Cybercrime impacts individuals from all walks of life, but it surely hits small companies the toughest. Whereas cyberattacks on massive firms and authorities companies get a majority of the information protection, small companies (broadly talking, organizations with lower than 500 staff) are typically extra weak to cybercriminals and endure extra proportionally from the outcomes of cyberattacks. An absence of skilled safety operations workers, underinvestment in cybersecurity, and smaller info expertise budgets general are contributing elements to this degree of vulnerability. And when they’re hit by cyberattacks, the expense of restoration might even drive many small companies to shut.
Small companies will not be a small matter. In keeping with the World Financial institution, greater than 90% of the world’s companies are small- and medium-sized organizations, and so they account for greater than 50% of employment worldwide. In the USA, small and medium companies account for over 40% of general financial exercise. (On this report, we are going to use the phrases small- and medium-sized companies or organizations interchangeably, reflecting their similarity in our information.)
In 2023, over 75% of buyer incident response circumstances dealt with by Sophos’ X-Ops Incident Response service had been for small companies. Information collected from these circumstances, along with telemetry collected from clients of our small- and medium-sized enterprise safety software program, offers us additional distinctive perception into the threats which might be concentrating on these organizations day by day.
Based mostly on that information and Sophos menace analysis, we see that ransomware continues to have the best impression on smaller organizations. However different threats additionally pose an existential menace to small companies:
- Information theft is the main focus of most malware concentrating on small and medium companies—password stealers, keyboard loggers, and different spyware and adware made up practically half of malware detections. Credential theft by way of phishing and malware can expose small companies’ information on cloud platforms and repair suppliers, and community breaches can be utilized to focus on their clients as nicely
- Attackers have stepped up using web-based malware distribution—by way of malvertising or malicious SEO (“search engine optimisation poisoning”)—to beat difficulties created by the blocking of malicious macros in paperwork, along with utilizing disk pictures to overwhelm malware detection instruments
- Unprotected units linked to organizations’ networks—together with unmanaged computer systems with out safety software program put in, improperly configured computer systems and techniques operating software program fallen out of assist by producers—are a main level of entry for all sorts of cybercrime assaults on small companies
- Attackers have turned more and more to abuse of drivers—both weak drivers from reputable firms or malicious drivers which have been signed with stolen or fraudulently obtained certificates—to evade and disable malware defenses on managed techniques
- E mail assaults have begun to maneuver away from easy social engineering towards extra energetic engagement with targets over e-mail, utilizing a thread of emails and responses to make their lures extra convincing
- Assaults on cellular gadget customers, together with social engineering-based scams tied to the abuse of third-party companies and social media platforms, have grown exponentially, affecting people and small companies. These vary from enterprise e-mail and cloud service compromise to pig butchering (shā zhū pán (殺豬盤)) scams.
A phrase about our information
