
The BlackCat/ALPHV ransomware operation has begun to make use of a brand new instrument named ‘Munchkin’ that makes use of digital machines to deploy encryptors on community units stealthily.
Manchkin permits BlackCat to run on distant methods or encrypt distant Server Message Block (SMB) or Widespread Web File (CIFS) community shares.
The introduction of Munchkin to BlackCat’s already intensive and superior arsenal makes the RaaS extra engaging to cybercriminals in search of to develop into ransomware associates.
Hiding in VirtualBox
Palo Alto Networks Unit 42 has found that BlackCat’s new Munchkin instrument is a personalized Alpine OS Linux distribution that comes as an ISO file.
After compromising a tool, the risk actors set up VirtualBox and create a brand new digital machine utilizing the Munchkin ISO.
This Munchkin digital machine features a suite of scripts and utilities that permit the risk actors to dump passwords, unfold laterally on the community, construct a BlackCat ‘Sphynx’ encryptor payload, and execute packages on community computer systems.
Upon boot, it adjustments the basis password to 1 identified solely by the attackers and leverages the ‘tmux’ utility to execute a Rust-based malware binary named ‘controller’ that begins to load scripts used within the assault.
These scripts are listed under:
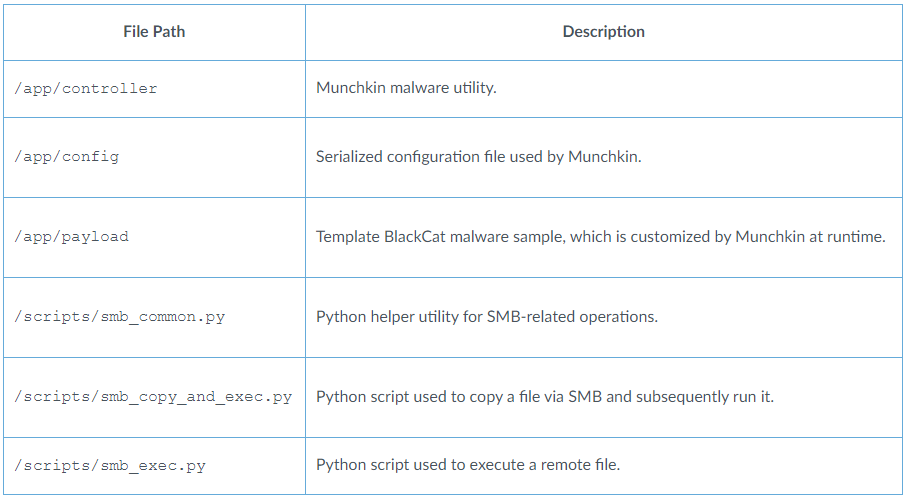
Supply: Unit 42
The ‘controller’ makes use of the bundled configuration file, which gives entry tokens, sufferer credentials, and authentication secrets and techniques, in addition to configuration directives, folder and file blocklists, duties to run, and hosts to focus on for encryption.
This configuration is used to generate customized BlackCat encryptor executables within the /payloads/ listing, that are then pushed to distant units to encrypt recordsdata or encrypt SMB and CIFS community shares.
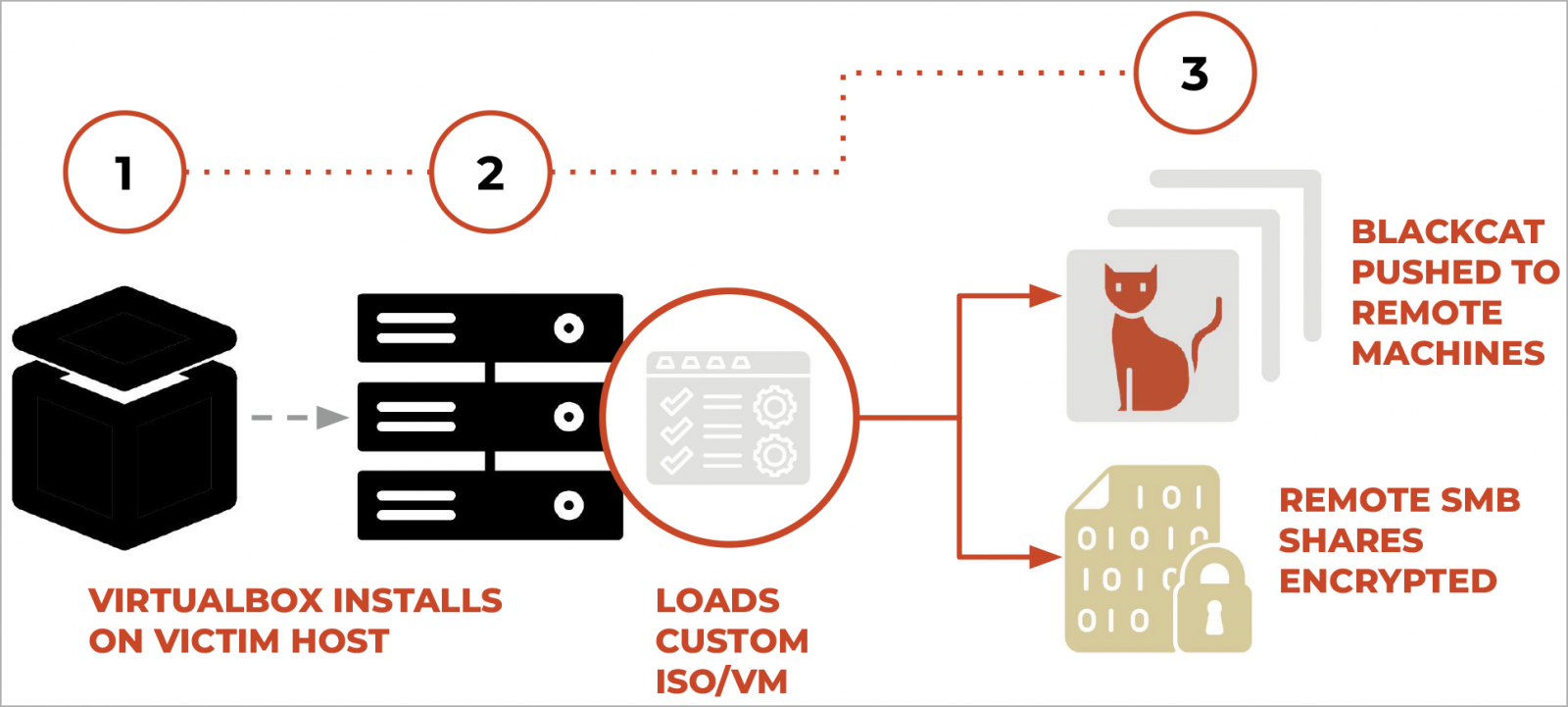
Supply: Unit 42
Unit 42 found a message within the malware’s code from BlackCat’s authors to their companions, warning in opposition to leaving the ISO on the right track methods because of the lack of encryption for the configuration, particularly highlighting the danger of chat entry token leakage.
