Authored by Neil Tyagi
On 23 August 2023, NIST disclosed a essential RCE vulnerability CVE-2023-38831. It’s associated to an RCE vulnerability in WinRAR earlier than model 6.23. The problem happens as a result of a ZIP archive could embody a benign file (resembling an bizarre .JPG file) and likewise a folder that has the identical identify because the innocent file, and the contents of the folder (which can embody executable content material) are processed throughout an try and entry solely the benign file.
Our intelligence exhibits that this vulnerability is being exploited as early as April 2023. Let�s have a look at a pattern exploiting this vulnerability (Hash: bc15b0264244339c002f83e639c328367efb1d7de1b3b7c483a2e2558b115eaa)
- The picture beneath exhibits that the archive is called trading_system, which hints that it’s used to focus on merchants

- We will additionally see that the menace actor can craft the archive in order that folder and file names are the identical.
- That is attention-grabbing as Home windows doesn�t enable recordsdata and folders to have the identical identify in the identical path.
- This exhibits that it was weaponized after creating an everyday zip by altering the bytes to make the file and folder identify the identical.
- Additionally, word there’s a trailing house on the finish of the file and folder identify (in yellow).
- After we look contained in the folder, we see many recordsdata, however crucial file is highlighted, which is a bat file containing a malicious script.
- The bat file additionally has the identical identify because the benign file exterior the folder.
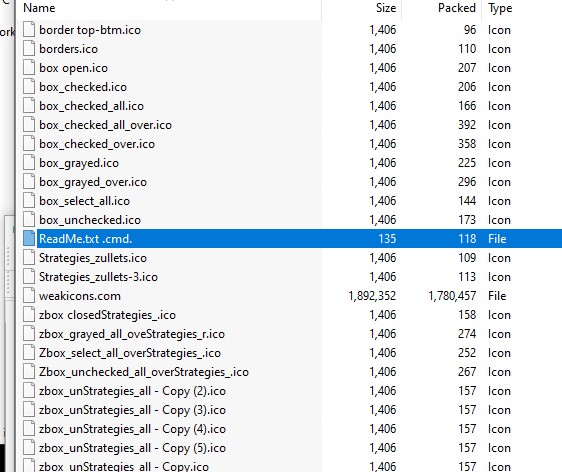
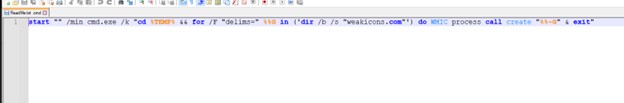
- After we test the script, we see it launches cmd within the minimized state, then goes to the temp folder the place WinRAR will extract the recordsdata, then tries to seek out the weakicons.com file, which is current contained in the folder and executes it utilizing wmic after which exits.
- Checking weakicons.com we discover that it’s a CAB SFX file.
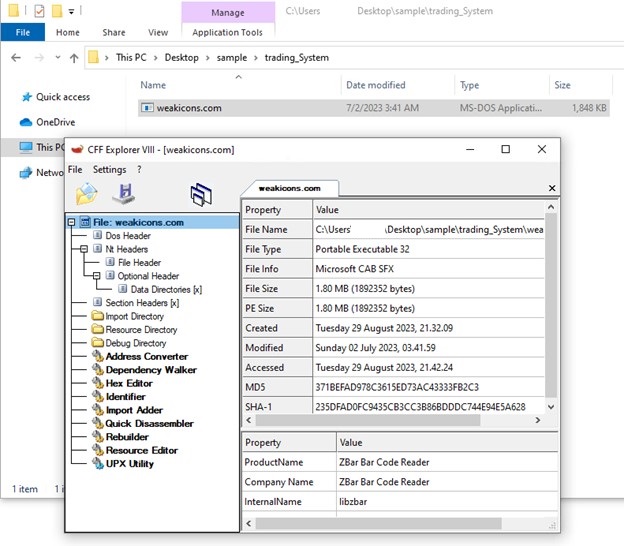
- We extract it to test what’s inside.