The info utilized in our evaluation comes from the next sources:
- Buyer reviews—detection telemetry from Sophos safety software program operating on clients’ networks, which supplies a broad view of threats encountered, and analyzed inside SophosLabs (on this report, known as the Labs dataset);
- Managed Detection and Response (MDR) incident information, gathered in the midst of escalations pushed by detection of malicious exercise on MDR clients’ networks (on this report, known as the MDR dataset);
- Incident Response crew information, drawn from incidents on buyer networks for enterprise of 500 staff or fewer the place there was little or no managed detection and response safety in place (on this report, known as the IR dataset).
For a deeper have a look at information drawn strictly from the circumstances dealt with by our external-facing IR crew (together with circumstances involving clients with greater than 500 staff), please see our sister publication, the Energetic Adversary Report (AAR). The conclusions on this report are primarily based, until in any other case acknowledged, on the mixed datasets with acceptable normalization.
Information is the prime goal
The best cybersecurity problem dealing with small companies—and organizations of all sizes—is information safety. Greater than 90% of assaults reported by our clients contain information or credential theft in a technique or one other, whether or not the tactic is a ransomware assault, information extortion, unauthorized distant entry, or just information theft.
Enterprise e-mail compromise (BEC), by which e-mail accounts are taken over by a cybercriminal for the aim of fraud or different malicious functions, is a considerable drawback within the small-to-medium enterprise set. We don’t presently cowl BEC in our sister publication, the Energetic Adversary Report, however the authors of the AAR estimate that in 2023, enterprise e-mail compromises had been recognized by our Incident Response crew extra typically than every other sort of incident, save ransomware.
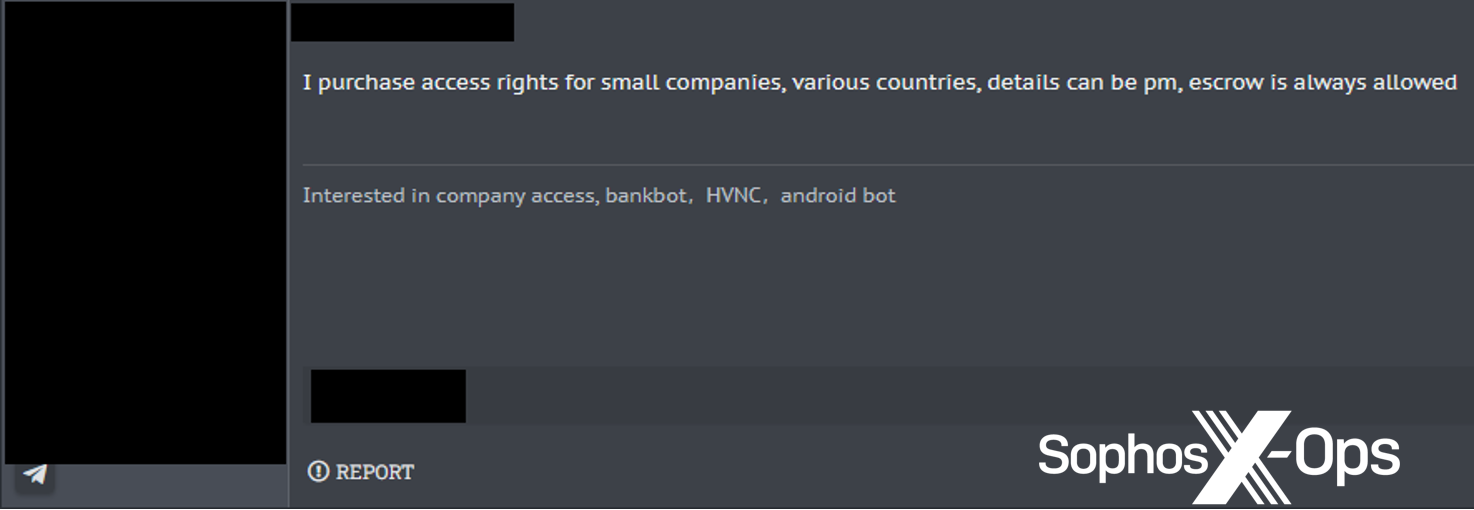
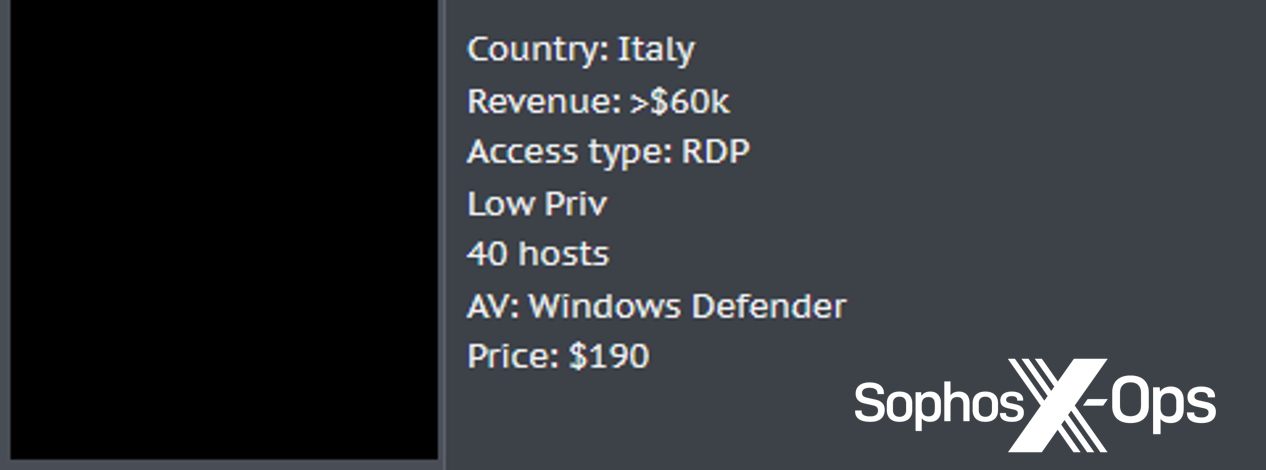
Stolen credentials, together with browser cookies, can be utilized for enterprise e-mail compromise, entry to third-party companies resembling cloud-based finance techniques, and entry to inside sources that may be exploited for fraud or different financial acquire. They will also be offered by “entry brokers” to anybody who cares to take advantage of them; Sophos has tracked presents on underground boards claiming to supply entry to plenty of small and medium companies’ networks.
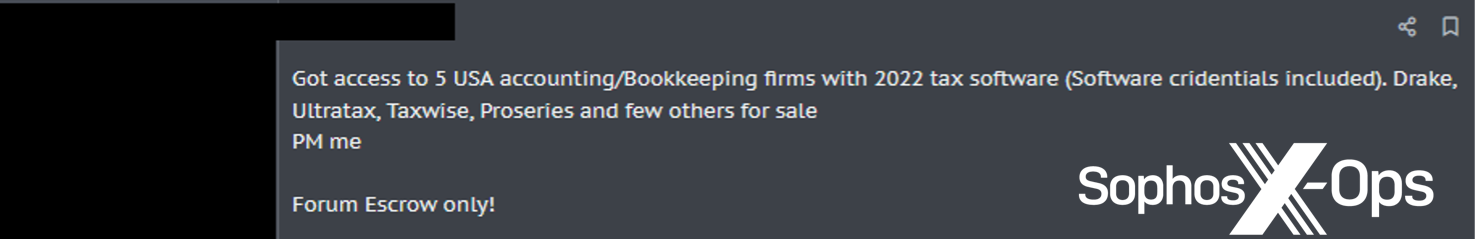
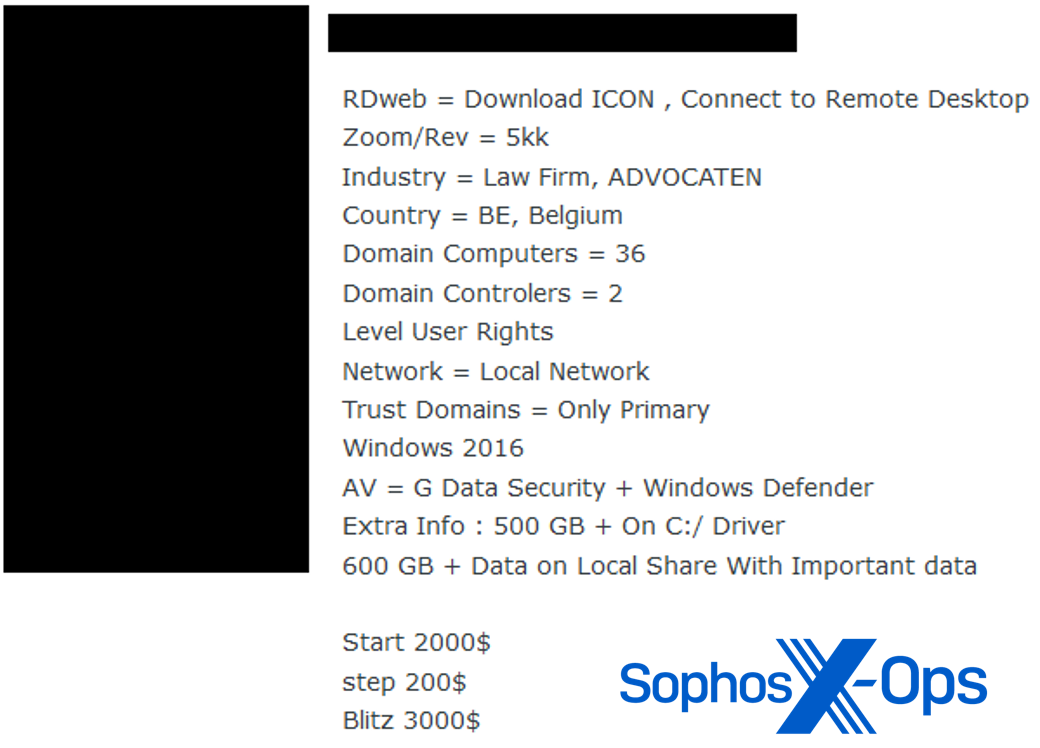
Determine 3: A cybercriminal providing to buy entry to small firms
By class, practically half of malware detected in 2023 focused the information of its meant victims. Nearly all of that’s malware we’ve categorized particularly as “stealers”—malware that grabs credentials, browser cookies, keystrokes, and different information that may be both changed into money as offered entry or used for additional exploitation.
Due to the modular nature of malware, nevertheless, it’s tough to utterly categorize malware by performance—practically all malware has the flexibility to steal some type of information from focused techniques. These detections additionally don’t embrace different credential theft strategies, resembling phishing by way of e-mail, textual content message, and different social engineering assaults. After which there are different targets, resembling macOS and cellular units, the place malware, probably undesirable functions, and social engineering assaults goal customers’ information—particularly of the monetary form.
