A bounty of $12,288 has been introduced for the primary particular person to crack the NIST elliptic curves seeds and uncover the unique phrases that have been hashed to generate them.
The bounty shall be tripled to $36,864 if the award recipient chooses to donate the quantity to any 501(c)(3) charity.
This problem was introduced by cryptography specialist Filippo Valsorda, who raised the quantity with the assistance of acknowledged figures in cryptography and cybersecurity.
This contains Johns Hopkins College professor Matt Inexperienced, PKI and Chromium contributor Ryan Sleevi, browser safety skilled Chris Palmer, “Logjam assault” developer David Adrian, and AWS cryptography engineer Colm MacCárthaigh.
Background
In Elliptic Curve Cryptography (ECC), seeds are values or units of values used because the preliminary enter for an encryption algorithm or course of to provide cryptographic keys.
ECC depends on the mathematical idea of elliptic curves outlined over finite fields to generate comparatively quick but safe keys. Utilizing curves ensures that, for a particular level (on them), it is computationally infeasible to find out the a number of of that time (scalar) used to provide it, offering the premise for encryption.
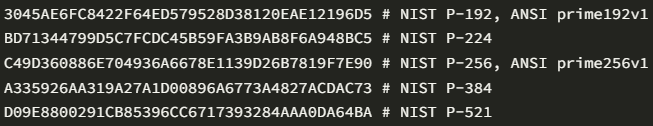
NIST elliptic curves (P-192, P-224, P-256, P-384, and P-521), launched in 2000 by means of the company’s FIPS 186-2 on ‘Digital Signature Commonplace,’ and that are essential to trendy cryptography, have been generated in 1997 utilizing seeds offered by the NSA.
The curves are specified by their coefficient and a random seed worth, whereas the deterministic course of to derive the keys is clear and verifiable to alleviate fears of hidden vulnerabilities.
Finish customers and builders do not must work together instantly with these seeds however as an alternative, use the curve parameters within the chosen cryptographic protocol. Nonetheless, these involved with the integrity and safety of the system are genuinely within the origin of the seeds.
No person is aware of how the unique seeds have been generated, however rumors and analysis counsel that they’re hashes of English sentences offered to Solinas by the NSA.
Solinas is believed to have used a hashing algorithm, in all probability SHA-1, to generate the seeds and presumably forgot concerning the phrases without end.
“The NIST elliptic curves that energy a lot of recent cryptography have been generated within the late ’90s by hashing seeds offered by the NSA. How have been the seeds generated?,” reads a weblog put up by Valsorda.
“Rumor has it that they’re in flip hashes of English sentences, however the one who picked them, Dr. Jerry Solinas, handed away in early 2023 forsaking a cryptographic thriller, some conspiracy theories, and an historic password cracking problem.”
Voices of concern from the cryptographic neighborhood began a few years in the past, beginning with the Dual_EC_DRBG controversy that claimed the NSA backdoored the algorithm.
Probably the most worrying situation arises from hypothesis and skepticism about an intentional weak spot integrated within the NIST curves, which might allow the decryption of delicate information.
Although no substantial proof exists to help these situations, the seeds’ origin stays unknown, creating concern and uncertainty locally.
Cracking problem
The safety implications that come up from the considerations that the NSA deliberately chosen weak curves are dire, and discovering the unique sentences used to generate them would dispel these considerations as soon as and for all.
Other than that, this problem holds historic significance, contemplating that NIST elliptic curves are foundational in trendy cryptography.
Additionally, that is, primarily, a cryptographic thriller that provides intrigue to the entire story, particularly after Dr. Solinas’ demise.
Filippo Valsorda believes anybody with sufficient GPU energy and passphrase brute-forcing expertise might crack the (presumed) SHA-1 hashes and derive the unique sentences.
The primary submission of not less than one pre-seed sentence will obtain half the bounty ($6,144), and the opposite half will go to the primary one that submits the entire package deal of 5. If it is the identical particular person, they may get the whole bounty of $12k.
Extra particulars concerning the problem and tips on how to submit your findings might be present in Valsorda’s weblog.