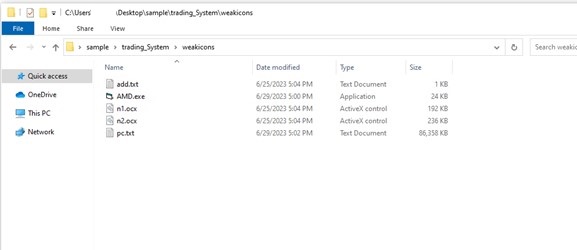
- We discovered a PE file, some ActiveX management objects, and two textual content recordsdata.
- AMD.exe is a visible primary compiled file whose primary job is to extract the dll hidden in a blob of information inside laptop.txt and execute the ActiveX controls.
- Inside add.txt, we discover the registry keys it can attempt to manipulate
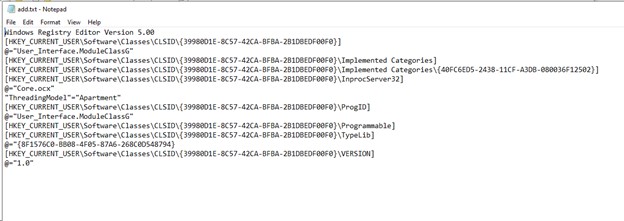
- The primary management is answerable for registering a COM object in Home windows. Throughout registration, registry keys are imported from the �add.txt� file. Because of this, a particular COM object with a novel CLSID is registered within the contaminated system. The default worth of the InprocServer32 secret’s populated with the trail to a malicious DLL named �Core.ocx�.

- Wmic course of executes weakicons.com

- AMD.exe extracts the encrypted dll file inside laptop.txt and writes it within the romaingnvidia folder.
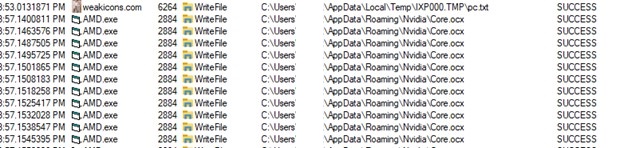
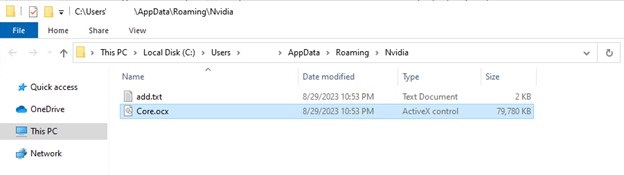
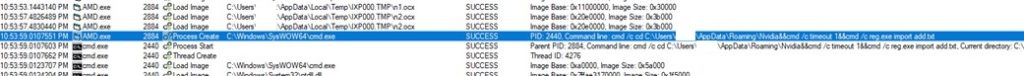
- Right here, we observe AMD.exe calls reg.exe on registry keys inside add.txt
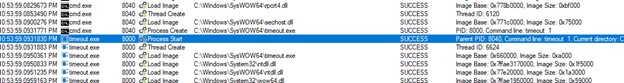
- Timeout can also be known as to decelerate the actions of the an infection chain.
