The password supervisor service LastPass is now forcing a few of its customers to choose longer grasp passwords. LastPass says the modifications are wanted to make sure all clients are protected by their newest safety enhancements. However critics say the transfer is little greater than a public relations stunt that may do nothing to assist numerous early adopters whose password vaults have been uncovered in a 2022 breach at LastPass.
LastPass despatched this notification to customers earlier this week.
LastPass informed clients this week they might be compelled to replace their grasp password if it was lower than 12 characters. LastPass formally instituted this alteration again in 2018, however some undisclosed variety of the corporate’s earlier clients have been by no means required to extend the size of their grasp passwords.
That is vital as a result of in November 2022, LastPass disclosed a breach through which hackers stole password vaults containing each encrypted and plaintext information for greater than 25 million customers.
Since then, a gentle trickle of six-figure cryptocurrency heists focusing on security-conscious folks all through the tech trade has led some safety specialists to conclude that crooks seemingly have succeeded at cracking open a number of the stolen LastPass vaults.
KrebsOnSecurity final month interviewed a sufferer who lately noticed greater than three million {dollars} value of cryptocurrency siphoned from his account. That person signed up with LastPass almost a decade in the past, saved their cryptocurrency seed phrase there, and but by no means modified his grasp password — which was simply eight characters. Nor was he ever compelled to enhance his grasp password.
That story cited analysis from Adblock Plus creator Wladimir Palant, who mentioned LastPass did not improve many older, unique clients to safer encryption protections that have been supplied to newer clients over time.
For instance, one other vital default setting in LastPass is the variety of “iterations,” or what number of instances your grasp password is run by way of the corporate’s encryption routines. The extra iterations, the longer it takes an offline attacker to crack your grasp password.
Palant mentioned that for a lot of older LastPass customers, the preliminary default setting for iterations was anyplace from “1” to “500.” By 2013, new LastPass clients got 5,000 iterations by default. In February 2018, LastPass modified the default to 100,100 iterations. And really lately, it upped that once more to 600,000. Nonetheless, Palant and others impacted by the 2022 breach at LastPass say their account safety settings have been by no means forcibly upgraded.
Palant known as this newest motion by LastPass a PR stunt.
“They despatched this message to everybody, whether or not they have a weak grasp password or not – this fashion they’ll once more blame the customers for not respecting their insurance policies,” Palant mentioned. “However I simply logged in with my weak password, and I’m not compelled to alter it. Sending emails is affordable, however they as soon as once more didn’t implement any technical measures to implement this coverage change.”
Both method, Palant mentioned, the modifications received’t assist folks affected by the 2022 breach.
“These folks want to alter all their passwords, one thing that LastPass nonetheless received’t suggest,” Palant mentioned. “However it’ll considerably assist with the breaches to return.”
LastPass CEO Karim Toubba mentioned altering grasp password size (and even the grasp password itself) is just not designed to handle already stolen vaults which are offline.
“That is meant to higher shield clients’ on-line vaults and encourage them to deliver their accounts as much as the 2018 LastPass customary default setting of a 12-character minimal (however may choose out from),” Toubba mentioned in an emailed assertion. “We all know that some clients might have chosen comfort over safety and utilized much less complicated grasp passwords regardless of encouragement to make use of our (or others) password generator to do in any other case.”
A fundamental performance of LastPass is that it’s going to decide and bear in mind prolonged, complicated passwords for every of your web sites or on-line companies. To mechanically populate the suitable credentials at any web site going ahead, you merely authenticate to LastPass utilizing your grasp password.
LastPass has all the time emphasised that in the event you lose this grasp password, that’s too dangerous as a result of they don’t retailer it and their encryption is so sturdy that even they’ll’t show you how to get better it.
However specialists say all bets are off when cybercrooks can get their arms on the encrypted vault information itself — versus having to work together with LastPass by way of its web site. These so-called “offline” assaults enable the dangerous guys to conduct limitless and unfettered “brute drive” password cracking makes an attempt towards the encrypted information utilizing highly effective computer systems that may every strive tens of millions of password guesses per second.
A chart on Palant’s weblog submit presents an thought of how growing password iterations dramatically will increase the prices and time wanted by the attackers to crack somebody’s grasp password. Palant mentioned it could take a single high-powered graphics card a couple of 12 months to crack a password of common complexity with 500 iterations, and about 10 years to crack the identical password run by way of 5,000 iterations.
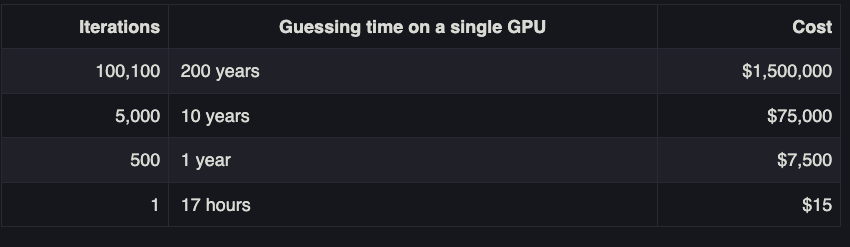
Picture: palant.data
Nevertheless, these numbers radically come down when a decided adversary additionally has different large-scale computational property at their disposal, similar to a bitcoin mining operation that may coordinate the password-cracking exercise throughout a number of highly effective programs concurrently.
Which means, LastPass customers whose vaults have been by no means upgraded to larger iterations and whose grasp passwords have been weak (lower than 12 characters) seemingly have been a major goal of distributed password-cracking assaults ever because the LastPass person vaults have been stolen late final 12 months.
Requested why some LastPass customers have been left behind on older safety minimums, Toubba mentioned a “small share” of shoppers had corrupted objects of their password vaults that prevented these accounts from correctly upgrading to the brand new necessities and settings.
“We’ve been in a position to decide {that a} small share of shoppers have objects of their vaults which are corrupt and after we beforehand utilized automated scripts designed to re-encrypt vaults when the grasp password or iteration rely is modified, they didn’t full,” Toubba mentioned. “These errors weren’t initially obvious as a part of these efforts and, as we’ve found them, we’ve been working to have the ability to treatment this and end the re-encryption.”
Nicholas Weaver, a researcher at College of California, Berkeley’s Worldwide Pc Science Institute (ICSI) and lecturer at UC Davis, mentioned LastPass made an enormous mistake years in the past by not force-upgrading the iteration rely for present customers.
“And now that is blaming the customers — ‘it is best to have used an extended passphrase’ — not them for having weak defaults that have been by no means upgraded for present customers,” Weaver mentioned. “LastPass in my guide is one step above snake-oil. I was, ‘Choose whichever password supervisor you need,’ however now I’m very a lot, ‘Choose any password supervisor however LastPass.’”
Requested why LastPass isn’t recommending that customers change the entire passwords secured by the encrypted grasp password that was stolen when the corporate obtained hacked final 12 months, Toubba mentioned it’s as a result of “the information demonstrates that almost all of our clients observe our suggestions (or larger), and the chance of efficiently brute forcing vault encryption is enormously decreased accordingly.”
“We’ve been telling clients since December of 2022 that they need to be following advisable tips,” Toubba continued. “And in the event that they haven’t adopted the rules we advisable that they modify their downstream passwords.”
