An advert fraud botnet dubbed PEACHPIT leveraged a military of a whole bunch of 1000’s of Android and iOS gadgets to generate illicit income for the menace actors behind the scheme.
The botnet is a component of a bigger China-based operation codenamed BADBOX, which additionally entails promoting off-brand cell and linked TV (CTV) gadgets on well-liked on-line retailers and resale websites which might be backdoored with an Android malware pressure known as Triada.
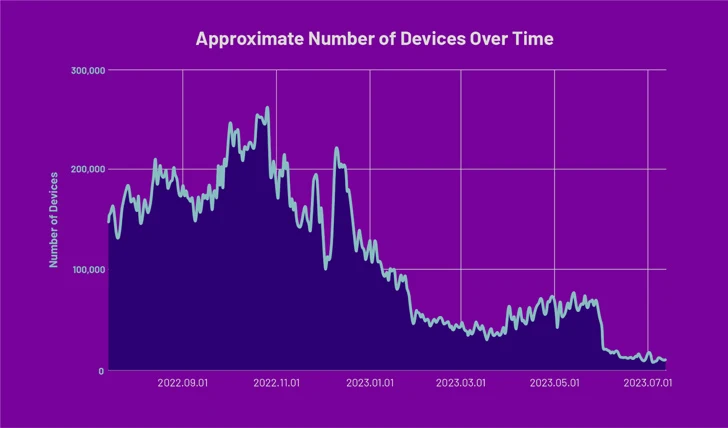
“The PEACHPIT botnet’s conglomerate of related apps have been present in 227 nations and territories, with an estimated peak of 121,000 gadgets a day on Android and 159,000 gadgets a day on iOS,” HUMAN mentioned.
The infections are mentioned to have been realized via a group of 39 apps that have been put in greater than 15 million instances. Gadgets fitted with the malware allowed the operators to steal delicate knowledge, create residential proxy exit friends, and commit advert fraud via the bogus apps.
It is at the moment not clear how the Android gadgets are compromised with a firmware backdoor, however proof factors to a {hardware} provide chain assault.
“Menace actors can even use the backdoored gadgets to create WhatsApp messaging accounts by stealing one-time passwords from the gadgets,” the corporate mentioned.
“Moreover, menace actors can use the gadgets to create Gmail accounts, evading typical bot detection as a result of the account seems prefer it was created from a standard pill or smartphone, by an actual particular person.”
Particulars concerning the felony enterprise have been first documented by Pattern Micro in Might 2023, attributing it to an adversary it tracks as Lemon Group.
HUMAN mentioned that it recognized at the least 200 distinct Android gadget varieties, together with cellphones, tablets, and CTV merchandise, which have exhibited indicators of BADBOX an infection, suggesting a widespread operation.
A notable side of the advert fraud is using counterfeit apps on Android and iOS made out there on main app marketplaces such because the Apple App Retailer and Google Play Retailer in addition to these which might be mechanically downloaded to backdoored BADBOX gadgets.
Current inside the Android apps is a module liable for creating hidden WebViews which might be then used to request, render, and click on on advertisements, and masquerading the advert requests as originating from professional apps, a way beforehand noticed within the case of VASTFLUX.
The fraud prevention agency famous that it labored with Apple and Google to disrupt the operation, including “the rest of BADBOX needs to be thought-about dormant: the C2 servers powering the BADBOX firmware backdoor an infection have been taken down by the menace actors.”
What’s extra, an replace pushed out earlier this 12 months has been discovered to take away the modules powering PEACHPIT on BADBOX-infected gadgets in response to mitigation measures deployed in November 2022.
That having mentioned, it is suspected the attackers are adjusting their ways in a probable try to avoid the defenses.
“What makes issues worse is the extent of obfuscation the operators went via to go undetected, an indication of their elevated sophistication,” HUMAN mentioned. “Anybody can unintentionally purchase a BADBOX gadget on-line with out ever understanding it was pretend, plugging it in, and unknowingly opening this backdoor malware.”