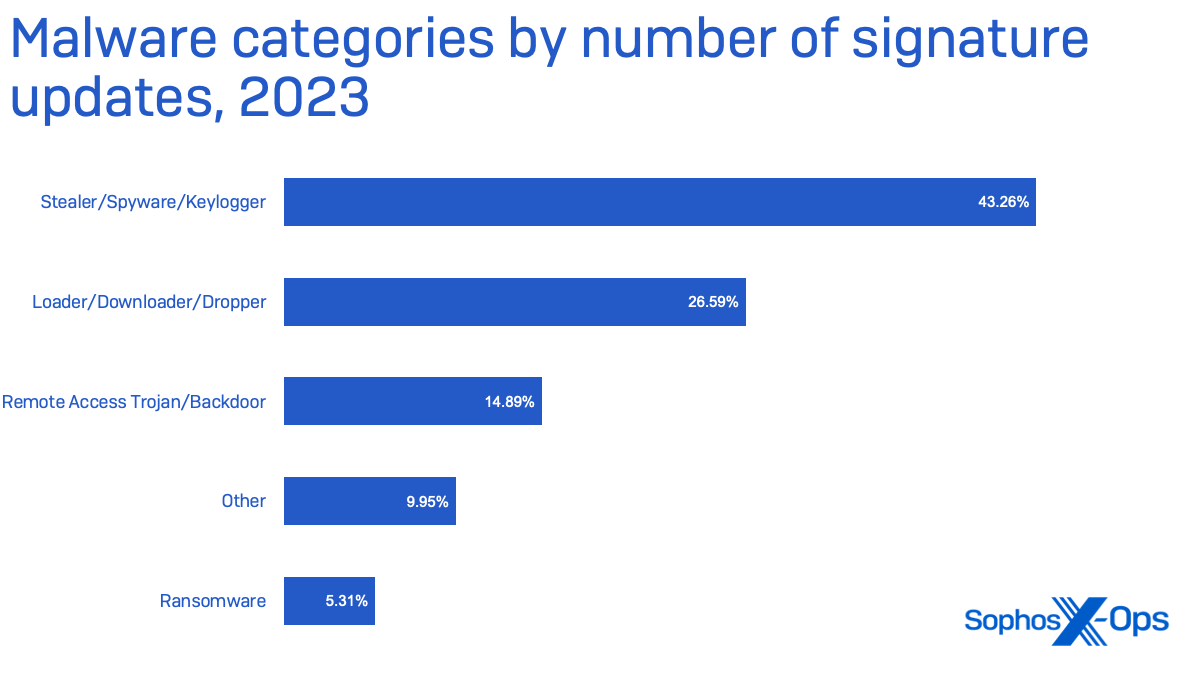
Practically 10% of malware detected falls exterior of the 4 main classes proven above. This “different” class contains malware that targets browsers to inject ads, redirect search outcomes to earn money for clicks, or in any other case modifies or collects information for the revenue of the malware developer, amongst different issues.
Some stealers are very particular of their concentrating on. Discord “token” stealers, meant to steal Discord messaging service credentials, are sometimes leveraged to ship different malware by way of chat servers or by way of Discord’s content material supply community. However different main stealers—Strela, Raccoon Stealer, and the venerable RedLine stealer household—are way more aggressive of their concentrating on, amassing password shops from the working system and functions in addition to browser cookies and different credential information. Raccoon Stealer has additionally deployed cryptocurrency “clippers” which swap crypto pockets addresses copied to the clipboard with a pockets tackle managed by the malware operator.
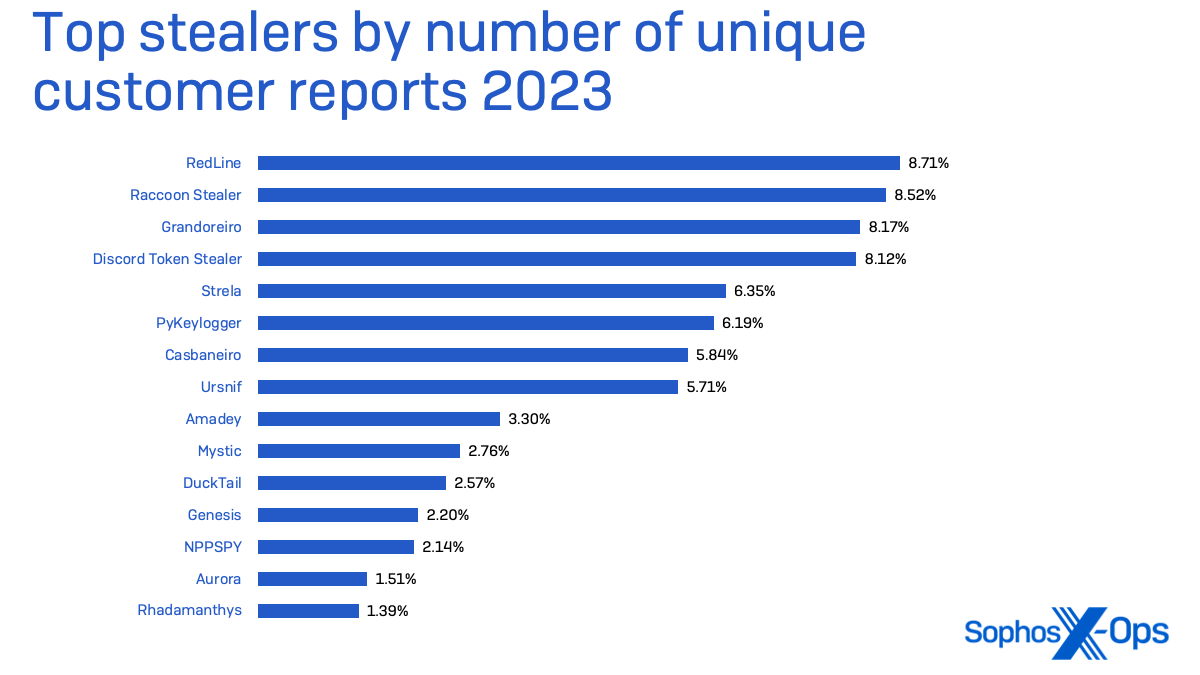
Sophos has seen a rise within the variety of information-stealing malware concentrating on macOS, and we imagine that pattern will proceed. These stealers—a few of that are offered in underground boards and Telegram channels for as much as $3,000— can gather system information, browser information, and cryptowallets.
