Previously 12 months, cyberattacks have touched 120 nations, fueled by government-sponsored spying and with affect operations (IO) additionally rising. At instances, practically half of those assaults focused NATO member states, and greater than 40% had been leveled towards authorities or private-sector organizations concerned in constructing and sustaining vital infrastructure. Whereas headline-grabbing assaults from the previous 12 months had been typically centered on destruction or monetary achieve with ransomware, information reveals the predominant motivation has swung again to a want to steal info, covertly monitor communication, or to control what folks learn. For instance:
- Russian intelligence companies have refocused their cyberattacks on espionage exercise in assist of their struggle towards Ukraine, whereas persevering with harmful cyberattacks in Ukraine and broader espionage efforts
- Iranian efforts, as soon as centered on taking down the networks of their targets, are additionally inclined right this moment to amplify manipulative messages to additional geopolitical objectives or faucet into information flowing by delicate networks
- China has expanded its use of spying campaigns to achieve intelligence to gasoline its Belt and Street Initiative or regional politics, to spy on the U.S. together with key services for the U.S. navy, and to determine entry to the networks of vital infrastructure entities
- North Korean actors have been making an attempt to covertly steal secrets and techniques; they’ve focused an organization concerned in submarine expertise, whereas individually utilizing cyberattacks to steal tons of of thousands and thousands in cryptocurrency
These are among the insights from the fourth annual Microsoft Digital Protection Report, which covers developments between July 2022 and June 2023 throughout nation-state exercise, cybercrime, and protection strategies.
Extra nations, sectors beneath assault
Whereas the U.S., Ukraine, and Israel proceed to be most closely attacked, the final 12 months has seen a rise within the international scope of assaults. That is significantly the case within the International South, particularly Latin America and sub-Saharan Africa. Iran elevated its operations within the Center East. Organizations concerned in policymaking and execution had been among the many most focused, in step with the shift in focus to espionage.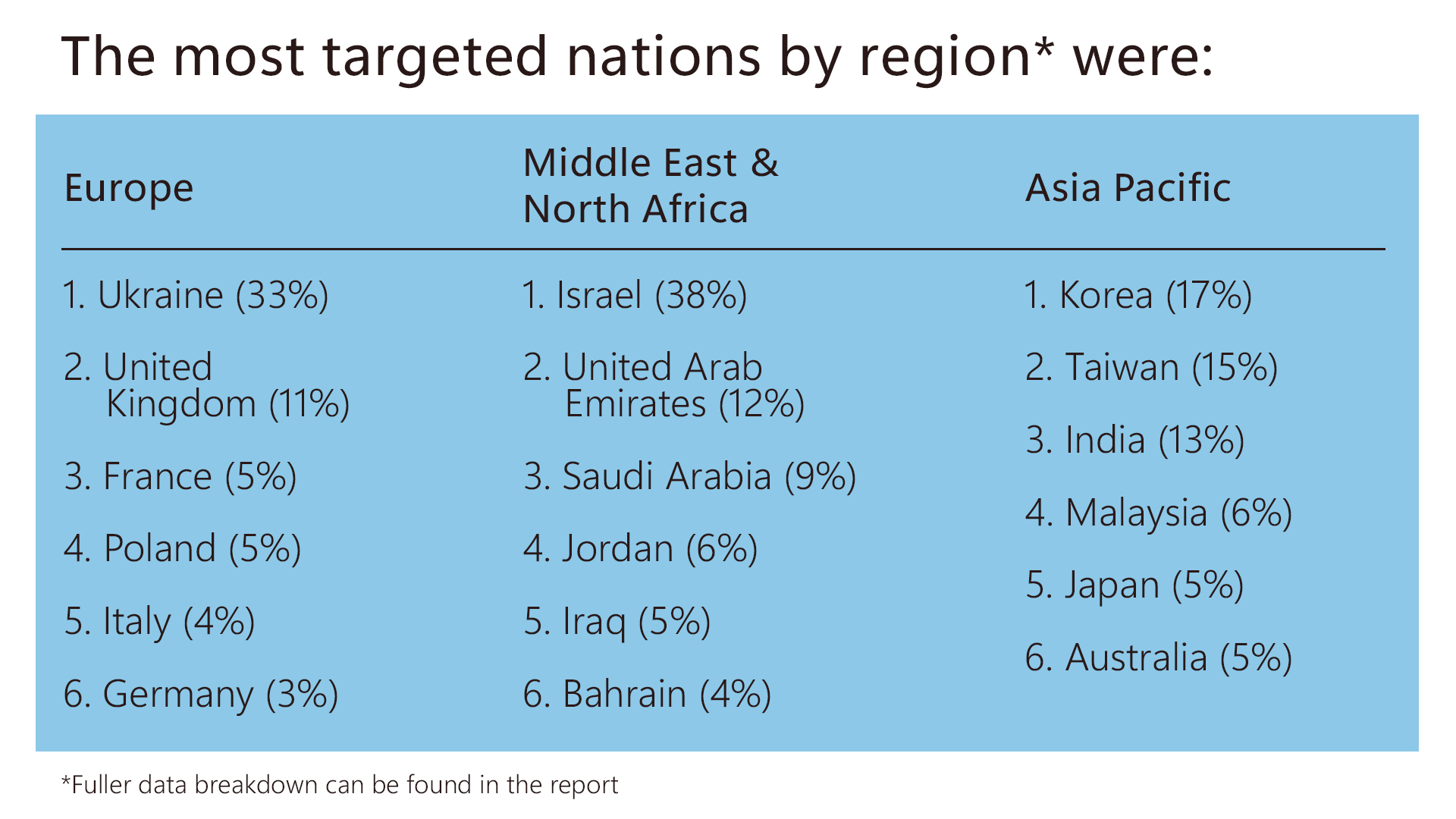
Russia and China enhance concentrate on diaspora communities
Each Russia and China are growing the scope of their affect operations towards a wide range of diasporas. Russia goals to intimidate international Ukrainian communities and sow distrust between struggle refugees and host communities in a spread of nations, particularly Poland and the Baltic states. Against this, China deploys an unlimited community of coordinated accounts throughout dozens of platforms to unfold covert propaganda. These immediately goal international Chinese language-speaking and different communities, denigrating U.S. establishments, and selling a optimistic picture of China by tons of of multilingual life-style influencers.
Convergence of affect operations with cyberattacks
