The sufferer shaming web site operated by the cybercriminals behind 8Base — presently one of many extra energetic ransomware teams — was till earlier at this time leaking fairly a bit of data that the crime group in all probability didn’t intend to be made public. The leaked information means that no less than a few of web site’s code was written by a 36-year-old programmer residing within the capital metropolis of Moldova.

The 8Base ransomware group’s sufferer shaming web site on the darknet.
8Base maintains a darknet web site that’s solely reachable through Tor, a freely obtainable world anonymity community. The location lists a whole lot of sufferer organizations and corporations — all allegedly hacking victims that refused to pay a ransom to maintain their stolen information from being printed.
The 8Base darknet web site additionally has a built-in chat function, presumably in order that 8Base victims can talk and negotiate with their extortionists. This chat function, which runs on the Laravel internet software framework, works tremendous so long as you’re *sending* data to the location (i.e., by making a “POST” request).
Nevertheless, if one had been to attempt to fetch information from the identical chat service (i.e., by making a “GET” request), the web site till fairly lately generated an especially verbose error message:
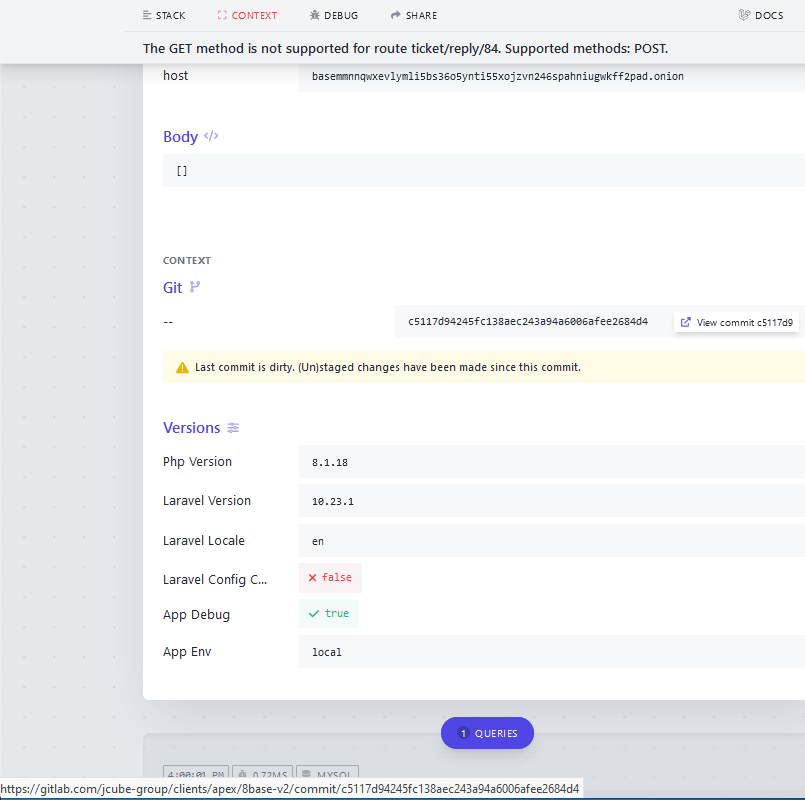
The verbose error message when one tries to tug information from 8Base’s darknet web site. Discover the hyperlink on the backside of this picture, which is generated when one hovers over the “View commit” message underneath the “Git” heading.
That error web page revealed the true Web handle of the Tor hidden service that homes the 8Base web site: 95.216.51[.]74, which in keeping with DomainTools.com is a server in Finland that’s tied to the Germany-based internet hosting big Hetzner.
However that’s not the attention-grabbing half: Scrolling down the prolonged error message, we are able to see a hyperlink to a personal Gitlab server referred to as Jcube-group: gitlab[.]com/jcube-group/shoppers/apex/8base-v2. Digging additional into this Gitlab account, we are able to discover some curious information factors obtainable within the JCube Group’s public code repository.