Ransomware stays a prime menace for small companies
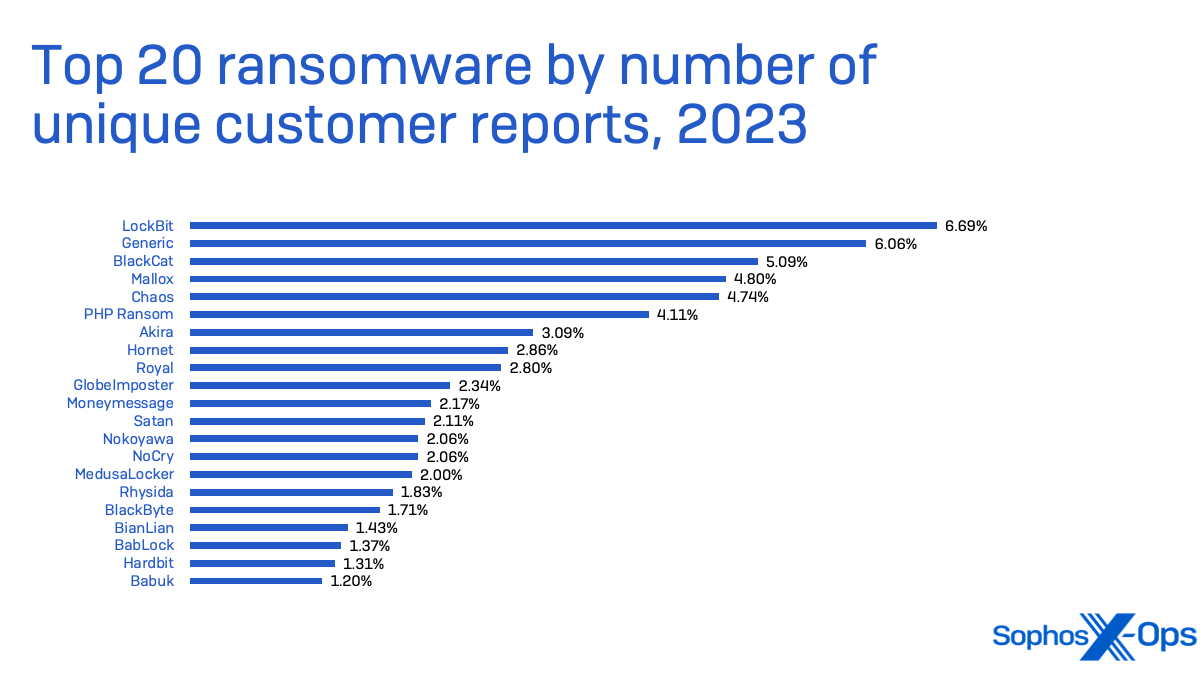
Whereas ransomware makes up a comparatively small proportion of general malware detections, it nonetheless packs the most important punch by way of impression. Ransomware impacts all sizes of companies throughout all sectors, however now we have seen it hit small- and medium-sized enterprises probably the most regularly. In 2021, the Institute for Safety and Expertise’s Ransomware Job Pressure discovered that 70% of ransomware assaults focused small companies. Whereas the general variety of ransomware assaults has various 12 months over 12 months, that proportion bears out in our personal metrics.
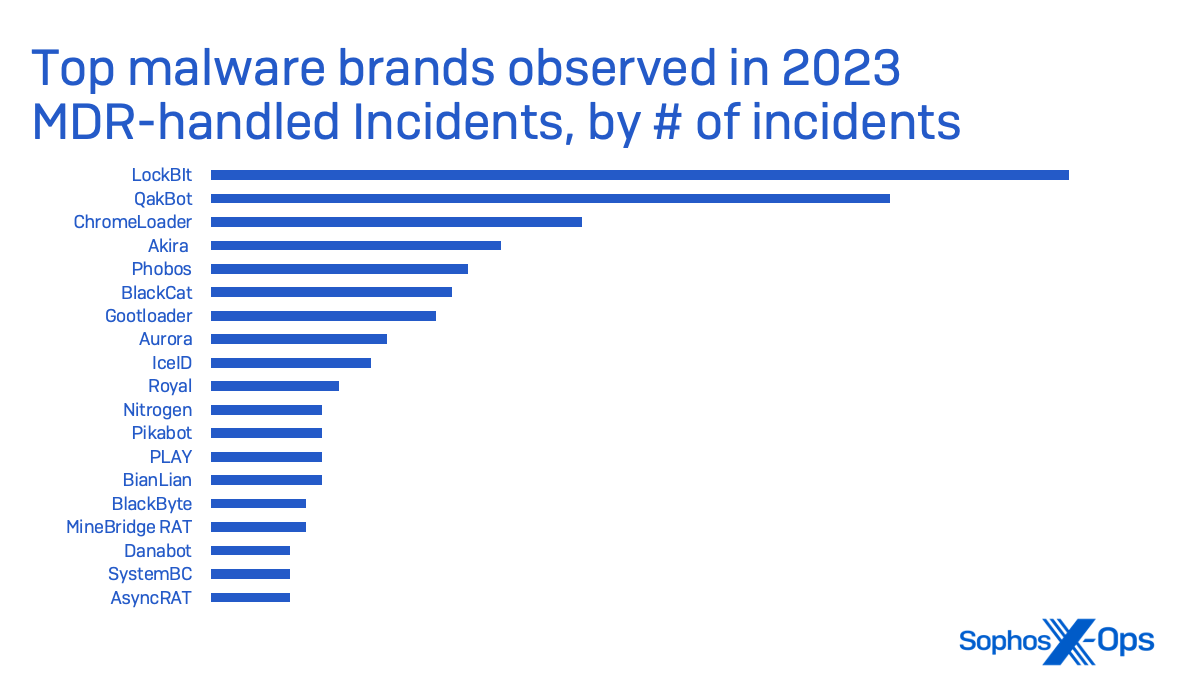
LockBit ransomware was the highest menace in small enterprise safety circumstances taken on by Sophos Incident Response in 2023. LockBit is a ransomware-as-a-service, delivered by plenty of associates, and was probably the most deployed ransomware of 2022 in line with Determine 7.
