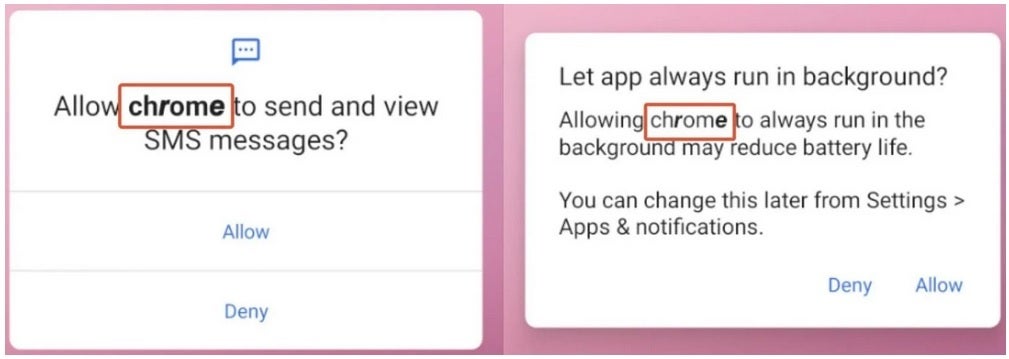
Faux permission requests are made to seem like they’re coming from Google Chrome
McAfee says, “Whereas the app is put in, their malicious exercise begins routinely. We’ve already reported this method to Google and they’re already engaged on the implementation of mitigations to stop one of these auto-execution in a future Android model.”
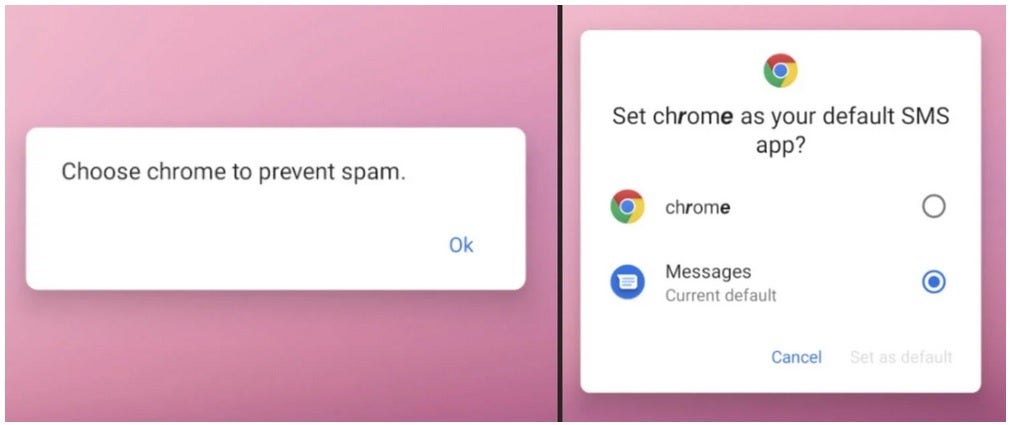
One other pretend request for permission
The malicious apps ship out permission requests pretending to come back from Google Chrome requesting permission to ship and think about SMS (textual content) messages and asking permission to maintain “Chrome” working within the background. And the coup de grace is permission to make “Chrome” your default SMS app. The malware, as soon as it will get all of those permissions, is used to ship images, textual content messages, contact lists, and data on the {hardware} you might be utilizing (together with your telephone’s distinctive IMEI quantity) to the management server. Sure, it is extremely scary.
McAfee says that since minimal interplay is required by the sufferer, the brand new XLoader malware is much more harmful than its predecessor. There may be some excellent news. An replace from McAfee dated a few weeks in the past says that Android units with Google Play Providers are shielded from assaults from this sort of malware by Google Play Defend which is enabled by default.
Nonetheless, there are some takeaways to contemplate right here. By no means click on on a shortened URL present in a message. And by no means sideload an app.

