
Google says that a number of state-backed hacking teams have joined ongoing assaults exploiting a high-severity vulnerability in WinRAR, a compression software program utilized by over 500 million customers, aiming to realize arbitrary code execution on targets’ methods.
Google’s Menace Evaluation Group (TAG), a workforce of safety consultants who defend Google customers from state-sponsored assaults, has detected state hackers from a number of nations focusing on the bug, together with the Sandworm, APT28, and APT40 risk teams from Russia and China.
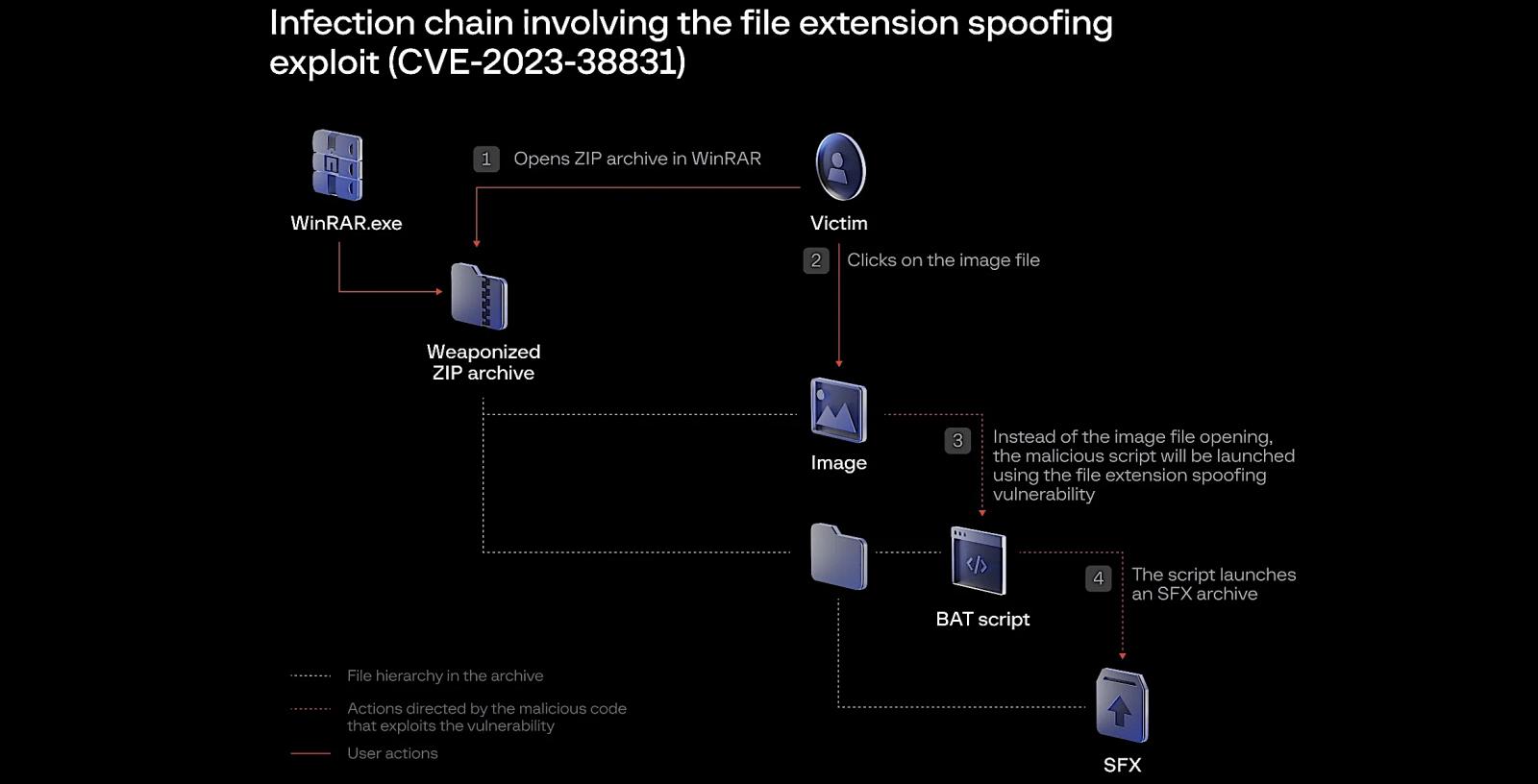
“In latest weeks, Google’s Menace Evaluation Group’s (TAG) has noticed a number of government-backed hacking teams exploiting the recognized vulnerability, CVE-2023-38831, in WinRAR, which is a well-liked file archiver instrument for Home windows,” Google stated at the moment.
“A patch is now out there, however many customers nonetheless appear to be weak. TAG has noticed government-backed actors from a lot of nations exploiting the WinRAR vulnerability as a part of their operations.”
In an early September assault, Russian Sandworm hackers delivered Rhadamanthys infostealer malware in phishing assaults utilizing pretend invites to affix a Ukrainian drone coaching college.
One other Russian hacking group, ATP28, focused Ukrainian customers with CVE-2023-38831 exploits hosted on servers offered by a free internet hosting supplier. On this assault, the risk actors used a malicious PowerShell script (IRONJAW) to steal browser credentials.
Moreover, APT40 Chinese language hackers exploit the WinRAR vulnerability in assaults in opposition to targets in Papua New Guinea. They deployed ISLANDSTAGER and BOXRAT, permitting them to ascertain persistence on compromised methods.
Exploited as a zero-day since April
The CVE-2023-38831 WinRar flaw has been beneath lively exploitation as a zero-day since no less than April 2023, permitting risk actors to realize code execution on their targets’ methods by tricking them into opening maliciously crafted RAR and ZIP archives containing booby-trapped decoy recordsdata.
Since April, the bug has been used to ship a variety of malware payloads, together with DarkMe, GuLoader, and Remcos RAT.
Group-IB researchers found situations of exploitation focusing on cryptocurrency and inventory buying and selling boards. In these assaults, the risk actors impersonated fellow fans whereas pretending to share buying and selling methods with unsuspecting victims.
?Inside hours of Group-IB disclosing their findings, proof of idea exploits started surfacing on public GitHub repositories, instantly resulting in what Google TAG describes as CVE-2023-38831 “testing exercise” by financially motivated hackers and APT teams.
Different cybersecurity corporations have additionally linked assaults exploiting this WinRAR with a number of different risk teams, together with DarkPink (NSFOCUS) and Konni (Knownsec).
The zero-day was mounted with the discharge of WinRAR model 6.23 on August 2, which additionally resolved a number of different safety flaws. Certainly one of them is CVE-2023-40477, a bug that may be exploited to set off command execution through specifically crafted RAR recordsdata.
“The widespread exploitation of the WinRAR bug highlights that exploits for recognized vulnerabilities may be extremely efficient, regardless of a patch being out there. Even essentially the most refined attackers will solely do what is important to perform their targets,” Google stated.
“These latest campaigns exploiting the WinRAR bug underscore the significance of patching and that there’s nonetheless work to be achieved to make it simple for customers to maintain their software program safe and up-to-date.”