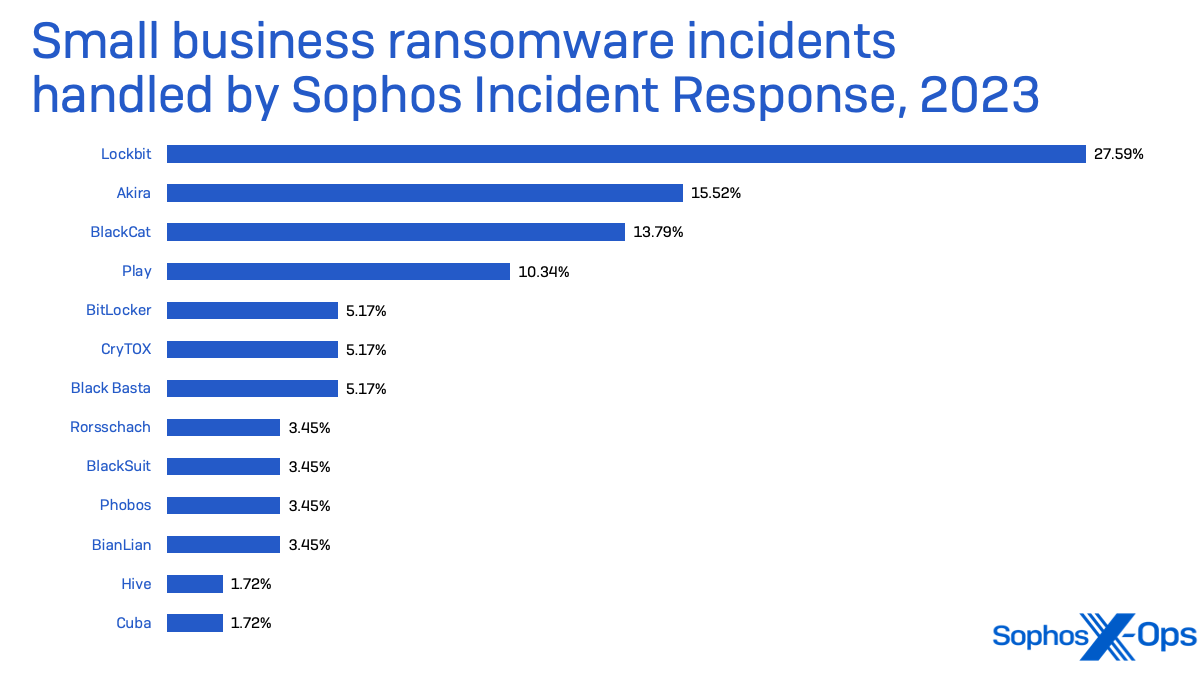
LockBit was the malware noticed probably the most by Sophos’ Managed Detection and Response (MDR) group (which incorporates the Incident Response crew and its information)—with practically thrice the variety of incidents by which ransomware deployment was tried than its nearest peer, Akira.
As 2023 progressed, we noticed a rise in using distant execution of ransomware—utilizing an unmanaged gadget on organizations’ networks to aim to encrypt information on different techniques by way of community file entry.
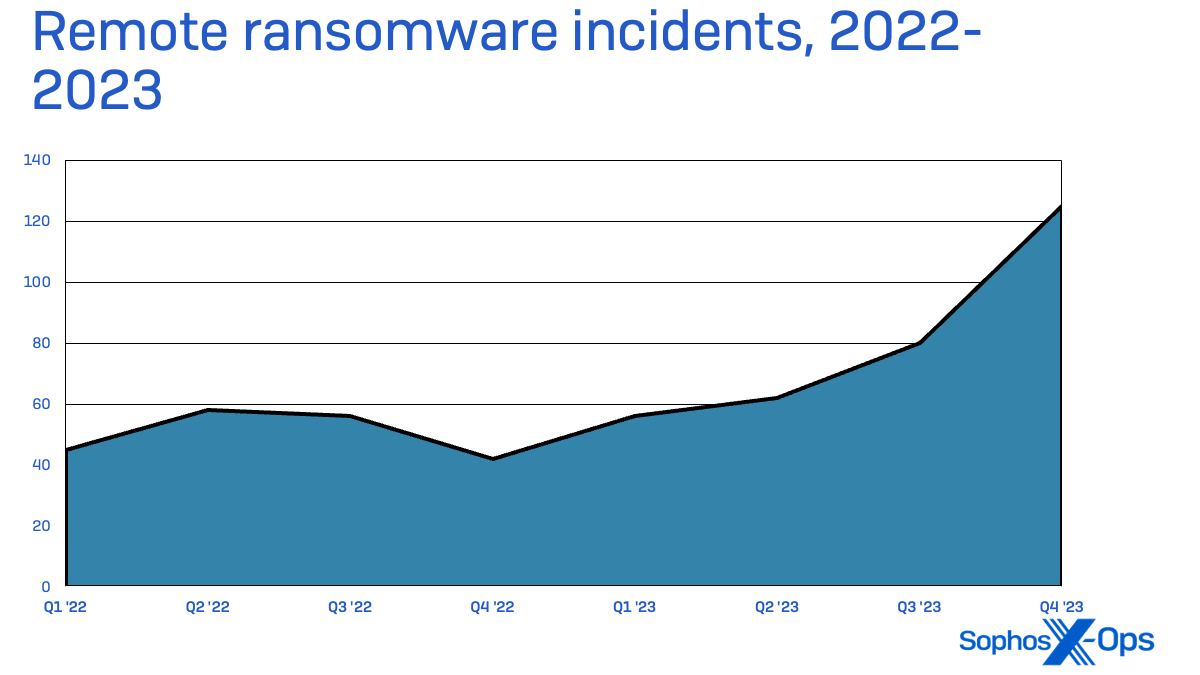
Some of these assaults are in a position to acquire footholds by exploitation of unprotected servers, private units, and community home equipment that connect with organizations’ Home windows-based networks. Protection in depth can forestall these assaults from taking total organizations offline, however they’ll nonetheless go away organizations weak to information loss and theft.
Home windows techniques aren’t the one ones focused by ransomware. More and more, ransomware and different malware builders are utilizing cross-platform languages to construct variations for macOS and Linux working techniques and supported {hardware} platforms. In February of 2023, a Linux variant of Cl0p ransomware was found to have been utilized in a December 2022 assault; since then, Sophos has noticed leaked variations of LockBit ransomware concentrating on macOS on Apple’s personal processor and Linux on a number of {hardware} platforms.
Cybercrime as a service
The malware world continues to be dominated by what we’ve known as “Malware as a Service” (MaaS)—using malware supply frameworks supplied by cybercriminals by way of underground marketplaces to different cybercriminals. However a mixture of enhancements in platform safety and takedown operations by business and legislation enforcement have had some impression on the form of the MaaS panorama.
After a decade of dominance within the malware supply enterprise, Emotet has receded since being taken down by Europol and Eurojust in January 2021. So, to a lesser diploma, have Qakbot and Trickbot, after being disrupted by legislation enforcement in August 2023. Whereas Qakbot has returned in some restricted type, it has been largely supplanted by its would-be successors, Pikabot and DarkGate.
None of this has impacted the venerable distant entry trojan AgentTesla, which has moved to the highest of the MaaS market. It was the malware most frequently detected by endpoint safety in 2023 general in endpoint (apart from generic malicious .LNK information and obfuscated malware), and made up 51% of the malware supply framework detections in our telemetry final 12 months.
