
The favored D-Hyperlink DAP-X1860 WiFi 6 vary extender is inclined to a vulnerability permitting DoS (denial of service) assaults and distant command injection.
The product is presently listed as accessible on D-Hyperlink’s web site and has 1000’s of opinions on Amazon, so it is a well-liked alternative amongst customers.
A workforce of German researchers (RedTeam) who found the vulnerability, tracked as CVE-2023-45208, report that regardless of their makes an attempt to alert D-Hyperlink a number of occasions, the seller has remained silent, and no fixes have been launched.
Vulnerability particulars
The issue lies within the community scanning performance of D-Hyperlink DAP-X1860, particularly, the lack to parse SSIDs containing a single tick (‘) within the title, misinterpreting it as a command terminator.
Technically, the issue originates from the ‘parsing_xml_stasurvey’ perform within the libcgifunc.so library, which comprises a system command for execution.
Nevertheless, given the product’s lack of SSID sanitization, an attacker can simply abuse this characteristic for malicious functions.
An attacker inside the extender’s vary can arrange a WiFi community and deceptively title it just like one thing the goal is accustomed to however embody a tick within the title, like ‘Olaf’s Community,’ for instance.
When the machine makes an attempt to connect with that SSID, it would produce an “Error 500: Inside Server Error”, failing to function usually.
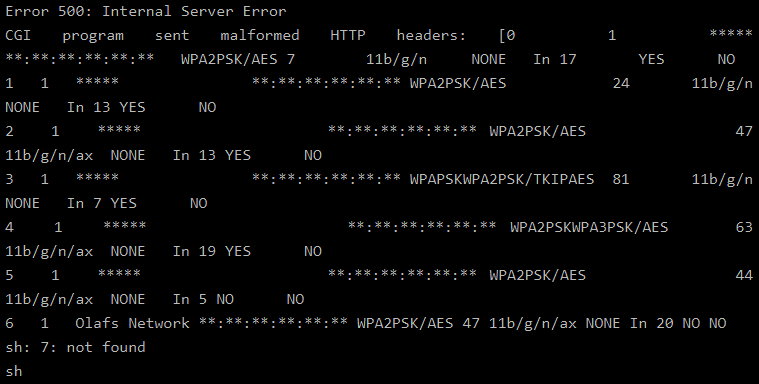
If the attacker provides a second part to the SSID that comprises a shell command separated by “&&” like “Check’ && uname -a &&”, the extender shall be tricked to execute the ‘uname -a’ command upon setup/community scan.
All processes on the extender, together with any instructions injected by exterior risk actors, are run with root privileges, probably permitting the attackers to probe different gadgets related to the extender and additional their community infiltration.
The toughest prerequisite for the assault is forcing a community scan on the goal machine, however that is potential by performing a deauthentication assault.
A number of available software program instruments can generate and ship deauth packets to the extender, inflicting it to disconnect from its primary community and forcing the goal to carry out a community scan.
RedTeam researchers found the flaw in Could 2023 and reported it to D-Hyperlink, however regardless of a number of follow-ups, no reply was ever acquired.
Which means D-Hyperlink DAP-X1860 remains to be weak to assaults, and the comparatively easy exploitation mechanism makes the state of affairs dangerous.
House owners of DAP-X1860 extenders are really useful to restrict guide community scans, deal with sudden disconnections suspiciously, and switch off the extender when not actively used.
Additionally, contemplate putting IoT gadgets and vary extenders on a separate community remoted from delicate gadgets holding private or work information.