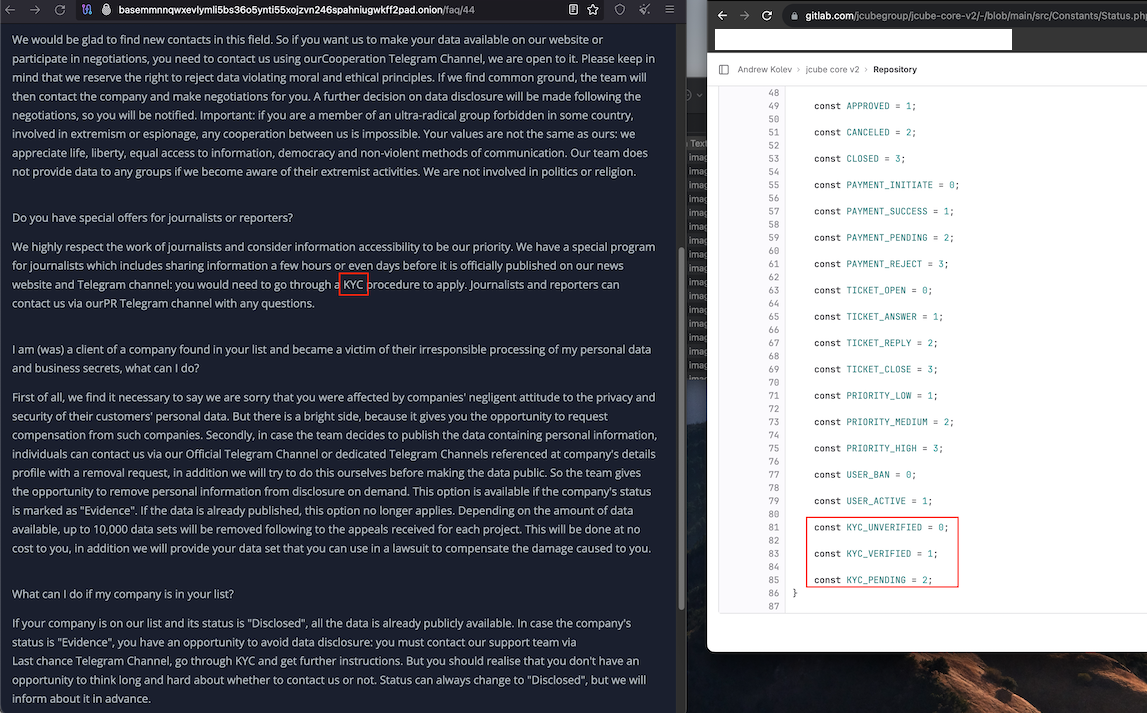
For instance, this “standing.php” web page, which was dedicated to JCube Group’s Gitlab repository roughly one month in the past, consists of code that makes a number of mentions of the time period “KYC” (e.g. KYC_UNVERIFIED, KYC_VERIFIED, and KYC_PENDING).
That is curious as a result of a FAQ on the 8Base darknet web site features a part on “particular gives for journalists and reporters,” which says the crime group is open to interviews however that journalists might want to show their id earlier than any interview can happen. The 8base FAQ refers to this vetting course of as “KYC,” which generally stands for “Know Your Buyer.”
“We extremely respect the work of journalists and take into account data to be our precedence,” the 8Base FAQ reads. “We now have a particular program for journalists which incorporates sharing data just a few hours and even days earlier than it’s formally printed on our information web site and Telegram channel: you would want to undergo a KYC process to use. Journalists and reporters can contact us through our PR Telegram channel with any questions.”
The 8Base darknet web site additionally has a publicly accessible “admin” login web page, which options a picture of a industrial passenger airplane parked at what seems to be an airport. Subsequent to the airplane photograph is a message that reads, “Welcome to 8Base. Admin Login to 8Base dashboard.”