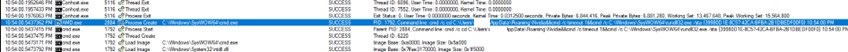
- AMD.exe Calls rundll32 on the clsid that’s registered within the registry
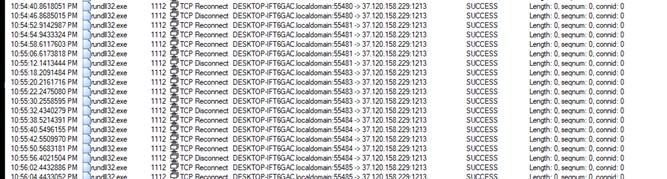
- We will see profitable tcp connection to menace actors C2.( ip 37[.]120[.]158[.]229)
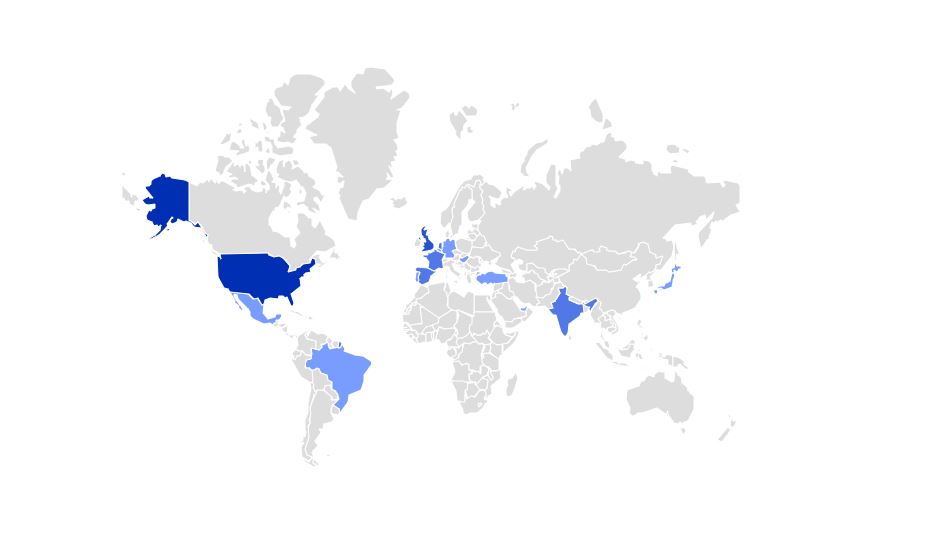
World Heatmap the place this vulnerability is being seen within the wild(based mostly on McAfee telemetry knowledge)
An infection chain
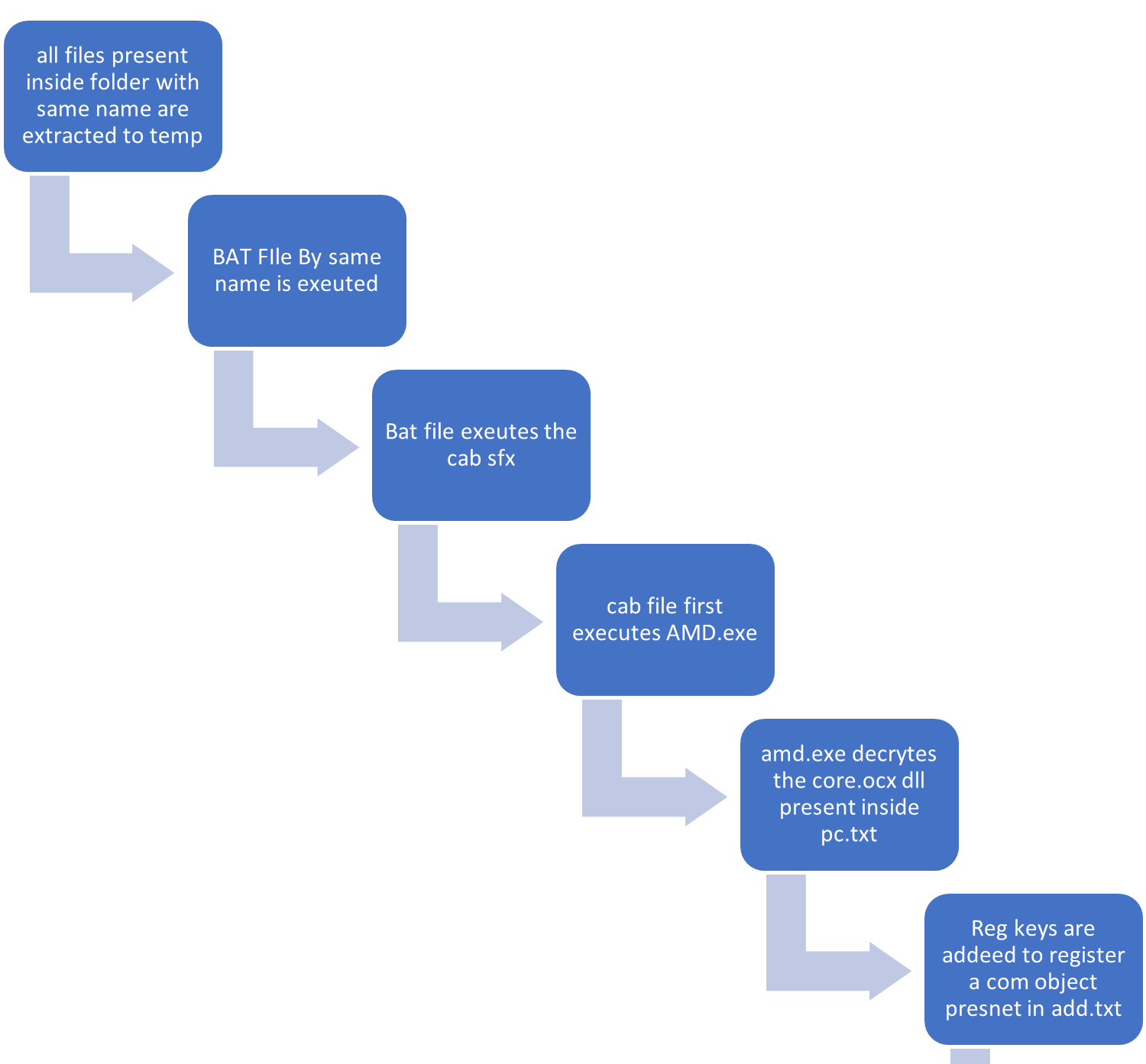
How does the vulnerability work?
- Right here, we are going to analyze the problem inflicting WinRAR to execute the script as a substitute of opening the picture.
- We’ll evaluate how WinRAR behaves once we execute a picture file from a weaponized zip vs. a traditional zip. So we hearth up ProcMon First.
Regular.zip
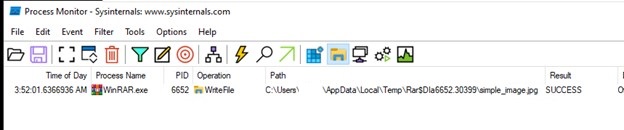
Weaponized.zip
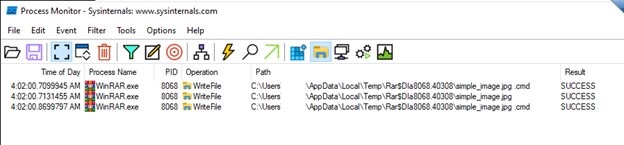
