James Rodriguez – Senior Specialist, Cybersecurity
Government abstract
Over the previous a number of months, AT&T Managed Detection and Response (MTDR) safety operations middle (SOC) analysts have seen a rise within the utilization of phishing emails containing malicious QR codes. In a latest instance, a buyer that was victimized by a phishing try offered the AT&T analysts with an electronic mail that was circulated to a number of of its inside customers. The analysts reviewed the e-mail and its included attachment, a PDF containing a QR code and an pressing message claiming to be from Microsoft.
When the focused consumer scanned the QR code, they have been directed to a counterfeit Microsoft login web page designed to reap usernames and passwords. This sort of assault known as “quishing.”
Sadly, a number of customers fell sufferer to the assault, and their credentials have been compromised. Nonetheless, our analysts have been capable of interact with the shopper and information them by way of the correct remediation steps.
Encouraging focused customers to behave shortly and scan the code utilizing their cellphone (which regularly shouldn’t be as safe as the remainder of an organization’s community) is an ordinary tactic employed by risk actors. By doing this, they hope to persuade the consumer to behave with out pondering and forgo correct safety practices permitting the risk actor to bypass conventional safety measures in place on an organization community.
Risk actor ways
The risk actor used a Home windows authentication setup for multi-factor authentication (MFA) to provoke the assault. The focused customers obtained a phishing electronic mail indicating MFA wanted to be arrange on their account. The e-mail included a PDF attachment with directions directing them to scan the included QR code, which was malicious.
As soon as the customers scanned the QR code, they have been redirected to a faux Microsoft sign-in web page on their cellphone. Right here, they entered their respectable login credentials,which have been then saved and made obtainable to the risk actor.
Investigation
As soon as the shopper suspected the e-mail was malicious, they contacted the AT&T staff and offered a replica of the PDF file with the included QR code. The staff analyzed the file and the QR code (see Picture 1) and recognized the related vacation spot as “srvc1[.]data/mcrsft2fasetup/index.html.”
Picture 1: PDF file from buyer containing malicious QR code
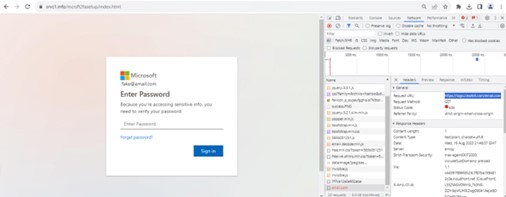
The QR codes related URL sends the consumer to a credential harvester masquerading as a Microsoft login web page. (See Picture 2.)
Picture 2: Credential harvester masquerading as login web page
AT&T SOC analysts analyzed the credential harvester utilizing a faux electronic mail and the Google Chrome Inspector software to file any outbound connections when clicking the “Signal In” button (see Picture 2). Just one community connection was made, which resulted in a 404 HTTP response code to the exterior area “emblem.clearbit[.]com/electronic mail.com.” Analysis into clearbit[.]com discovered it’s related to Clearbit B2B Advertising Intelligence, which is listed as a respectable advertising and marketing software for figuring out prospects and gross sales exchanges.
Analysts used open-source intelligence (OSINT) to additional analysis the preliminary related area “srvc1[.]data” however discovered no extra info because the area was not too long ago bought. Additional investigation revealed that the proprietor’s identification was hidden, and there was no extra information obtainable. The client confirmed that neither the Clearbit nor the srvc1 exterior domains have been identified or part of regular enterprise use inside their surroundings.
Remediation
AT&T SOC analysts labored intently with the shopper to establish which customers had obtained the e-mail and to confirm whether or not any credentials have been submitted on the login web page. Throughout this time, the analysts offered detailed directions to the shopper on the best way to shut all energetic periods and instructing them to reset consumer credentials. Closing all energetic periods previous to any credential resets is essential for the reason that risk actor will retain entry to the consumer’s account till they’re fully logged out.
The client was additionally directed to take away the phishing electronic mail from all consumer inboxes inside their surroundings and to dam all exterior domains related to the QR code. Analysts carried out additional evaluation of the affected consumer accounts to verify that no information had been efficiently exfiltrated and that there have been no different indicators of the e-mail being circulated internally. As soon as the incident had been totally remediated, the shopper was capable of take the teachings discovered to higher inform their groups of the hazards of phishing and malicious QR codes.
Defend your self towards malicious QR codes
Phishing assaults and credential harvesters have been in use for a while. Nonetheless, as using QR codes turns into extra commonplace, take care to confirm the area {that a} QR code is related to earlier than you scan it.
Moreover, keep away from scanning the QR code along with your cell gadget. Sometimes, there are much less safety measures in place on a cell gadget than on a network-connected company gadget.