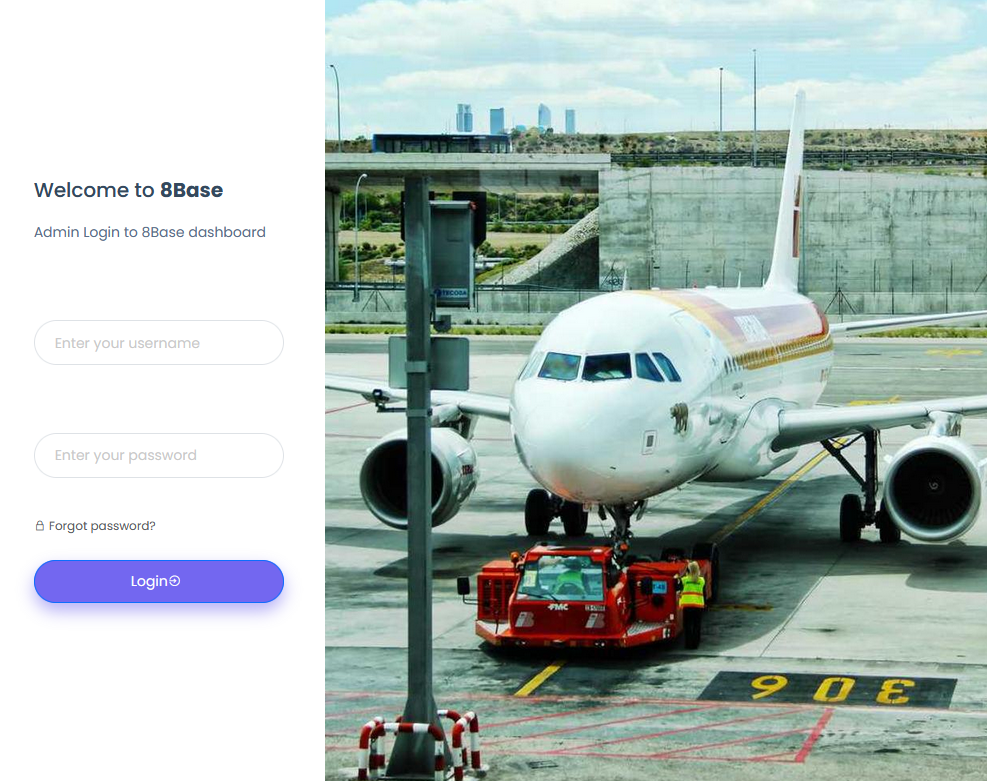
The login web page on the 8Base ransomware group’s darknet web site.
Proper-clicking on the 8Base admin web page and deciding on “View Supply” produces the web page’s HTML code. That code is nearly similar to a “login.blade.php” web page that was authored and dedicated to JCube Group’s Gitlab repository roughly three weeks in the past.
It seems the individual liable for the JCube Group’s code is a 36-year-old developer from Chisinau, Moldova named Andrei Kolev. Mr. Kolev’s LinkedIn web page says he’s a full-stack developer at JCube Group, and that he’s presently in search of work. The homepage for Jcubegroup[.]com lists an handle and telephone quantity that Moldovan enterprise information affirm is tied to Mr. Kolev.
The posts on the Twitter account for Mr. Kolev (@andrewkolev) are all written in Russian, and reference a number of now-defunct on-line companies, together with pluginspro[.]ru.
Reached for remark through LinkedIn, Mr. Kolev mentioned he had no concept why the 8Base darknet web site was pulling code from the “shoppers” listing of his non-public JCube Group Gitlab repository, or how the 8Base identify was even included.
“I [don’t have] a clue, I don’t have that venture in my repo,” Kolev defined. “They [aren’t] my shoppers. Truly we presently have simply our personal tasks.”
Mr. Kolev shared a screenshot of his present tasks, however in a short time after that deleted it. Nevertheless, KrebsOnSecurity captured a duplicate of the picture earlier than it was eliminated:
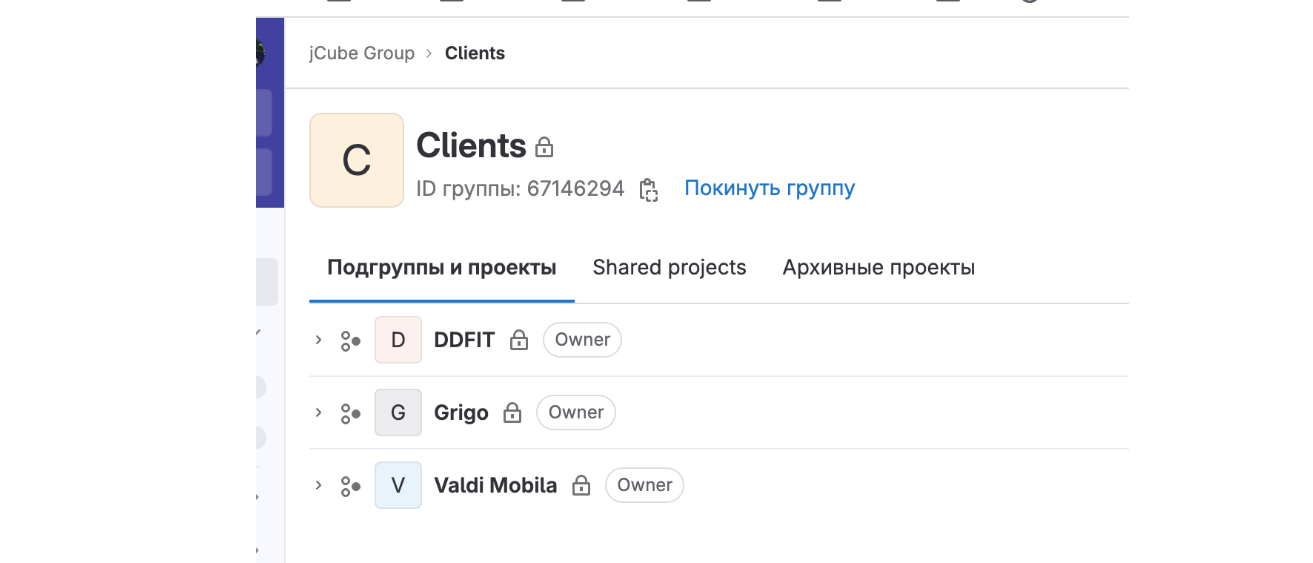
A screenshot of Mr. Kolev’s present tasks that he shortly deleted.
Inside minutes of explaining why I used to be reaching out to Mr. Kolev and strolling him by way of the method of discovering this connection, the 8Base web site was modified, and the error message that linked to the JCube Group non-public Gitlab repository not appeared. As a substitute, attempting the identical “GET” methodology described above prompted the 8Base web site to return a “405 Technique Not Allowed” error web page:
Mr. Kolev claimed he didn’t know something in regards to the now-removed error web page on 8Base’s web site that referenced his non-public Gitlab repo, and mentioned he deleted the screenshot from our LinkedIn chat as a result of it contained non-public data.
