
The ransomware actor ‘ShadowSyndicate’ was noticed scanning for servers weak to CVE-2024-23334, a listing traversal vulnerability within the aiohttp Python library.
Aiohttp is an open-source library constructed on high of Python’s asynchronous I/O framework, Asyncio, to deal with giant quantities of concurrent HTTP requests with out conventional thread-based networking.
It’s utilized by tech corporations, internet builders, backend engineers, and information scientists seeking to construct high-performance internet functions and companies that mixture information from a number of exterior APIs.
On January 28, 2024, aiohttp launched model 3.9.2, addressing CVE-2024-23334, a high-severity path traversal flaw impacting all variations of aiohttp from 3.9.1 and older that enables unauthenticated distant attackers to entry information on weak servers.
The flaw is because of insufficient validation when ‘follow_symlinks’ is ready to ‘True’ for static routes, permitting unauthorized entry to information outdoors the server’s static root listing.
On February 27, 2024, a researcher launched a proof of idea (PoC) exploit for CVE-2024-23334 on GitHub, whereas an in depth video showcasing step-by-step exploitation directions was printed on YouTube at the beginning of March.
Cyble’s risk analysts report that their scanners have caught exploitation makes an attempt concentrating on CVE-2024-23334 beginning on February 29 and persevering with at an elevated charge into March.
The scanning makes an attempt originate from 5 IP addresses, considered one of which was tagged in a September 2023 report by Group-IB, who linked it to the ShadowSyndicate ransomware actor.
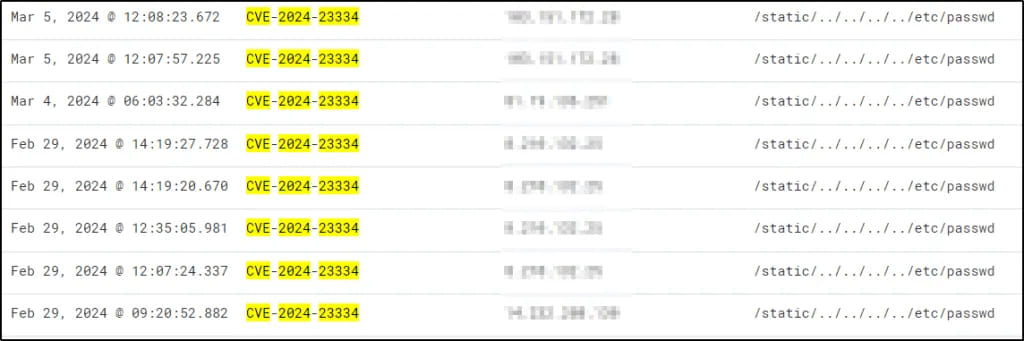
ShadowSyndicate is an opportunistic, financially-motivated risk actor, lively since July 2022, who was linked with varied levels of confidence to ransomware strains akin to Quantum, Nokoyawa, BlackCat/ALPHV, Clop, Royal, Cactus, and Play.
Group-IB believes the risk actor is an affiliate working with a number of ransomware operations.
Cyble’s discovering, although not definitive, signifies that the risk actors could be finishing up scans concentrating on servers utilizing a weak model of the aiohttp library. Whether or not or not these scans flip into breaches stays unknown presently.
Relating to the assault floor, Cyble’s web scanner ODIN reveals there are roughly 44,170 internet-exposed aiohttp situations all over the world. Most (15.8%) are positioned in the US, adopted by Germany (8%), Spain (5.7%), the UK, Italy, France, Russia, and China.
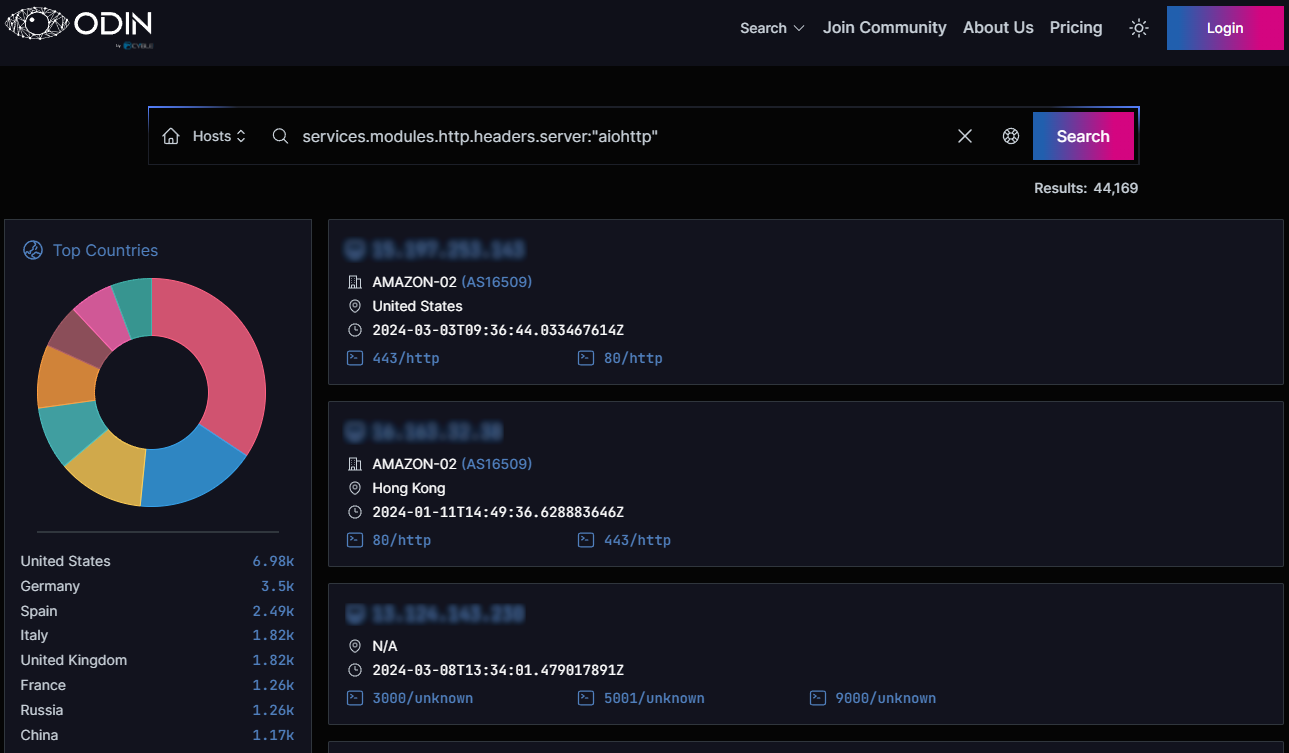
The model of the internet-exposed situations run can’t be discerned, making it arduous to find out the variety of weak aiohttp servers.
Sadly, open-source libraries are sometimes utilized in outdated variations for prolonged intervals as a consequence of varied sensible points that complicate finding and patching them.
This makes them extra helpful to risk actors, who leverage them in assaults even after years have handed since a safety replace was made out there.
