Authored by ZePeng Chen and Wenfeng Yu
McAfee Cell Analysis Workforce has noticed an lively rip-off malware marketing campaign focusing on Android customers in India. This malware has gone via three phases. The primary one is the event stage, from March 2023 to July 2023, throughout which a few functions have been created every month. The second is the enlargement stage, from August 2023 to October 2023, throughout which dozens of functions have been created every month. The third is the lively stage, from September 2023 to the current, throughout which a whole bunch of functions have been created every month. In accordance with McAfee’s detection telemetry knowledge, this malware has amassed over 800 functions and has contaminated greater than 3,700 Android gadgets. The marketing campaign continues to be ongoing, and the variety of contaminated gadgets will proceed to rise.
Malware builders create phishing pages for situations which might be straightforward to deceive, akin to electrical energy invoice funds, hospital appointments, and courier package deal bookings. Builders use completely different functions to load completely different phishing pages, that are finally offered to scammers. In our analysis, greater than 100 distinctive phishing URLs and greater than 100 distinctive C2 URLs are created in these malicious functions. It signifies that every scammer can perform rip-off actions independently.
Scammers use malware to assault victims. They usually contact victims by way of telephone, textual content, e mail, or social functions to tell them that they should reschedule providers. This type of fraud assault is a typical and efficient fraud methodology. Because of this, victims are requested to obtain a selected app, and submit private data. There was a report the place an Indian girl downloaded malware from a hyperlink in WhatsApp and about ₹98,000 was stolen from her. We weren’t capable of affirm if is identical malware, but it surely is only one instance of how these malicious functions will be distributed instantly by way of WhatsApp.
The assault state of affairs seems credible, many victims don’t doubt the scammers’ intentions. Following the directions offered, they obtain and put in the app. Within the app, victims are induced to submit delicate data akin to private telephone numbers, addresses, financial institution card numbers, and passwords. As soon as this data falls into the fingers of scammers, they’ll simply steal funds from the sufferer’s checking account.
The malware not solely steals victims’ checking account data by way of phishing internet pages but additionally steals SMS messages on victims’ gadgets. Due to the stolen data, even when the checking account helps OTP authentication, the scammer can switch all of the funds. The malware makes use of professional platforms to deploy phishing pages to make it seem extra reliable to evade detection.
McAfee Cell Safety detects this menace as Android/SmsSpy. For extra data, and to get absolutely protected, go to McAfee Cell Safety.
Malware-as-a-Service (MaaS)
We found that these phishing pages and malware have been being offered as a service by a cyber group named ELVIA INFOTECH. A definite distinction between this malware and others is that the apps offered have a sound expiration date. When the expiration date is reached, some utility hyperlinks will redirect to a cost notification web page. The notification is clearly to request the purchaser to pay a charge to revive the usage of the malware.
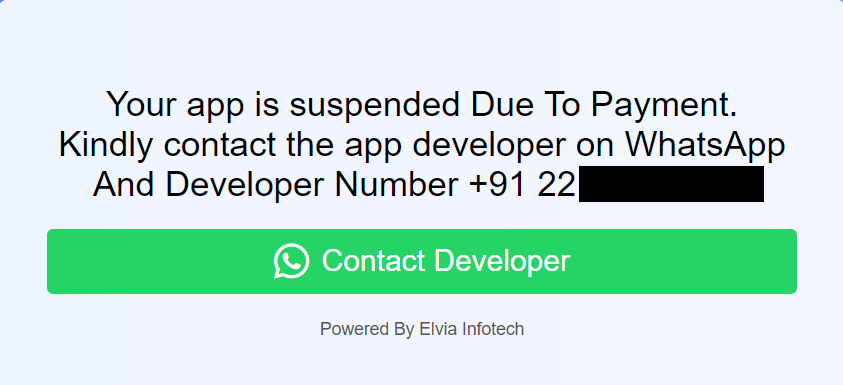
Determine 1. Cost notification.
We additionally found that the cybercriminal group was promoting malware in a Telegram group. Primarily based on these observations, we consider that ELVIA INFOTECH is an expert cybercriminal group engaged within the growth, upkeep, and sale of malware and phishing web sites.
