
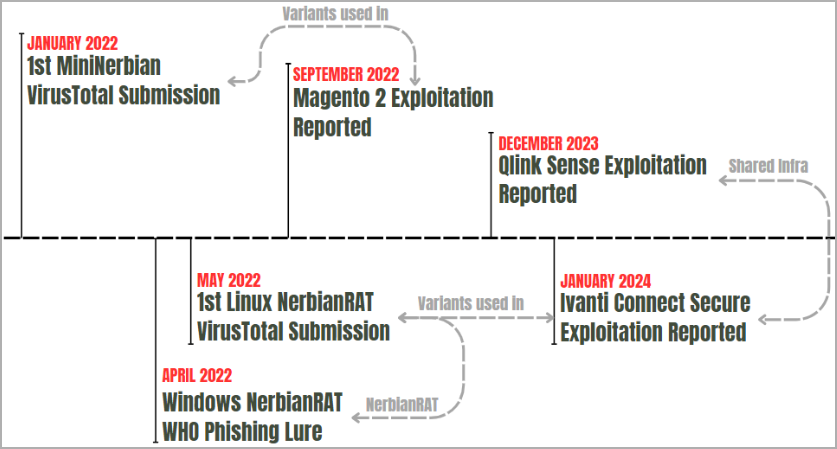
A financially motivated hacking group named Magnet Goblin makes use of numerous 1-day vulnerabilities to breach public-facing servers and deploy customized malware on Home windows and Linux techniques.
1-day flaws check with publicly disclosed vulnerabilities for which a patch has been launched. Risk actors trying to exploit these flaws should accomplish that rapidly earlier than a goal can apply safety updates.
Although exploits are normally not made obtainable instantly upon a flaw’s disclosure, some vulnerabilities are trivial to determine learn how to leverage. Moreover, reverse-engineering the patch could reveal the underlying downside and learn how to exploit it.
Test Level analysts who recognized Magnet Goblin report that these risk actors are fast to use newly disclosed vulnerabilities, in some circumstances exploiting flaws a day after a PoC exploit is launched.
A few of the units or providers focused by the hackers are Ivanti Join Safe (CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, CVE-2024-21893., Apache ActiveMQ, ConnectWise ScreenConnect, Qlik Sense (CVE-2023-41265, CVE-2023-41266, CVE-2023-48365), and Magento (CVE-2022-24086).
Magnet Goblin exploits the issues to contaminate servers with customized malware, notably NerbianRAT and MiniNerbian, in addition to a customized variant of the WARPWIRE JavaScript stealer.
Supply: Test Level
Customized Linux malware
NerbianRAT for Home windows has been identified since 2022, however Test Level now reviews {that a} sloppily compiled but efficient Linux variant utilized by Magnet Goblin has been in circulation since Could 2022.
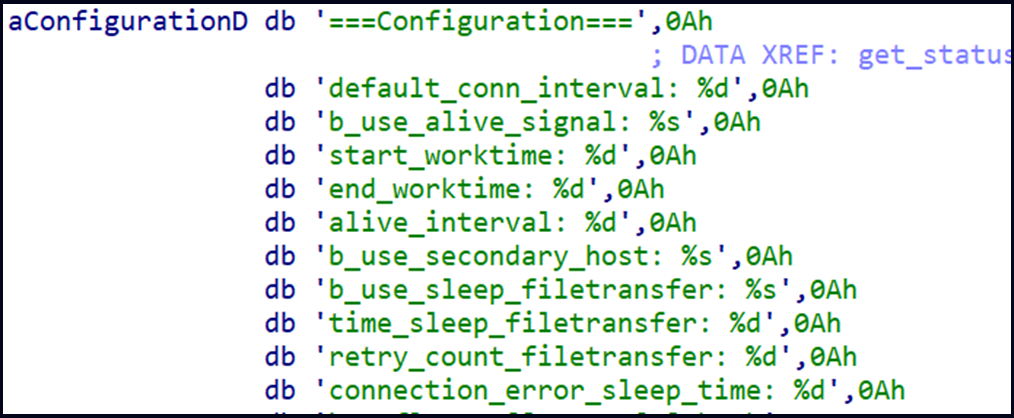
Upon first launch, the malware performs preliminary actions, together with the gathering of system information similar to time, username, and machine identify, technology of a bot ID, setting a hardcoded IP deal with as main and secondary host, setting the working listing, and loading a public RSA key for encrypting (AES) community communication.
After that, NerbianRAT hundreds its configuration, which determines exercise instances (worktime), time intervals for speaking with the command and management (C2) server, and different parameters.
Supply: Test Level
The C2 could ship one of many following actions to the malware for execution on the contaminated system:
- Request extra actions
- Execute a Linux command in a brand new thread
- Ship command outcome and clear the file; cease any operating instructions
- Execute a Linux command instantly
- Do nothing
- Modify connection interval
- Regulate and save worktime settings
- Return idle timings, config, or command outcomes
- Replace a particular config variable
- Refresh command buffer for C2 execution instructions
The MiniNerbian is a simplified model of the NerbianRAT, which is primarily used for command execution and helps the next actions:
- Execute C2’s command and return outcomes
- Replace exercise schedule (full day or particular hours)
- Replace configuration
MiniNerbian communicates with the C2 by way of HTTP, differentiating it from the extra complicated NerbianRAT, which makes use of uncooked TCP sockets for communication.
Presumably, Magnet Goblin makes use of it for redundancy or as a stealthier backdoor in some circumstances.
Supply: Test Level
Test Level says figuring out particular threats like Magnet Goblin’s assaults among the many sheer quantity of 1-day exploitation information is difficult, permitting these teams to cover in plain sight within the chaos that follows the disclosure of flaws.
Patching rapidly is crucial in beating 1-day exploitation, whereas further measures similar to community segmentation, endpoint safety, and multi-factor authentication can assist mitigate the affect of potential breaches.