- The above picture exhibits that the primary logical bug is how WinRAR is extracting recordsdata within the temp folder earlier than executing them. Within the case of an everyday zip, solely the clear picture file is extracted to the temp folder, whereas within the case of a weaponized zip, even the recordsdata current contained in the folder are extracted to the temp folder together with the clear picture file. That is as a result of identical file names we’ve got given, which makes WinRAR extract these in temp.
- Verifying the identical within the temp folder
Regular Zip
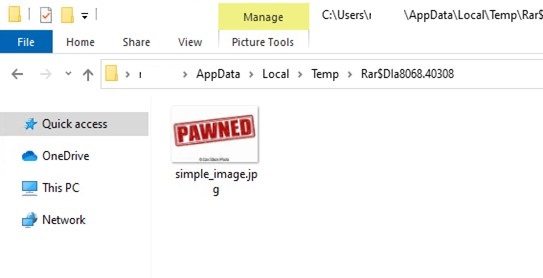
Weaponized Zip
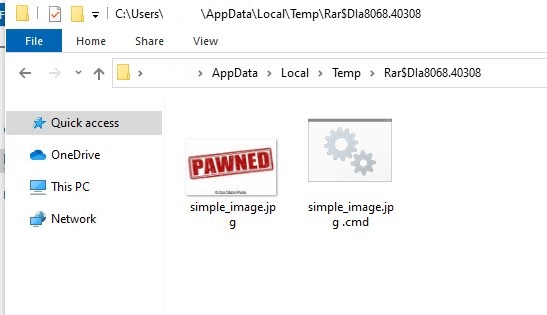
- In Logs, once we dig deep, we are able to see Winrar searches for our filename with an *, which causes it to iterate over our bat file because it has the identical identify, which in flip will get executed.
