Menace actors have been noticed serving malicious code by using Binance’s Sensible Chain (BSC) contracts in what has been described because the “subsequent degree of bulletproof internet hosting.”
The marketing campaign, detected two months in the past, has been codenamed EtherHiding by Guardio Labs.
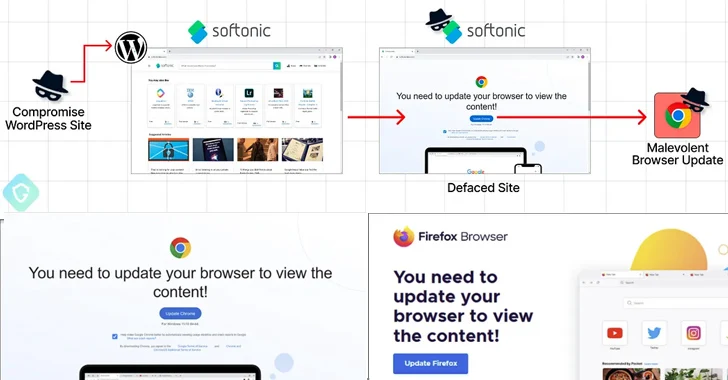
The novel twist marks the newest iteration in an ongoing marketing campaign that leverages compromised WordPress websites to serve unsuspecting guests a pretend warning to replace their browsers earlier than the websites might be accessed, finally resulting in the deployment of knowledge stealer malware equivalent to Amadey, Lumma, or RedLine.
“Whereas their preliminary methodology of internet hosting code on abused Cloudflare Employee hosts was taken down, they’ve rapidly pivoted to make the most of the decentralized, nameless, and public nature of blockchain,” safety researchers Nati Tal and Oleg Zaytsev mentioned.
“This marketing campaign is up and more durable than ever to detect and take down.”
It is no shock that menace actors have focused WordPress websites through each malicious plugins, in addition to make the most of publicly disclosed safety flaws in in style plugins to breach web sites. This offers the flexibility to utterly hijack contaminated web sites at will.
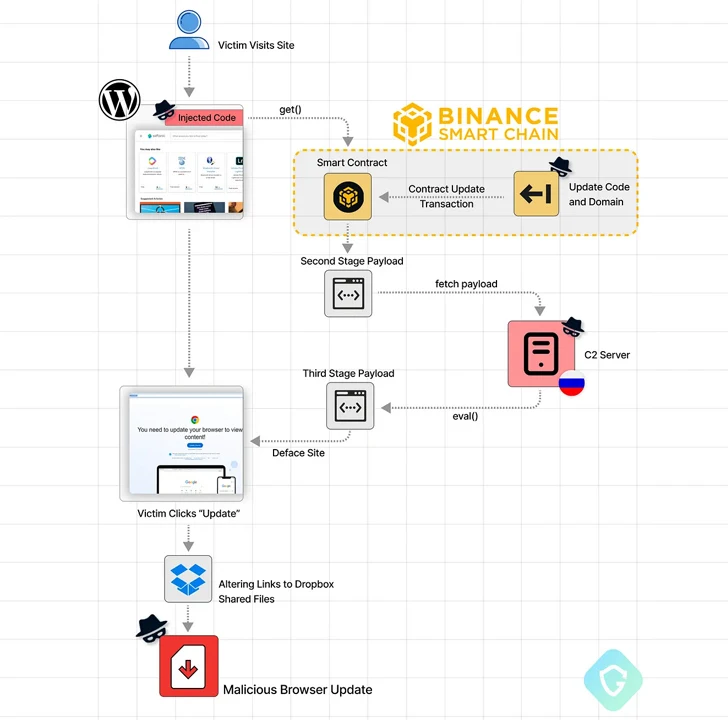
Within the newest set of assaults, the contaminated websites are injected with obfuscated Javascript designed to question the BNB Sensible Chain by making a sensible contract with an attacker-controlled blockchain deal with.
The objective is to fetch a second-stage script that, in flip, retrieves a third-stage payload from a command-and-control (C2) server to serve the misleading browser replace notices.
Ought to a sufferer click on the replace button on the bogus overlay, they’re redirected to obtain a malicious executable from Dropbox or different authentic file internet hosting companies.
Whereas the deal with and the related contract have been tagged as utilized in a phishing scheme, the consequence of internet hosting it on a decentralized service means that there’s presently no method to intervene and disrupt the assault chain.
“As this isn’t an deal with utilized in any monetary or different exercise that victims might be lured to switch funds or some other sort of Mental property to — guests of compromised WordPress websites haven’t any clue as to what’s going on below the hood,” the researchers defined.
“This contract, tagged as pretend, malicious, or whatnot, remains to be on-line and delivers the malicious payload.”
With plugins turning into a large assault floor for WordPress, it is beneficial that customers counting on the content material administration system (CMS) adhere to safety greatest practices and preserve their methods up-to-date with the newest patches, take away undesirable admin customers, and implement robust passwords.