A vulnerability within the HTTP/2 community protocol is presently being exploited, ensuing within the largest DDoS assault in historical past. Discover out what safety groups ought to do now, and listen to what Cloudflare’s CEO has to say about this DDoS.
Google, AWS and Cloudflare have reported the exploitation of a zero-day vulnerability named HTTP/2 Speedy Reset and tracked as CVE-2023-44487, which is presently used within the wild to run the biggest Distributed Denial of Service assault campaigns ever seen. All organizations or people utilizing servers that present HTTP/2 to the web are susceptible.
Leap to:
What’s HTTP/2?
HTTP/2, often known as HTTP/2.0, is a significant revision of the HTTP community protocol that’s used to switch information between computer systems and net servers. HTTP/2 was developed to make net purposes quicker, in addition to extra environment friendly and safe.
A elementary distinction with HTTP/1.1 resides in its multiplexing capabilities. In HTTP/1.1, a number of connections had been required for parallel communication, resulting in inefficiency and elevated latency. HTTP/2 permits a number of requests and responses to be despatched and acquired in parallel over a single TCP connection.
What’s the HTTP/2 Speedy Reset assault?
The HTTP/2 Speedy Reset assault works by leveraging HTTP/2’s stream cancellation function: The attacker sends a request and cancels it instantly.
Automating that means of sending/canceling at scale results in a DDoS assault, which is what attackers did utilizing a number of bots (Determine A).
Determine A
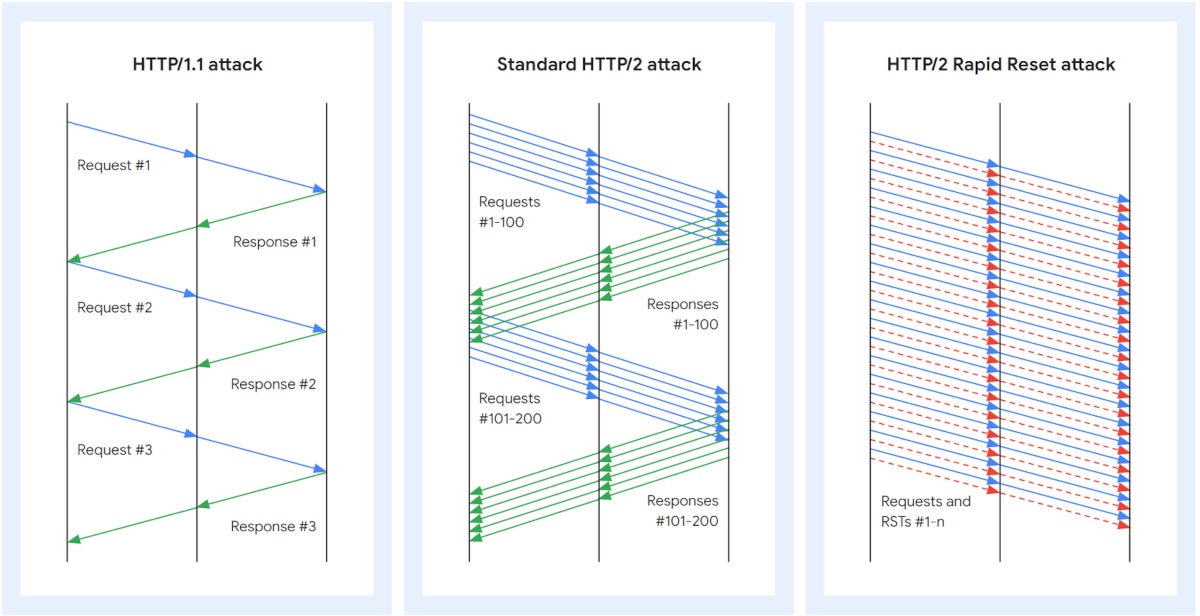
DDoS at unprecedented scale
Amazon noticed and mitigated greater than a dozen HTTP/2 Speedy Reset assaults over two days in late August, the strongest one hitting its infrastructures at 155 million requests per second. Cloudflare reported a peak at 201 million requests per second and mitigated greater than 1,100 different assaults with greater than 10 million RPS, and 184 assaults better than the earlier DDoS document of 71 million RPS.
Google reported the most important assault, which reached a peak of 398 million RPS utilizing the HTTP/2 Speedy Reset approach (Determine B). As acknowledged by Google in its weblog put up concerning the DDoS assault, “For a way of scale, this two minute assault generated extra requests than the whole variety of article views reported by Wikipedia throughout the complete month of September 2023.”
