On daily basis, private knowledge, resembling location info, pictures, or textual content queries are handed between your gadget and distant, cloud-based companies. Your knowledge is encrypted when in transit and at relaxation, however as potential assault vectors develop extra refined, knowledge should even be protected throughout use by the service, particularly for software program programs that deal with personally identifiable person knowledge.
Towards this purpose, Google’s Mission Oak is a analysis effort that depends on the confidential computing paradigm to construct an infrastructure for processing delicate person knowledge in a safe and privacy-preserving manner: we guarantee knowledge is protected throughout transit, at relaxation, and whereas in use. As an assurance that the person knowledge is the truth is protected, we’ve open sourced Mission Oak code, and have launched a clear launch course of to present publicly inspectable proof that the applying was constructed from that supply code.
This weblog submit introduces Oak’s clear launch course of, which depends on the SLSA framework to generate cryptographic proof of the origin of Oak’s confidential computing stack, and along with Oak’s distant attestation course of, permits customers to cryptographically confirm that their private knowledge was processed by a reliable software in a safe surroundings.
Mission Oak lately collaborated with the SLSA neighborhood to create a brand new container-based builder that produces Provide-chain Ranges for Software program Artifacts (SLSA) Construct Degree 3 provenance. This new container-based builder generates non-forgeable provenance statements that seize particulars about construct course of info that permit customers to carry out automated, rigorous provenance verification.
With this enhanced provenance generated by the container-based builder, you may reply questions like:
-
Was the artifact constructed with a toolchain that I do know and belief?
-
Was the artifact constructed with a command that I belief?
-
Did the construct command use a software that was affected by a vulnerability?
-
How can I recreate the artifact?
Mission Oak is especially excited by answering these questions on each layer of the confidential computing stack. As an example, to make certain that a launched binary was constructed utilizing a trusted construct course of (e.g., the construct command didn’t use any probably malicious software), the Oak launch course of compares the construct command towards a set of allow-listed tokens. Equally, we will confirm that the builder was not tampered with.
Mission Oak develops a safe runtime and a distant attestation protocol—methods to detect potential adversaries on distant servers and to guard workloads whereas they’re operating. Now, with the addition of the container-based SLSA builder, we’re capable of full our clear launch course of to guard towards software program provide chain assaults and supply an automatic course of for verifying the integrity and trustworthiness of a distant server, earlier than sending delicate info to it.
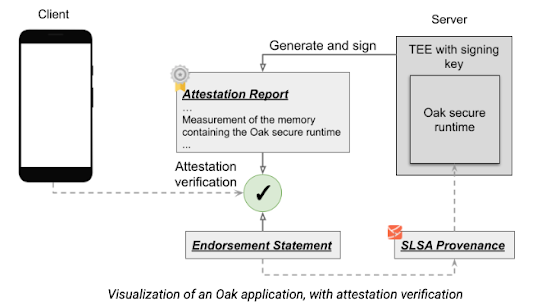
Particularly, for every launched model of the Oak safe runtime, the Oak group generates and indicators an endorsement assertion for the binary, utilizing a key accessible solely to the Oak group. The endorsement assertion can solely be generated if the provenance assertion passes verification checks, making certain {that a} potential malicious attacker can not forge the assertion.
When the shopper establishes a connection to the server, the shopper should confirm the endorsement assertion and the proof of its inclusion in a transparency log, and test that the binary identities within the attestation report and the endorsement assertion are the identical. This, along with signature verification for the endorsement assertion, ensures three necessary factors of belief for the general course of: that the shopper is interacting with the identical publicly endorsed model of the Oak safe runtime that every one different shoppers work together with; the Oak safe runtime is open supply; and that it has a publicly revealed non-forgeable SLSA v1.0 provenance with adherence to SLSA Construct Observe 3. For a extra technical rationalization of the method, see Mission Oak’s clear launch course of.
Visualization of an Oak software, with attestation verification
We encourage you to take a look at the clear launch undertaking as a use case for SLSA. Please attain out to us by way of our slack channel to discover concepts associated to Oak safe runtimes and distant attestation.
You don’t want to make use of Mission Oak to make the most of the brand new SLSA builder software. In case your undertaking is open supply, attempt one of many SLSA builders to generate non-forgeable provenance in your binaries. We encourage you to containerize your construct and check out the container-based SLSA 3 builder! Utilizing a container picture in your builds improves the reproducibility of your binaries. We additionally advocate including the directions for constructing your container picture (e.g., a Dockerfile) to your GitHub repository, which improves auditability and transparency of your construct course of, and thus the safety of your software program provide chain.