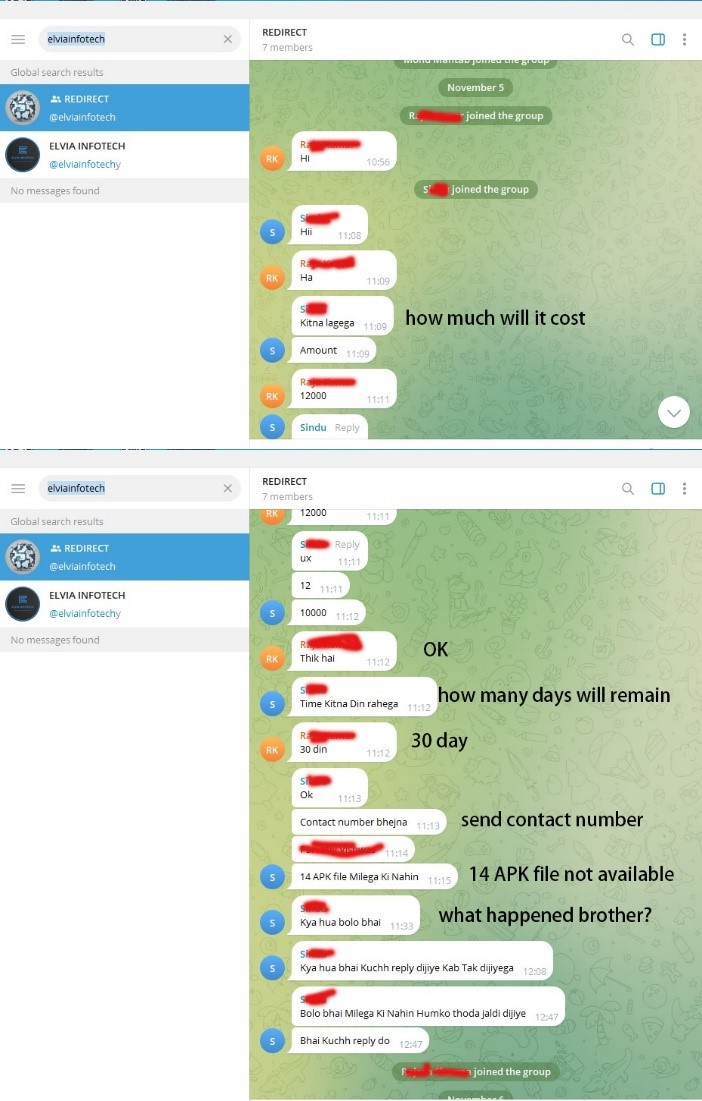
Determine 2. Telegram Group dialog.
Malware Evaluation
This malware has been maintained and lately up to date, and a whole bunch of malicious functions have been created. They like to make use of the file names akin to “CustomerSupport.apk”, “Mahavitaran Invoice Replace.apk”, “Appointment Reserving.apk”, “Hospital Assist.apk”, “Emergency Courier.apk” and the applying names akin to “Buyer Assist”, “Blue Dart”, “Hospital Assist”,” Emergency Courier” to trick victims, beneath are some functions’ names and icons.

Determine 3. Some functions’ names and icons
Not solely do they fake to be “Buyer Assist”, however additionally they fake to be standard courier corporations like “Blue Dart” in India, however additionally they goal utility corporations like “Mahavitaran” (Energy Company of India).
As soon as victims click on the faux icon, the applying can be launched and begin to assault victims.
1. Loading Phishing Pages
The phishing web page hundreds as soon as the applying is launched. It’ll disguise itself as a web page of varied professional providers, making victims consider that they’re visiting a professional service web site. Right here, victims are tricked into offering delicate data akin to title, tackle, telephone quantity, financial institution card quantity, and password. Nevertheless, as soon as submitted, this data falls into the fingers of scammers, permitting them to simply entry and management the sufferer’s checking account.
We discovered that almost all of this assault marketing campaign impersonated service package deal supply corporations.

