
A bunch of cyber activists underneath the Ukrainian Cyber Alliance banner has hacked the servers of the Trigona ransomware gang and wiped them clear after copying all the data accessible.
The Ukrainian Cyber Alliance fighters say they exfiltrated the entire information from the menace actor’s techniques, together with supply code and database data, which can embrace decryption keys.
Trigona ransomware out of fee
Ukrainian Cyber Alliance hackers gained entry to Trigona ransomware’s infrastructure by utilizing a public exploit for CVE-2023-22515, a essential vulnerability in Confluence Knowledge Middle and Server that may be leveraged remotely to escalate privileges.
The vulnerability was leveraged in assaults as a zero-day since September 14 by a minimum of one menace group that Microsoft tracks as Storm-0062 (often known as DarkShadow and Oro0lxy).
The Ukrainian Cyber Alliance, or UCA for brief, first breached Trigona ransomware’s Confluence server about six days in the past, established persistence, and mapped the cybercriminal’s infrastructure fully unnoticed.
After a UCA activist utilizing the deal with herm1t printed screenshots of the ransomware gang’s inner help paperwork, BleepingComputer was instructed that Trigona ransomware initially panicked and responded by altering the password and taking down its public-facing infrastructure.
Nonetheless, over the following week, the activists managed to take all the data from the menace actor’s administration and sufferer panels, their weblog and information leak website, and inner instruments (Rocket.Chat, Jira, and Confluence servers).
herm1t instructed BleepingComputer that additionally they exfiltrated the developer atmosphere, cryptocurrency scorching wallets in addition to the supply code and database data.
The activists don’t know if the data they transferred comprises any decryption keys however they mentioned they’d launch them if discovered.
After harvesting all accessible information from the ransomware gang, the UCA activists deleted and defaced their websites, additionally sharing the important thing for the administration panel website.
supply: herm1t
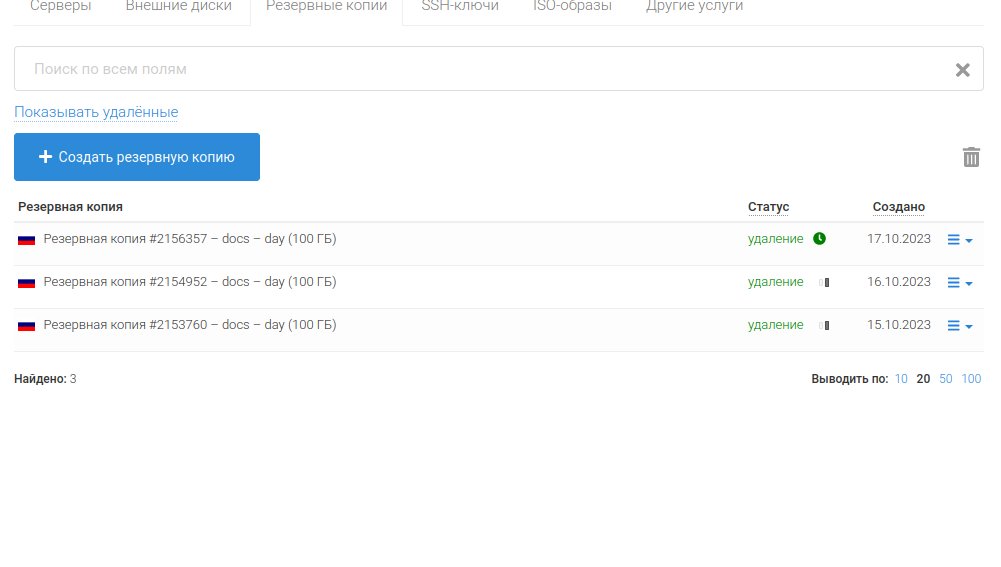
UCA claims that they had been capable of retrieve three backups with a whole lot of gigabytes of possible stolen paperwork.
supply: herm1t
The Ukrainian Cyber Alliance
Beginning in 2014, a number of hacktivists in Ukraine and all over the world began working collectively to defend the nation’s our on-line world in opposition to Russian aggression.
About two years later, particular person hackers and a number of other hacker teams united to type the Ukrainian Cyber Alliance, now registered as a non-governmental group, and started to focus on varied organizations and people supporting Russia’s exercise in opposition to Ukraine.
The identities of the members of the group are secret, aside from those who set it up as an official entity whose work is ruled by the civic obligation for the nation.
In keeping with the group’s Wikipedia web page, its members carried out a number of profitable hacking operations that resulted in exposing details about Russian exercise and propaganda efforts in Ukraine and different international locations, in addition to its management over varied people and entities.
Amongst UCA’s claims are hacking the Russian Ministry of Protection twice in 2016 and leaking public protection contracts and confidential information on the availability of the state protection order of 2015–2016.
One other success was hacking the emails of Vladislav Surkov, a person believed to have designed the equipment for the Russian propaganda of the previous years, the place he mentioned the annexation of Crimea and learn how to fund the Luhansk and Donetsk territories after they grew to become Russian republics.
Trigona ransomware exercise
The Trigona ransomware operation emerged underneath this title in late October final 12 months, when the gang launched a Tor website to barter ransom funds in Monero cryptocurrency with victims of their assaults.
Beforehand, samples of the malware had no particular title and had been noticed within the wild because the starting of 2022. Earlier than the Trigona branding, the operators used electronic mail to barter the ransom funds.
For some time, the cybercriminals had been sufficiently lively to compromise in a single month a minimum of 15 corporations within the manufacturing, finance, building, agriculture, advertising, and excessive know-how sectors.
Earlier this 12 months, Trigona hackers had been focusing on Microsoft SQL servers uncovered on the general public web utilizing brute-force or dictionary assaults to acquire entry credentials.
For the time being, as a result of Ukrainian Cyber Alliance’s current actions, not one of the Trigona ransomware public web sites and providers are on-line.
