
Google is on the point of check a brand new “IP Safety” function for the Chrome browser that enhances customers’ privateness by masking their IP addresses utilizing proxy servers.
Recognizing the potential misuse of IP addresses for covert monitoring, Google seeks to strike a steadiness between guaranteeing customers’ privateness and the important functionalities of the online.
IP addresses permit web sites and on-line providers to trace actions throughout web sites, thereby facilitating the creation of persistent person profiles. This poses vital privateness considerations as, not like third-party cookies, customers at present lack a direct strategy to evade such covert monitoring.
What’s Google’s proposed IP Safety function?
Whereas IP addresses are potential vectors for monitoring, they’re additionally indispensable for vital internet functionalities like routing visitors, fraud prevention, and different important community duties.
The “IP Safety” resolution addresses this twin function by routing third-party visitors from particular domains via proxies, making customers’ IP addresses invisible to these domains. Because the ecosystem evolves, so will IP Safety, adapting to proceed safeguarding customers from cross-site monitoring and including extra domains to the proxied visitors.
“Chrome is reintroducing a proposal to guard customers in opposition to cross-site monitoring through IP addresses. This proposal is a privateness proxy that anonymizes IP addresses for qualifying visitors as described above,” reads an outline of the IP Safety function.
Initially, IP Safety will likely be an opt-in function, guaranteeing customers have management over their privateness and letting Google monitor habits traits.
The function’s introduction will likely be in phases to accommodate regional issues and guarantee a studying curve.
In its preliminary method, solely the domains listed will likely be affected in third-party contexts, zooming in on these perceived to be monitoring customers.
The primary part, dubbed “Section 0,” will see Google proxying requests solely to its personal domains utilizing a proprietary proxy. This may assist Google check the system’s infrastructure and purchase extra time to fine-tune the area listing.
To begin, solely customers logged into Google Chrome and with US-based IPs can entry these proxies.
A choose group of purchasers will likely be mechanically included on this preliminary check, however the structure and design will endure modifications because the checks progress.
To avert potential misuse, a Google-operated authentication server will distribute entry tokens to the proxy, setting a quota for every person.
In upcoming phases, Google plans to undertake a 2-hop proxy system to extend privateness additional.
“We’re contemplating utilizing 2 hops for improved privateness. A second proxy could be run by an exterior CDN, whereas Google runs the primary hop,” explains the IP Safety explainer doc.
“This ensures that neither proxy can see each the shopper IP deal with and the vacation spot. CONNECT & CONNECT-UDP assist chaining of proxies.”
As many on-line providers make the most of GeoIP to find out a customers location for providing providers, Google plans on assigning IP addresses to proxy connections that characterize a “coarse” location of a person reasonably than their particular location, as illustrated beneath.
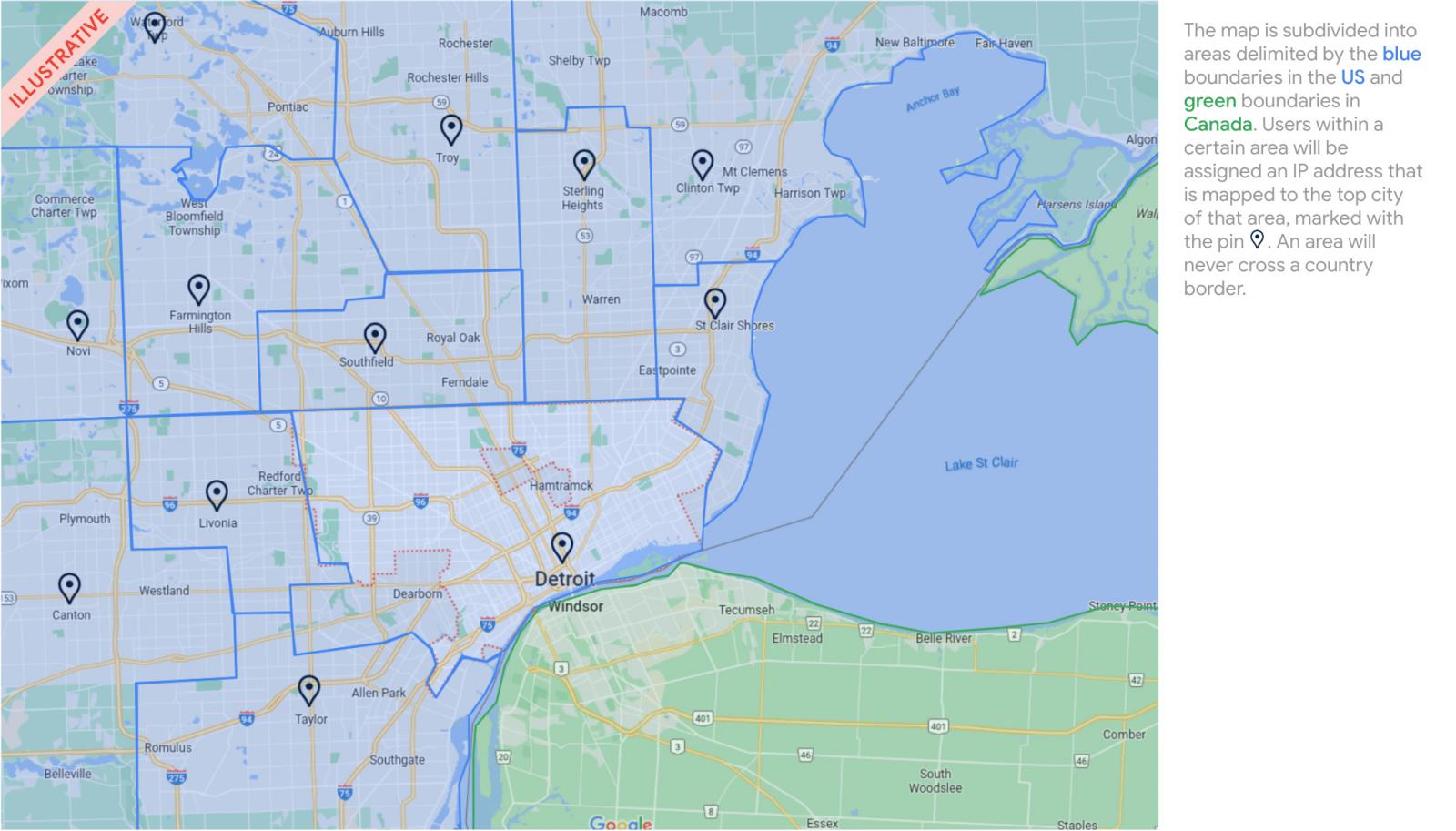
Supply: Google
Among the many domains the place Google intends to check this function are its personal platforms like Gmail and AdServices.
Google plans on testing this function between Chrome 119 and Chrome 225.
Potential safety considerations
Google explains there are some cybersecurity considerations associated to the brand new IP Safety function.
Because the visitors will likely be proxied via Google’s servers, it could make it tough for safety and fraud safety providers to dam DDoS assaults or detect invalid visitors.
Moreover, if considered one of Google’s proxy servers is compromised, the risk actor can see and manipulate the visitors going via it.
To mitigate this, Google is contemplating requiring customers of the function to authenticate with the proxy, stopping proxies from linking internet requests to explicit accounts, and introducing rate-limiting to stop DDoS assaults.