Determine 4. Phishing Pages Load As soon as App Launches
The malware builders additionally designed completely different phishing pages for various functions to deceive victims in numerous situations that exploit electrical energy invoice funds and hospital appointments.
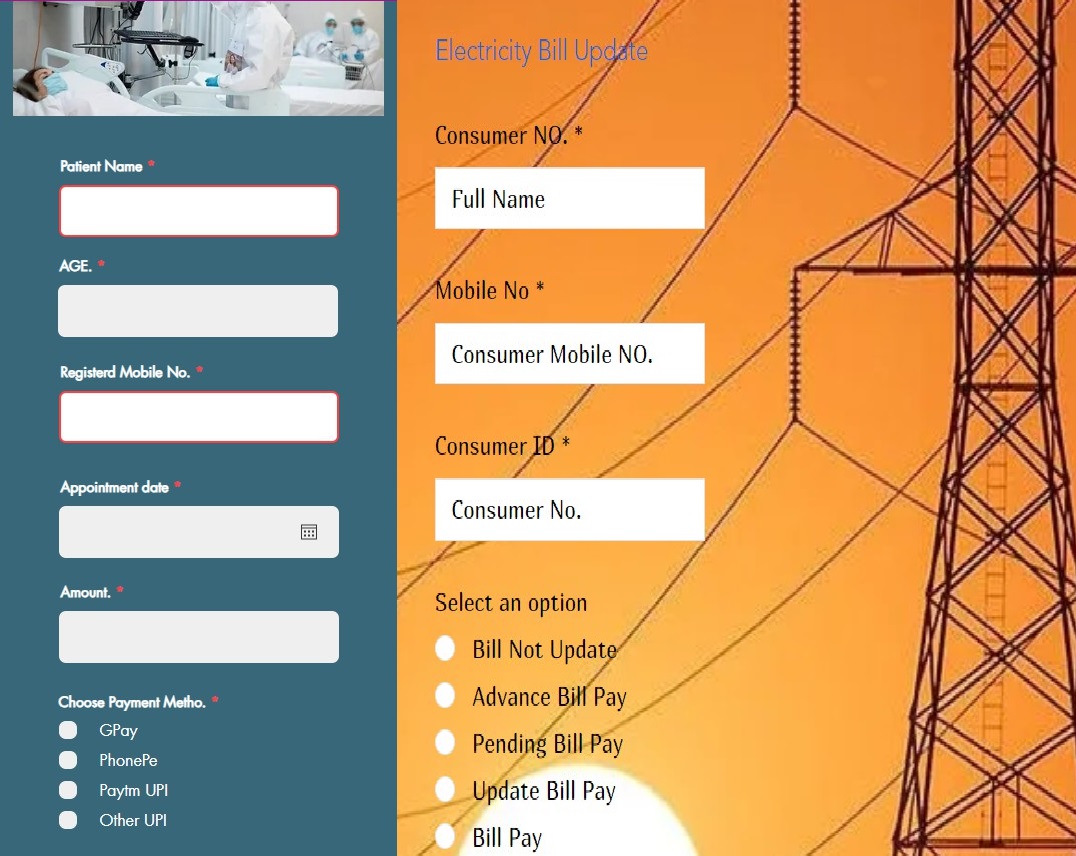
Determine 5. Hospital appointment and Electrical energy Invoice Phishing Pages
2. Stealing One-Time Passwords by way of SMS message
As a core design of this malware, the applying requests permissions to permit it to ship and look at SMS messages as soon as it launches.
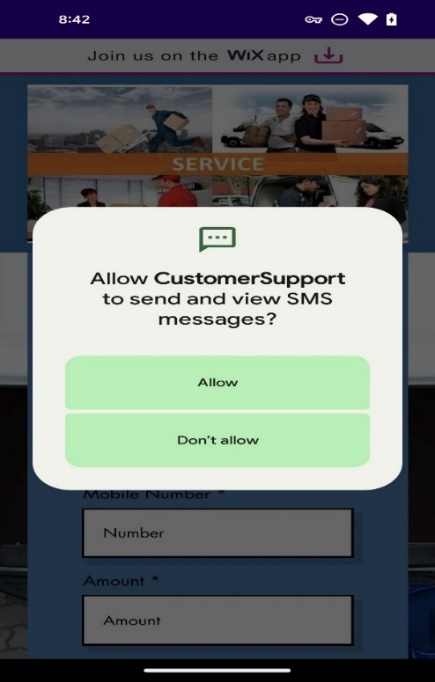
Determine 6. Request SMS permissions.