A typical downside affecting ransomware victims and cybercriminals is that samples generally get leaked via malware evaluation websites. Analyzing the ransomware samples permits researchers to realize full entry to the negotiation chat between a ransomware gang and its sufferer.
To stop this, associates present Tor negotiation website entry tokens at run-time when launching. Subsequently, it is unattainable to realize entry to a sufferer’s negotiation chat, even when they’ve entry to the pattern used within the assault.
Resulting from this, the risk actors warn associates that they need to delete the Munchkin digital machines and ISOs to stop these entry tokens from leaking.
The builders additionally embrace directions and tips about utilizing ‘Controller’ to observe the assault’s progress and launch duties.
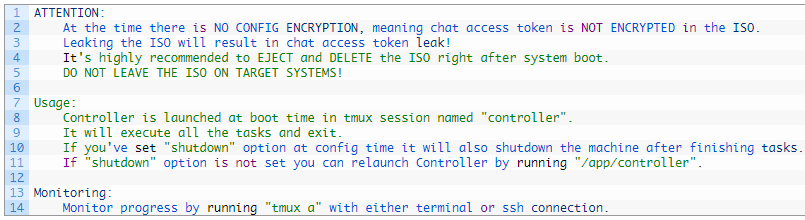
Supply: Unit 42
Munchkin makes it simpler for BlackCat ransomware associates to carry out varied duties, together with bypassing safety options defending the sufferer’s gadget. It’s because digital machines present a layer of isolation from the working system, making detection and evaluation tougher for safety software program.
Moreover, the selection of Alpine OS ensures a small digital footprint, and the instrument’s automated operations scale back the necessity for guide interventions and noise from command feeds.
Lastly, the modularity of Munchkin, that includes a wide range of Python scripts, distinctive configurations, and the flexibility to swap payloads as wanted, makes the instrument straightforward to regulate to particular targets or campaigns.
BlackCat nonetheless evolving
BlackCat emerged in late 2021 as a classy Rust-based ransomware operation because the successor to BlackMatter and Darkside.
The RaaS has adopted a profitable trajectory to this point, usually introducing superior options like extremely configurable intermittent encryption, information leak API, Impacket and Remcom embedding, encryptors with assist for customized credentials, signed kernel drivers, and upgrades on the info exfiltration instrument.
Notable BlackCat victims in 2023 embrace the Florida Circuit Court docket, MGM Resorts, Motel One, Seiko, Estee Lauder, HWL Ebsworth, Western Digital, and Constellation Software program.