Nation state actors are extra often using IO alongside cyber operations to unfold favored propaganda narratives. These purpose to control nationwide and international opinion to undermine democratic establishments inside perceived adversary nations – most dangerously within the contexts of armed conflicts and nationwide elections. For instance, following its invasion of Ukraine, Russia persistently timed its IO operations with navy and cyberattacks. Equally, in July and September 2022, Iran adopted harmful cyberattacks on the Albanian authorities with a coordinated affect marketing campaign which remains to be ongoing.
Tendencies by nation state
Whereas there was a rise general in risk exercise, developments have been noticed with probably the most energetic nation state actors.
- Russia targets Ukraine’s NATO allies
Russian state actors expanded their Ukraine-related actions to focus on Kyiv’s allies, principally NATO members. In April and Could 2023, Microsoft noticed a spike in exercise towards Western organizations, 46% of which had been in NATO member states, significantly the US, the UK, and Poland. A number of Russian state actors posed as Western diplomats and Ukrainian officers, making an attempt account entry. The aim was to acquire insights into Western international coverage on Ukraine, protection plans and intentions, and struggle crimes investigations. - China targets US protection, South China Sea nations and Belt and Street Initiative companions
China’s expanded and complicated actions mirror its twin pursuits of worldwide affect and intelligence assortment. Their targets are mostly U.S. protection and significant infrastructure, nations bordering the South China Sea (particularly Taiwan) and even China’s personal strategic companions. Along with the a number of refined assaults on U.S. infrastructure detailed within the report, Microsoft has additionally seen China-based actors assault China’s Belt and Street Initiative companions comparable to Malaysia, Indonesia, and Kazakhstan. - Iran brings new assaults to Africa, Latin America, and Asia
The previous 12 months has seen some Iranian state actors enhance the complexity of their assaults. Iran has not solely focused Western nations it believes are fomenting unrest inside Iran, but it surely has additionally expanded its geographical attain to incorporate extra Asian, African, and Latin American nations. On the IO entrance, Iran has pushed narratives that search to bolster Palestinian resistance, sow panic amongst Israeli residents, foment Shi’ite unrest in Gulf Arab nations, and counter the normalization of Arab-Israeli ties. Iran has additionally made efforts to extend the coordination of its actions with Russia. - North Korea targets Russian organizations amongst others
North Korea has elevated the sophistication of its cyber operations within the final 12 months, particularly in cryptocurrency theft and supply-chain assaults. Moreover, North Korea is utilizing spear-phishing emails and LinkedIn profiles to focus on Korean peninsula consultants world wide to assemble intelligence. Regardless of the latest assembly between Putin and Kim Jong-Un, North Korea is concentrating on Russia, particularly for nuclear power, protection, and authorities coverage intelligence assortment.