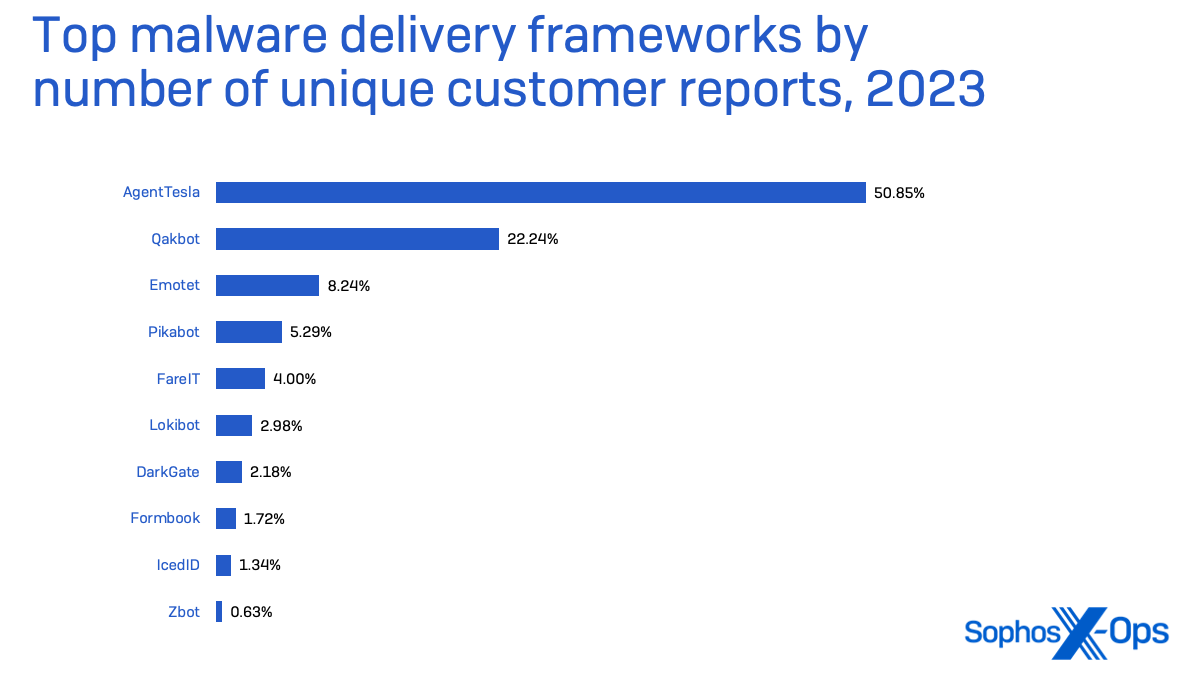
Discovering a unique supply route
Malware assaults require some type of preliminary entry. Sometimes, that entails one of many following:
- Phishing emails
- Malicious e-mail attachments
- Exploits of vulnerabilities in working techniques and functions
- Pretend software program updates
- Exploitation and abuse of Distant Desktop Protocol
- Credential theft
MaaS operators have previously been largely reliant on malicious e-mail attachments for that preliminary foothold. However adjustments to the default safety of the Microsoft Workplace platform have had an impression on the MaaS market. As Microsoft has rolled out adjustments to Workplace functions that block by default Visible Fundamental for Functions (VBA) macros in paperwork downloaded from the Web, it has develop into harder for MaaS operators to make use of their favored technique of spreading malware.
That has led to some adjustments within the forms of file attachments attackers use—attackers have moved to PDF file attachments virtually solely. Nevertheless, there have been some notable exceptions. In early 2023, Qakbot operators turned to utilizing malicious OneNote paperwork to get round adjustments being pushed out to Excel and Phrase, concealing inside the doc hyperlinks to script information that had been activated when the goal clicked on a button inside the OneNote pocket book file.
In 2021, we famous that “malware-as-a-service” choices such because the RaccoonStealer backdoor had begun to rely closely on net supply, typically utilizing SEO (search engine optimisation) tips to idiot targets into downloading their malware. In 2022, we noticed “search engine optimisation poisoning” used as a part of a SolarMarker info stealer marketing campaign. These strategies are on the rise once more, and the actors behind them have grown extra refined.
We noticed a number of notable campaigns utilizing malicious online advertising and search engine optimisation poisoning to focus on victims. One among these was by an exercise group utilizing malware we dubbed “Nitrogen”; the group used Google and Bing ads tied to particular key phrases to lure targets into downloading a software program installer from a faux web site, utilizing a reputable software program developer’s model identification. The identical malvertising approach has been utilized in reference to plenty of different preliminary entry malware, together with the Pikabot botnet agent, IcedID info stealer, and Gozi backdoor malware households.
Within the case of Nitrogen, the advertisements focused IT generalists, providing downloads together with well-known distant desktop software program for end-user assist and safe file switch utilities. The installers carried what was marketed, however in addition they delivered a malicious Python payload that, when launched by the installer, pulled down a Meterpreter distant shell and Cobalt Strike beacons. Based mostly on different researchers’ findings, this was doubtless step one in a BlackCat ransomware assault.
“Twin use” instruments
Cobalt Strike, the well-worn “adversary simulation and pink crew operations” software program equipment, continues for use by precise adversaries in addition to reputable safety testing organizations. However it’s in no way the one commercially developed software program utilized by attackers—and it’s now not the commonest.
Distant desktop instruments, file compression instruments, frequent file switch software program, different utilities, and open-source safety testing instruments are generally utilized by attackers for a similar purpose that they’re utilized by small and medium enterprises—to make their jobs simpler.