Determine B
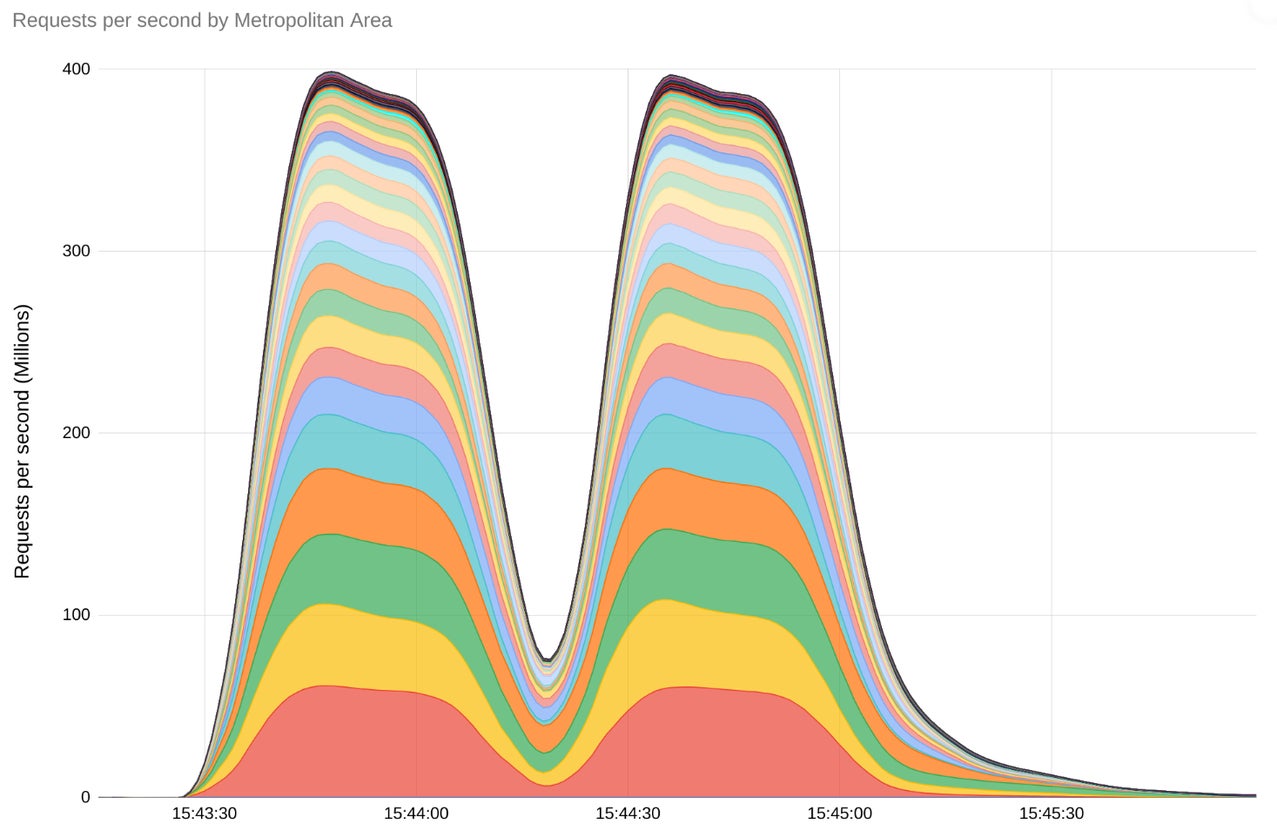
After we requested Cloudflare CEO and co-founder Matthew Prince concerning the variety of bots wanted to launch such assaults, he stated that it wanted, “Between 10,000 – 20,000 nodes within the botnet, which is comparatively small. That’s regarding as a result of botnets in the present day with a whole bunch of hundreds or hundreds of thousands of nodes are frequent. And this assault ought to scale linearly with the variety of nodes within the botnet. It might be doable to generate an assault bigger than the estimated professional visitors quantity of the net (1–3 billion requests per second) however all targeted on a single sufferer. That’s one thing that even the biggest organizations wouldn’t be capable of deal with with out applicable mitigation.”
From one other Cloudflare weblog put up: “As a result of the assault abuses an underlying weak spot within the HTTP/2 protocol, we imagine any vendor that has applied HTTP/2 shall be topic to the assault. This included each trendy net server.”
Cross-industry response coordination
Google coordinated a cross-industry response with different cloud suppliers and software program maintainers who implement the HTTP/2 protocol stack. The coordination allowed intelligence sharing and mitigation methodologies in actual time because the assaults had been ongoing.
Patches and different mitigation strategies emerged from it. From Google’s weblog put up: “The collaboration helped to pave the way in which for in the present day’s coordinated accountable disclosure of the brand new assault methodology and potential susceptibility throughout a large number of frequent open supply and business proxies, software servers, and cargo balancers.”
Find out how to mitigate this HTTP/2 DDoS assault menace
Vendor patches for CVE-2023-44487 can be found and ought to be deployed as quickly as doable. It is usually suggested to make sure that all automation like Terraform builds and pictures are totally patched so older variations of net servers will not be deployed into manufacturing over the safe ones accidentally.
As a final resort, organizations might disable HTTP/2, however that could be a foul thought for companies that want good net efficiency. Prince acknowledged, “For organizations that care about net efficiency, HTTP/2 stays an enormous win over HTTP/1.1. A whole lot of the responsive, app-like net (apps) that buyers have come to count on requires HTTP/2 or HTTP/3. It’s doable to mitigate this assault vector and nonetheless get the advantages of a contemporary net protocol. So, for many companies, turning off HTTP/2 ought to solely be a final choice.”