AI creates new threats – and new alternatives for protection
Attackers are already utilizing AI as a weapon to refine phishing messages and enhance affect operations with artificial imagery. However AI will even be essential for profitable protection, automating, and augmenting points of cybersecurity comparable to risk detection, response, evaluation, and prediction. AI may allow massive language fashions (LLMs) to generate pure language insights and proposals from advanced information, serving to make analysts more practical and responsive.
We’re already seeing AI-powered cyber-defense reversing the tide of cyberattacks; in Ukraine, for instance, AI has helped defend towards Russia.
As transformative AI reshapes many points of society, we should have interaction in Accountable AI practices essential for sustaining person belief and privateness, and for creating long-term advantages. Generative AI fashions require us to evolve cybersecurity practices and risk fashions to handle new challenges, such because the creation of lifelike content material – together with textual content, pictures, video, and audio – that can be utilized by risk actors to unfold misinformation or create malicious code. To remain forward of those rising threats, we stay dedicated to making sure that every one our AI services and products are developed and utilized in a fashion that upholds our AI ideas.
The state of cybercrime
The sport of cat and mouse between cybercriminals and defenders continues to evolve. Whereas risk teams have considerably accelerated the tempo of their assaults during the last 12 months, built-in protections throughout Microsoft merchandise have blocked tens of billions of malware threats, thwarted 237 billion brute-force password assault makes an attempt, and mitigated 619,000 distributed denial of service (DDoS) assaults that purpose to disable a server, service, or community by overwhelming it with a flood of web visitors.
Criminals are additionally trying to enhance their anonymity and effectiveness, through the use of distant encryption to cowl their traces extra successfully in addition to cloud-based instruments comparable to digital machines. However stronger personal and public partnerships imply that they’re more and more discovering themselves within the crosshairs of legislation enforcement. For instance, the ransomware operator referred to as Goal was outed, and arrests and indictments had been efficiently made. However criminals proceed to search for the factors of best entry to methods and a steady and accelerating effort is required to remain one step forward of them.
Ransomware assaults enhance in sophistication and velocity
Microsoft’s telemetry signifies organizations noticed human-operated ransomware assaults enhance 200% since September 2022. These assaults are usually a “palms on keyboard” sort of assault relatively than an automatic one, usually concentrating on an entire group with custom-made ransom calls for.
Attackers are additionally evolving assaults to reduce their footprint, with 60% utilizing distant encryption, thereby rendering process-based remediation ineffective.
These assaults are additionally notable for the way they try to achieve entry to unmanaged or bring-your-own gadgets. Greater than 80% of all compromises we noticed originate from such unmanaged gadgets. Ransomware operators are more and more exploiting vulnerabilities in much less frequent software program, making it harder to foretell and defend towards assaults.
Ransomware criminals additionally threaten disclosure of stolen info to strain victims and extract fee. Since November 2022, we now have noticed a doubling of potential information exfiltration cases after risk actors compromised an surroundings. However not all information theft is related to ransomware; it will also be for credential harvesting or nation-state espionage.
Password-based and Multifactor Authentication (MFA) fatigue assaults skyrocket
MFA is the more and more frequent authentication technique that requires customers to offer two or extra “components” of identification to achieve entry to an internet site or software – comparable to a password together with facial recognition or a one-time passcode. Whereas deploying MFA is likely one of the best and handiest defenses organizations can deploy towards assaults, decreasing the chance of compromise by 99.2%, risk actors are more and more making the most of “MFA fatigue” to bombard customers with MFA notifications within the hope they’ll lastly settle for and supply entry.
Microsoft has noticed roughly 6,000 MFA fatigue makes an attempt per day over the previous 12 months. Moreover, the primary quarter of 2023 noticed a dramatic tenfold surge in password-based assaults towards cloud identities, particularly within the training sector, from round 3 billion per thirty days to over 30 billion – a mean of 4,000 password assaults per second concentrating on Microsoft cloud identities this 12 months.
The one safe protection will likely be a collective protection
The size and nature of threats outlined within the Microsoft Digital Protection Report can seem dispiriting. However enormous strides are being made on the expertise entrance to defeat these attackers and on the identical time, robust partnerships are being solid that transcend borders, industries, and the private-public divide. These partnerships are having ever larger success in holding us all protected and for this reason it’s critical we proceed to broaden and deepen them. Some 75% of eligible residents in democratic nations have the chance to vote within the subsequent 12 months and a half. Retaining elections protected and democratic establishments robust is a cornerstone of our collective protection.