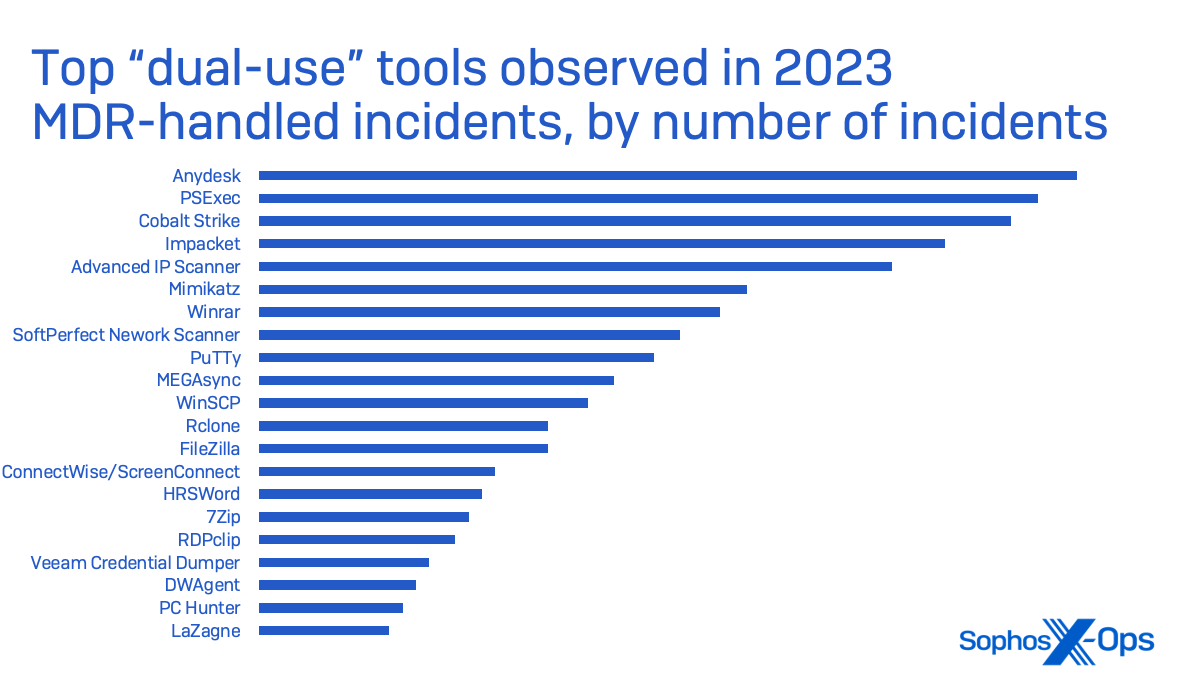
Sophos MDR has noticed these utilities, which we seek advice from as “dual-use instruments”, abused as a part of the post-exploitation course of by attackers:
- Discovery: Superior IP Scanner, NetScan, PCHunter, HRSword
- Persistence: Anydesk, ScreenConnect, DWAgent
- Credential Entry: Mimikatz, Veeam Credential Dumper, LaZagne
- Lateral Motion: PsExec, Impacket, PuTTy
- Information Assortment & Exfil: FileZilla, winscp, megasync, Rclone, WinRar, 7zip
AnyDesk and PsExec had been each seen in additional incidents by Sophos MDR than was Cobalt Strike, as seen under:
Zero-day assaults and nonzero-day assaults
In Might 2023, Progress Software program reported vulnerabilities within the firm’s extensively used safe managed file switch platform, MOVEit—together with one which had been exploited by a minimum of one set of malicious actors. Subsequently the corporate would reveal a number of extra vulnerabilities and challenge a number of patches to repair them.
The assaults had been attributed to actors related to the Cl0p ransomware ring. The attackers used the vulnerability to deploy net shells on the public-facing net interfaces to MOVEit Switch servers—net shells that in some circumstances continued after the vulnerabilities had been patched by Progress clients.
MOVEit was simply considered one of plenty of “zero day” vulnerabilities that challenged defenders in 2023. GoAnywhere, one other managed file switch system, disclosed a vulnerability in February that one other CL0p-affiliated group tried to take advantage of. And a distant code execution vulnerability within the PaperCut MF and NG print server software program merchandise was exploited by the Bl00dy ransomware gang in March and April after being reported to the builders in January.
In some circumstances, these vulnerabilities merely can’t be patched. For instance, a vulnerability in Barracuda E mail Safety Gateway home equipment, present in June, was so extreme that it couldn’t be patched and required full substitute of bodily or digital home equipment. A Chinese language menace group continued to take advantage of the weak home equipment all through the remainder of 2023.
Vulnerabilities in software program and units don’t need to be new to be leveraged by attackers. Risk actors regularly search out software program that has fallen out of assist, resembling older community firewalls and net server software program, to focus on— figuring out that no patch will probably be coming.
Provide chain assaults and digitally signed malware
Small companies additionally need to be involved in regards to the safety of the companies they rely on to handle their enterprise—and their IT infrastructure. Provide chain assaults will not be only for nation-state actors; we’ve seen assaults towards managed service suppliers develop into a permanent a part of the ransomware playbook.
In 2023, Sophos MDR responded to 5 circumstances by which small enterprise clients had been attacked by way of an exploit of a service supplier’s distant monitoring and administration (RMM) software program. The attackers used the NetSolutions RMM agent operating on the focused organizations’ computer systems to create new administrative accounts on the focused networks, after which deployed industrial distant desktop, community exploration and software program deployment instruments. In two of the circumstances, the attackers efficiently deployed LockBit ransomware.
It’s exhausting to defend towards assaults that leverage trusted software program, particularly when that software program offers attackers the flexibility to disable endpoint safety. Small companies and the service suppliers who assist them should be vigilant to alerts that endpoint safety has been turned off on techniques on their networks, as a result of this can be an indication that an attacker has gained privileged entry by way of a provide chain vulnerability—or by way of different software program that at the beginning look could appear reputable.
For instance, in 2023, we noticed plenty of situations of attackers utilizing weak kernel drivers from older software program that also had legitimate digital signatures, and of deliberately created malicious software program that used fraudulently obtained digital signatures—together with malicious kernel drivers digitally signed by way of Microsoft’s Home windows {Hardware} Compatibility Writer (WHCP) program—to evade detection by safety instruments and run code that disables malware safety.
Kernel drivers function at a really low degree inside the working system, and are usually loaded earlier than different software program throughout the working system’s start-up. That implies that they execute in lots of circumstances earlier than safety software program can begin up. Digital signatures act as a license to drive, so to talk—in all variations of Home windows since Home windows 10 model 1607, kernel drivers have to have a sound digital signature or Home windows working techniques with Safe Boot enabled gained’t load them.
In December 2022, Sophos notified Microsoft of the invention of malicious kernel drivers that carried Microsoft-signed certificates. As a result of these drivers had Microsoft-signed certificates, they had been by default accepted as benign software program, permitting them to be put in—after which disable endpoint protections on techniques that they had been put in on. Microsoft issued a safety advisory, after which in July 2023 revoked a bunch of malicious drivers’ certificates that had been obtained by way of WHCP.
Drivers don’t need to be malicious to get exploited. We’ve seen a number of circumstances of drivers and different libraries from older and even present variations of software program merchandise leveraged by attackers to “aspect load” malware into system reminiscence.
We’ve additionally seen Microsoft’s personal drivers utilized in assaults. A weak model of a driver for Microsoft’s Course of Explorer utility has been used a number of occasions by ransomware operators in efforts to disable endpoint safety merchandise; in April 2023, we reported on a software dubbed “AuKill” that used this driver in a number of assaults in makes an attempt to deploy Medusa Locker and LockBit ransomware.
Generally we get fortunate and catch weak drivers earlier than they are often exploited. In July, Sophos behavioral guidelines had been triggered by exercise from a driver for an additional firm’s safety product. The alert was triggered by a buyer’s personal attacker simulation check, however our investigation of the occasion uncovered three vulnerabilities that we reported to the software program vendor and had been subsequently patched.
Spammers push social engineering boundaries
E mail might appear to be an old-school communication technique in an period of encrypted end-to-end cellular chats, however spammers didn’t appear to note (or care) about that. Whereas the standard BEC technique of merely posing as an worker and asking one other worker to ship present playing cards persists, spammers have gotten way more inventive.
Up to now 12 months, Sophos’ messaging safety crew got here throughout a slew of recent social engineering tips and methods designed to evade typical e-mail controls. Messages by which the attacker emails an attachment or hyperlink out of the blue are actually passé: The simpler spammers usually tend to strike up a dialog first, then transfer in for the kill in observe up emails.
