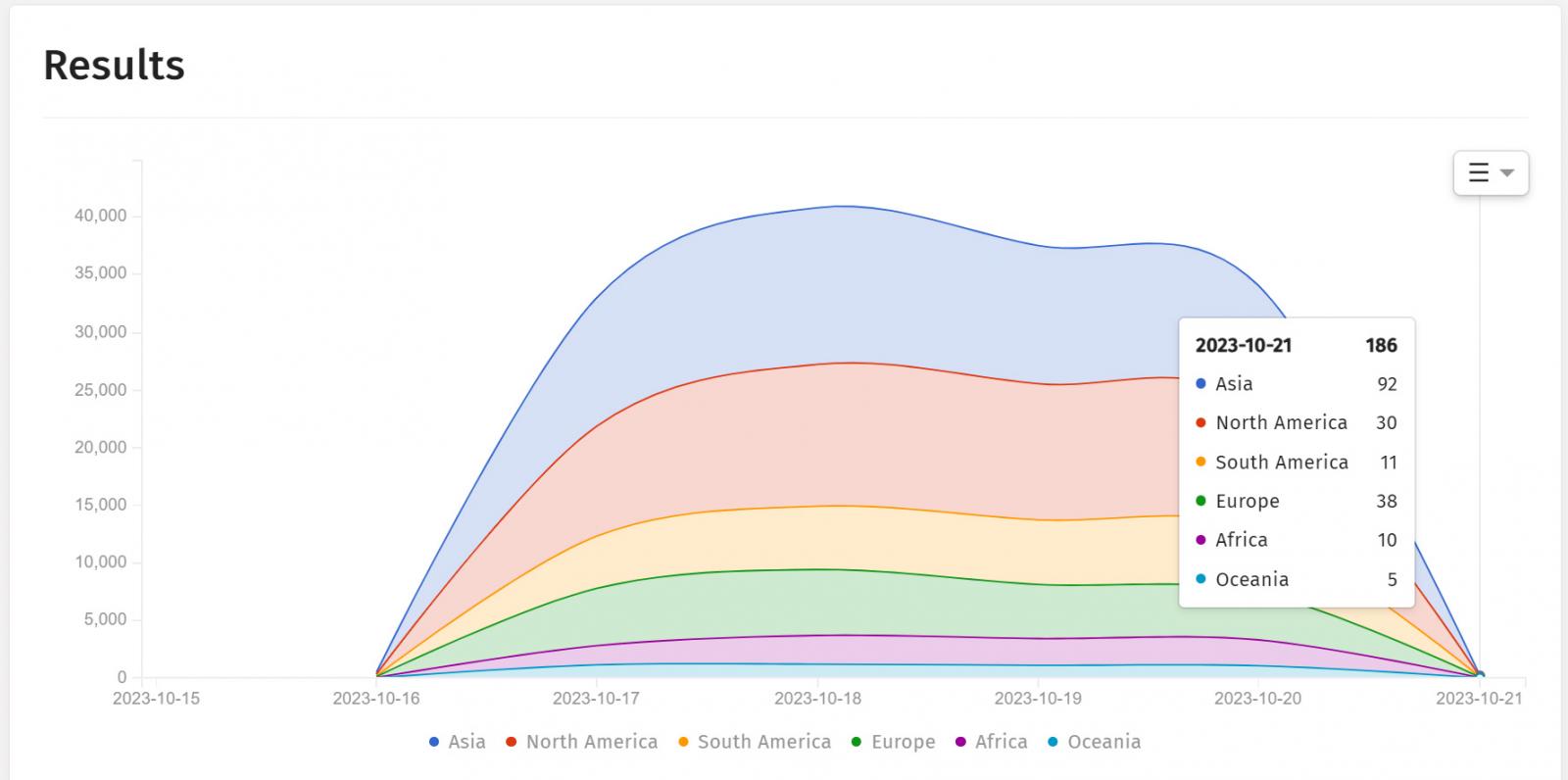
Supply: ShadowServer
One other idea is {that a} grey-hat hacker is automating the reboot of impacted Cisco IOS XE units to clear the implant. A related marketing campaign was seen in 2018 when a hacker claimed to have patched 100,000 MikroTik routers so they might not be abused for cryptojacking and DDoS campaigns.
Nonetheless, Orange Cyberdefense CERT for the Orange Group informed BleepingComputer that they don’t consider {that a} grey-hat hacker is behind the lower in implants however quite that this may very well be a brand new exploitation section.
“Please be aware {that a} potential hint cleansing step is underway to cover the implant (following exploitation of #CVE-2023-20198),” tweeted Orange Cyberdefense CERT.
“Even if in case you have disabled your WebUI, we advocate that you simply perform an investigation to make it possible for no malicious customers has been added and that its configuration has not been altered.”
One other chance shared by safety researcher Daniel Card is that the numerous units breached with implants have been merely a decoy to cover the true targets in assaults.
Sadly, all we’ve are theories presently. Till Cisco or different researchers can look at a beforehand breached Cisco IOS XE gadget to see in the event that they have been merely rebooted or if new modifications have been made, there isn’t any approach to know what occurred.
BleepingComputer has contacted Cisco with questions in regards to the drop in implants however has not acquired a reply presently.