If victims click on the “Permit” button, the malware begins a background service that secretly screens customers’ textual content messages and forwards them to a quantity which is from C2 server.
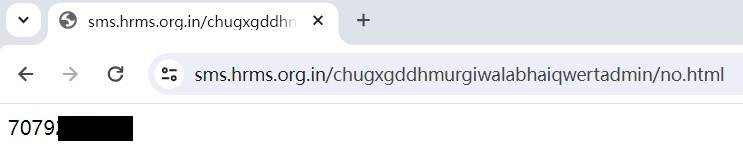
Determine 7. Ahead telephone quantity from C2 server
This step is essential for the rip-off course of, as many banks ship a one-time password (OTP) to the shopper’s telephone for transaction verification. Utilizing this methodology, the scammers can get hold of these OTPs and efficiently full financial institution transactions.
Conclusion:
This malicious app and the builders behind it have emerged quickly in India from final 12 months to now, purposefully creating and sustaining malware, and specializing in deploying well-designed phishing web sites via professional platforms. The group secretly promotes and sells its malware via social media platforms, making the unfold of the malware extra delicate and troublesome to detect. This tactic resulted in an much more extreme malware outbreak, posing an ongoing and critical menace to the monetary safety of Indian customers.
Malware campaigns are very persistent and utilizing a number of completely different functions on completely different web sites can trick many victims into putting in these functions and offering their non-public and private data, which might then be used to commit fraud. On this setting, unusual customers in India face enormous cybersecurity challenges. Subsequently, customers want to stay vigilant and cautious when coping with any digital communications or utility obtain requests that seem professional however might comprise malware. We strongly advocate customers set up safety software program on their gadgets and at all times hold it updated. By utilizing McAfee Cell Safety merchandise, customers can additional defend their gadgets and cut back the dangers related to this kind of malware, offering a safer expertise.
Indicators of Compromise (IOCs)
SHA256 hash Checklist:
- 092efedd8e2e0c965290154b8a6e2bd5ec19206f43d50d339fa1485f8ff6ccba
- 7b1f692868df9ff463599a486658bcdb862c1cf42e99ec717e289ddb608c8350
- c59214828ed563ecc1fff04efdfd2bff0d15d411639873450d8a63754ce3464c
- b0df37a91b93609b7927edf4c24bfdb19eecae72362066d555278b148c59fe85
- 07ad0811a6dac7435f025e377b02b655c324b7725ab44e36a58bc68b27ce0758
- c8eb4008fa4e0c10397e0fb9debf44ca8cbadc05663f9effbeac2534d9289377
- 1df43794618ef8d8991386f66556292429926cd7f9cf9b1837a08835693feb40
- 5b3d8f85f5637b217e6c97e6b422e6b642ce24d50de4a6f3a6b08c671f1b8207
Phishing URLs:
- hxxps://bijlipayupdate[.]wixsite[.]com/my-site
- hxxps://appointmentservice0[.]wixsite[.]com/onlineappointment
- hxxps://couriers9343[.]wixsite[.]com/courier/
- hxxps://doctorappointment34[.]wixsite[.]com/appointmentbooking
- hxxps://hospitalservice402[.]wixsite[.]com/hospital-in
- hxxps://adn-reg[.]com/web site
C2 Server URLs:
- hxxps://forexroyality[.]on-line/complainf13/My_File[.]txt
- hxxps://adn-reg[.]com/knowledge[.]json
- hxxps://icustomrcore[.]com/chand3/knowledge[.]json
- hxxps://sms[.]hrms[.]org[.]in/chugxgddhmurgiwalabhaiqwertadmin/no[.]html
- hxxps://krishna[.]salaar[.]co[.]in/admindata[.]txt
- hxxps://courier[.]elviainfotech[.]cloud/pages/telephone[.]json