Ransomware teams are recognized to remotely rent builders for particular tasks with out disclosing precisely who they’re or how the brand new rent’s code is meant for use, and it’s attainable that one in every of Mr. Kolev’s shoppers is merely a entrance for 8Base. However regardless of 8Base’s assertion that they’re pleased to correspond with journalists, KrebsOnSecurity remains to be ready for a reply from the group through their Telegram channel.
The tip in regards to the leaky 8Base web site was offered by a reader who requested to stay nameless. That reader, a authentic safety skilled and researcher who goes by the deal with @htmalgae on Twitter, mentioned it’s doubtless that whoever developed the 8Base web site inadvertently left it in “improvement mode,” which is what prompted the location to be so verbose with its error messages.
“If 8Base was working the app in manufacturing mode as an alternative of improvement mode, this Tor de-anonymization would have by no means been attainable,” @htmalgae mentioned.
A latest weblog publish from VMware/Carbon Black referred to as the 8Base ransomware group “a heavy hitter” that has remained comparatively unknown regardless of the huge spike in exercise in Summer season of 2023.
“8Base is a Ransomware group that has been energetic since March 2022 with a major spike in exercise in June of 2023,” Carbon Black researchers wrote. “Describing themselves as ‘easy pen testers,’ their leak web site offered sufferer particulars by way of Steadily Requested Questions and Guidelines sections in addition to a number of methods to contact them. ”
In accordance with VMware, what’s notably attention-grabbing about 8Base’s communication fashion is the usage of verbiage that’s strikingly acquainted to a different recognized cybercriminal group: RansomHouse.
“The group makes use of encryption paired with ‘name-and-shame’ strategies to compel their victims to pay their ransoms,” VMware researchers wrote. “8Base has an opportunistic sample of compromise with latest victims spanning throughout diversified industries. Regardless of the excessive quantity of compromises, the knowledge relating to identities, methodology, and underlying motivation behind these incidents nonetheless stays a thriller.”
Replace, Sept. 21, 10:43 a.m. ET: The creator of Databreaches.internet was lurking within the 8Base Telegram channel once I popped in to ask the crime group a query, and experiences that 8Base did finally reply: ““hello in the meanwhile we r not doing interviews. we’ve got nothing to say. we r a little bit busy.”