A number of safety vulnerabilities have been disclosed within the Clever Platform Administration Interface (IPMI) firmware for Supermicro baseboard administration controllers (BMCs) that would lead to privilege escalation and execution of malicious code on affected techniques.
The seven flaws, tracked from CVE-2023-40284 by means of CVE-2023-40290, fluctuate in severity from Excessive to Crucial, based on Binarly, enabling unauthenticated actors to realize root entry to the BMC system. Supermicro has shipped a BMC firmware replace to patch the bugs.
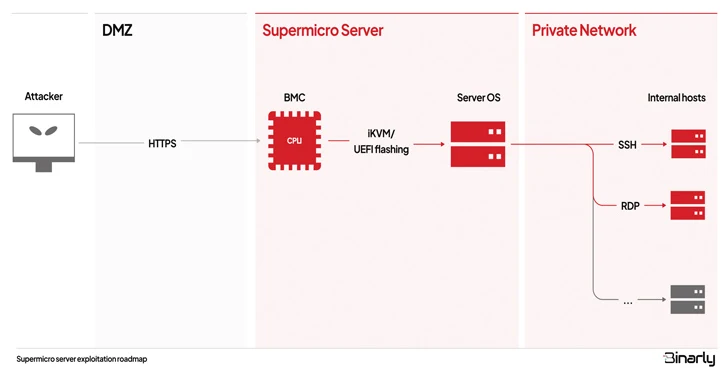
BMCs are particular processors on server motherboards that help distant administration, enabling directors to observe {hardware} indicators comparable to temperature, set fan pace, and replace the UEFI system firmware. What’s extra, BMC chips stay operational even when the host working system is offline, making them profitable assault vectors to deploy persistent malware.
A quick explainer of every of the vulnerabilities is beneath –
- CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288 (CVSS scores: 9.6) – Three cross-site scripting (XSS) flaws that permit distant, unauthenticated attackers to execute arbitrary JavaScript code within the context of the logged-in BMC person.
- CVE-2023-40285 and CVE-2023-40286 (CVSS rating: 8.6) – Two cross-site scripting (XSS) flaws that permit distant, unauthenticated attackers to execute arbitrary JavaScript code within the context of the logged-in BMC person by poisoning browser cookies or native storage.
- CVE-2023-40289 (CVSS rating: 9.1) – An working system command injection flaw that enables for the execution of malicious code as a person with administrative privileges.
- CVE-2023-40290 (CVSS rating: 8.3) – A cross-site scripting (XSS) flaw that enables distant, unauthenticated attackers to execute arbitrary JavaScript code within the context of the logged-in BMC person, however solely when utilizing Web Explorer 11 browser on Home windows.
CVE-2023-40289 is “important as a result of it permits authenticated attackers to realize root entry and utterly compromise the BMC system,” Binarly mentioned in a technical evaluation printed this week.
“This privilege permits to make the assault persistent even whereas the BMC element is rebooted and to maneuver laterally throughout the compromised infrastructure, infecting different endpoints.”
The opposite six vulnerabilities – CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288 specifically – might be used to create an account with admin privileges for the net server element of the BMC IPMI software program.
Consequently, a distant attacker trying to take management of the servers may mix them with CVE-2023-40289 to carry out command injection and obtain code execution. In a hypothetical situation, this might play within the type of sending a phishing e mail bearing a booby-trapped hyperlink to the administrator’s e mail tackle that, when clicked, triggers the execution of the XSS payload.
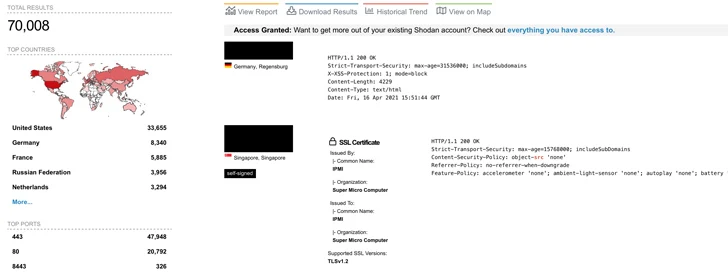
There may be presently no proof of any malicious exploitation of the vulnerabilities within the wild, though Binarly mentioned it noticed greater than 70,000 situations of internet-exposed Supermicro IPMI internet interfaces initially of October 2023.
“First, it’s doable to remotely compromise the BMC system by exploiting vulnerabilities within the Net Server element uncovered to the web,” the firmware safety firm defined.
“An attacker can then acquire entry to the Server’s working system by way of reliable iKVM distant management BMC performance or by flashing the UEFI of the goal system with malicious firmware that enables persistent management of the host OS. From there, nothing prevents an attacker from lateral motion throughout the inner community, compromising different hosts.”
Earlier this 12 months, two safety flaws have been revealed in AMI MegaRAC BMCs that, if efficiently exploited, may permit menace actors to remotely commandeer weak servers and deploy malware.