![]()
![]()
![]()
- To see what�s taking place underneath the hood, we hook a debugger and launch WinRAR by manipulating the �picture file Execution choices� registry key.
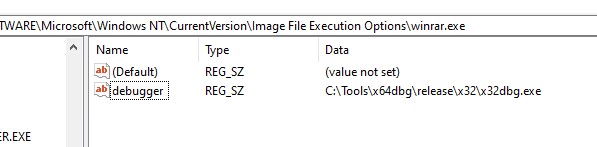
- After we execute the rar file, we see the debugger getting hooked up to the winrar course of in order that we are able to do just-in-time debugging.
- We put a breakpoint on the ShellExecuteExW operate to see what parameters are handed to it simply after clicking the jpeg file.
- After we double-click on the picture file, we are able to see the debugger is opened, and after just a few clicks, we hit our breakpoint.
Regular zip

- On this case, the proper parameter is handed to the ShellExecuteExW operate because the file exists at this precise path.
Weaponized zip

- On this case, an incorrect parameter is handed to the ShellExecuteExW operate because the parameter accommodates a trailing house, and such a file doesn’t exist on the disk.
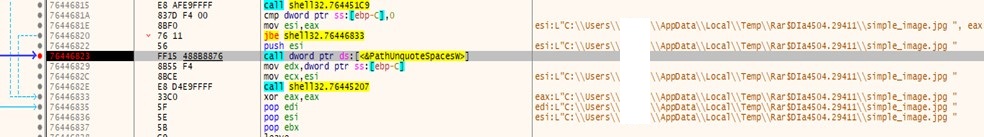
- After we dig deep, we discover that later, it calls PathUnquoteSpacesA API name, as per MSDN. It �Removes quotes from the start and finish of a path.�
- As quotes are faraway from the top of the trail, ShellExecuteExW executes �simple_image.jpg .cmd� as a substitute of �simple_image.jpg.�
IOC�s
| Sha256 | Detection |
| bc15b0264244339c002f83e639c328367efb1d7de1b3b7c483a2e2558b115eaa | Trojan:Archive/2023_38831.NEAA
� |
�
- .( ip 37[.]120[.]158[.]229)
- REG keys
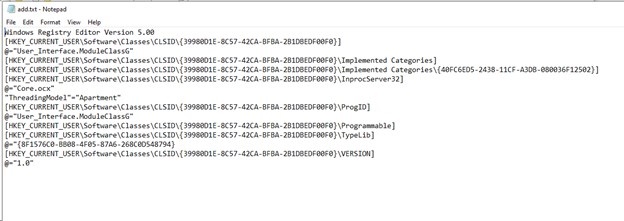
%APPDATApercentNvidiaCore.ocx
Suggestions
- WinRAR customers ought to instantly replace to the most recent model. WinRAR archiver, a strong software to course of RAR and ZIP recordsdata (rarlab.com)
- Use a licensed and up to date McAfee+ subscription to remain protected.
- Keep knowledgeable about frequent cyber threats and ways utilized by cybercriminals. This data might help you acknowledge potential dangers and keep away from scams.
- Be very cautious when coping with attachments from unknown sources. Solely run attachments that come from trusted sources.
- Shield your accounts through the use of multi-factor authentication.


