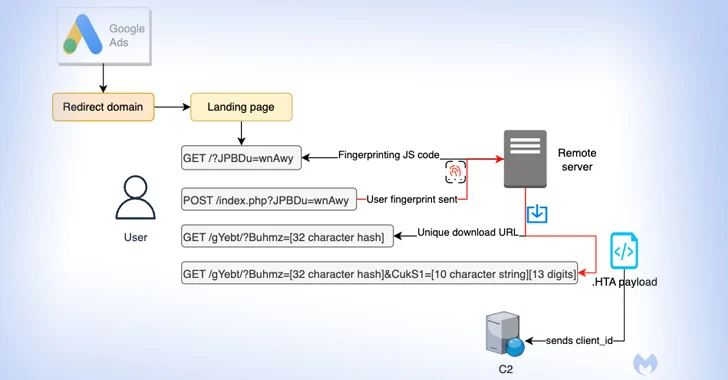
Particulars have emerged a few malvertising marketing campaign that leverages Google Advertisements to direct customers looking for common software program to fictitious touchdown pages and distribute next-stage payloads.
Malwarebytes, which found the exercise, mentioned it is “distinctive in its strategy to fingerprint customers and distribute time delicate payloads.”
The assault singles out customers looking for Notepad++ and PDF converters to serve bogus adverts on the Google search outcomes web page that, when clicked, filters out bots and different unintended IP addresses by displaying a decoy web site.
Ought to the customer be deemed of curiosity to the risk actor, the sufferer is redirected to a reproduction web site promoting the software program, whereas silently fingerprinting the system to find out if the request is originating from a digital machine.
Customers who fail the examine are taken to the respectable Notepad++ web site, whereas a possible goal is assigned a singular ID for “monitoring functions but in addition to make every obtain distinctive and time delicate.”
The ultimate-stage malware is an HTA payload that establishes a connection to a distant area (“mybigeye[.]icu”) on a customized port and serves follow-on malware.
“Menace actors are efficiently making use of evasion methods that bypass advert verification checks and permit them to focus on sure forms of victims,” Jérôme Segura, director of risk intelligence, mentioned.
“With a dependable malware supply chain in hand, malicious actors can give attention to enhancing their decoy pages and craft customized malware payloads.”
The disclosure overlaps with an analogous marketing campaign that targets customers looking for the KeePass password supervisor with malicious adverts that direct victims to a site utilizing Punycode (keepass[.]information vs ķeepass[.]information), a particular encoding used to transform Unicode characters to ASCII.
“Individuals who click on on the advert will likely be redirected through a cloaking service that’s meant to filter sandboxes, bots and anybody not deemed to be a real sufferer,” Segura famous. “The risk actors have arrange a brief area at keepasstacking[.]web site that performs the conditional redirect to the ultimate vacation spot.”
Customers who land on the decoy web site are tricked into downloading a malicious installer that in the end results in the execution of FakeBat (aka EugenLoader), a loader engineered to obtain different malicious code.
The abuse of Punycode will not be completely novel, however combining it with rogue Google Advertisements is an indication that malvertising through engines like google is getting extra refined. By using Punycode to register related domains as respectable web site, the objective is to tug off a homograph assault and lure victims into putting in malware.
“Whereas Punycode with internationalized domains has been used for years by risk actors to phish victims, it exhibits how efficient it stays within the context of name impersonation through malvertising,” Segura mentioned.
Talking of visible trickery, a number of risk actors – TA569 (aka SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), ClearFake, and EtherHiding – have been noticed benefiting from themes associated to pretend browser updates to propagate Cobalt Strike, loaders, stealers, and distant entry trojans, an indication that these assaults are a continuing, evolving risk.
“Faux browser updates abuse finish consumer belief with compromised web sites and a lure personalized to the consumer’s browser to legitimize the replace and idiot customers into clicking,” Proofpoint researcher Dusty Miller mentioned in an evaluation printed this week.
“The risk is just within the browser and could be initiated by a click on from a respectable and anticipated electronic mail, social media web site, search engine question, and even simply navigating to the compromised web site.”