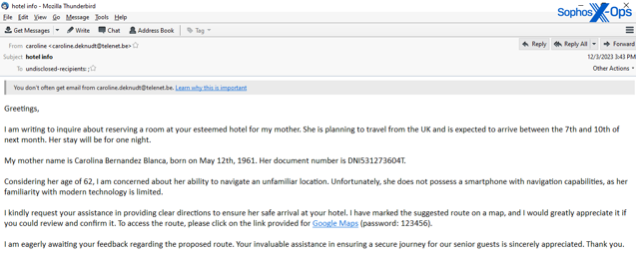
We noticed this system in assaults by which spammers posing as supply service staff known as enterprise clients on the cellphone and requested them to open a weaponized e-mail. We additionally noticed spammers initially e-mail a solicitation for enterprise or criticism, in assaults concentrating on quite a lot of industries in 2023, adopted by a hyperlink to obtain a disguised, weaponized file after the enterprise responded to the primary e-mail.
Standard spam prevention entails processes inspecting message content material and making choices primarily based on that content material. Spammers experimented with quite a lot of strategies of changing any textual content content material of their messages with embedded pictures: Generally the photographs gave the impression to be a written message, whereas others experimented with using QR codes or pictures that look like invoices (with phone numbers the attackers immediate victims to name) as a technique to evade detection.
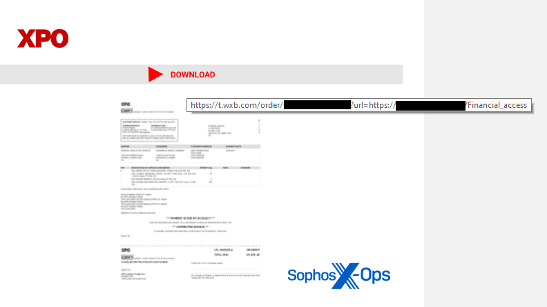
Malicious attachments even pushed boundaries, with weaponized PDFs making one thing of a comeback, linking to malicious scripts or websites, typically utilizing embedded QR codes. The Qakbot malware household expansively abused Microsoft’s OneNote doc format, the pocket book (or .one file), to ship payloads earlier than being shut down later within the 12 months in a coordinated takedown. Attackers additionally latched onto the MSIX file format – a kind of archive file format utilized by Microsoft to distribute apps by way of the Home windows App Retailer – as a method of bypassing detection.

And attackers abused Microsoft’s companies as nicely: By the 12 months’s finish, about 15% of the overall spam Sophos blocked had been despatched utilizing e-mail accounts created in Microsoft’s business-oriented onmicrosoft.com messaging system.
Cellular malware and social engineering threats
Small companies rely closely on cellular units as a part of both authorised or ad-hoc info techniques. Textual content messages, messaging and communications functions, and apps connecting to cloud companies—together with cellular level of sale functions—are mission-critical techniques for distributed small enterprises. Cybercriminals know that, and proceed to seek out methods to focus on cellular gadget customers to achieve entry to information or to defraud.
Adware and “bankers” are a bunch of Android malware of explicit concern, and which we imagine will proceed to be a menace. Adware is used to reap information on the cellphone—and typically will even subscribe the gadget’s person to premium-rate companies for direct financial acquire. They harvest private information, together with SMS messages and name logs from the affected gadget, which is then offered to fraudsters or used for blackmail—or each. There have been a number of circumstances the place victims have taken their very own lives on account of threats from spyware and adware operators.
These malicious cellular functions are distributed in plenty of methods. They might masquerade as reputable functions on the Google Play app retailer or third-party app retailer websites—typically as cellular lending functions. They’re additionally unfold by way of hyperlinks despatched by way of textual content messages.
Bankers are malware that concentrate on monetary functions, together with cryptocurrency wallets, to reap account information to achieve entry to funds—utilizing accessibility permissions to achieve entry to delicate information on the cellphone.
Then there’s the phenomenon of “pig butchering,” or sha zhu pan. We started monitoring faux functions on each the iOS and Android platform tied to a type of rip-off we first known as “CryptoRom” in early 2021; since then, the scams have develop into more and more extra refined.
The crime rings that function these scams— regularly operated out of scamming compounds staffed with individuals who have basically been kidnapped by organized crime—have taken billions of {dollars} from victims worldwide, and infrequently give attention to individuals tied to small companies. In 2023, a small financial institution in Kansas failed and was seized by the FDIC after the financial institution CEO despatched over $12 million from deposits to scammers in an effort to get well funds he had misplaced reportedly in considered one of these scams. This tragic instance reveals how a rip-off often related to a person’s private life can have ramifications and impression on small companies.
Sha zhu pan scammers lure victims by way of social media websites, courting apps, different apps and neighborhood platforms, and even “inadvertent” SMS messages. They have an inclination to focus on people who’re searching for a romantic connection or friendship. After transferring the goal to a safe messaging app resembling WhatsApp or Telegram, they acquire their belief and introduce a money-making concept that they declare to have inside data about—and that often entails cryptocurrency.
Over the previous 12 months, we’ve seen the faux functions utilized by these scams making their method into the Google Play and iOS App shops. They evade retailer safety evaluate by presenting as a benign app till the evaluate course of is over, after which change distant content material to show it right into a faux crypto buying and selling app. Any crypto deposited by way of these apps is instantly pocketed by the scammers.
Just lately, we’ve additionally seen these scams undertake a tactic from one other sort of crypto rip-off that requires no faux apps—as an alternative, they use the “Web3” performance of cellular crypto pockets apps to straight faucet into wallets created by the victims. Now we have recognized lots of of domains related to these “DeFi (Decentralized Finance) mining” variants of sha zhu pan, and as with the faux apps we establish, we proceed to report them and work to get them taken down.
Conclusions
Small companies face no scarcity of threats, and the sophistication of these threats is usually on par with these used to assault massive enterprises and governments. Whereas the amount of cash that may be stolen is lower than obtainable from a bigger group, the criminals are joyful to steal what you will have and make up for it in quantity.
Legal syndicates are relying on smaller firms to be much less well-defended and to not have deployed fashionable, refined instruments to guard their customers and belongings. The important thing to efficiently defending towards these threats is to show their assumptions fallacious: Educate your workers, deploy multifactor authentication on all externally dealing with belongings, patch servers and community home equipment with the utmost precedence and think about migrating tough to handle belongings like Microsoft Alternate servers to SaaS e-mail platforms.
The first distinction in our expertise between the businesses that had been impacted probably the most by cyberattacks and those that suffered the least is time to reply. Having safety consultants to observe and reply 24/7 is desk stakes for an efficient protection in 2024. Staying secure isn’t inconceivable; it simply takes complete planning and layered defenses to purchase you time to reply and decrease damages.