US meals supply compeny PurFoods, which trades as Mother’s Meals, has simply admitted to a cyberintrusion that passed off from 2023-01-16 to 2023-02-22.
The corporate acknowledged formally that:
[The] cyberattack […] included the encryption of sure information in our community.
As a result of the investigation recognized the presence of instruments that may very well be used for information exfiltration (the unauthorized switch of knowledge), we will’t rule out the likelihood that information was taken from one among our file servers.
PurFoods says it has contacted everybody whose was affected, or a minimum of everybody whose information appeared in a number of of the scrambled information, which we assume are the information that the corporate thinks the attackers would have stolen, if certainly any information was exfiltrated.
What’s in danger
The corporate didn’t say how many individuals had been caught up on this incident, however a current report on IT information website The Register places the entire at greater than 1,200,000 people.
PurFoods listed these affected as:
Shoppers of PurFoods who acquired a number of meal deliveries, in addition to some present and former staff and impartial contractors.
The data within the information included date of delivery, driver’s license/state identification quantity, monetary account info, fee card info, medical report quantity, Medicare and/or Medicaid identification, well being info, therapy info, prognosis code, meal class and/or value, medical insurance info, and affected person ID quantity.
Social Safety numbers [SSNs] had been concerned for lower than 1% of the [individuals], most of that are inner to PurFoods.
We’re guessing that the corporate didn’t accumulate SSNs for patrons, although we’d anticipate them to wish SSN information for workers, which is why the at-risk SSNs are listed as “inner”.
However when you’re questioning why a meals supply firm would want to gather clients’ medical particulars, together with well being and therapy info…
…nicely, we puzzled that, too.
It appears that evidently the corporate specialises in offering meals for folks with particular dietary wants, comparable to these with diabetes, kidney issues and different medical circumstances, for whom meals components must be chosen fastidiously.
Mother’s Meals subsequently wants medical particulars for some, if not all, of its clients, and that information was blended in with loads of different personally identifiable info (PII) which will now be within the palms of cybercriminals.
What to do?
In case you’re one of many greater than one million affected clients:
- Take into account changing your fee card if yours was listed as presumably stolen. Most banks will situation new fee playing cards promptly, thus mechanically invalidating your outdated card and making the outdated card particulars ineffective to anybody who has them now or buys them up in a while the darkish internet.
- Watch your statements fastidiously. It is best to do that anyway, so that you simply spot anomalies as quickly as you may, but it surely’s value holding a more in-depth eye on what’s occurring together with your monetary accounts if there’s proof you may be at a greater-than-usual danger of id theft or card abuse.
- Take into account implementing a credit score freeze. This provides an additional layer of authorisation from you that’s wanted earlier than something in your credit score report may be launched to anybody. This makes it more durable for crooks to accumulate loans, bank cards and the like in your identify (though this clearly makes it more durable – and thus takes longer – so that you can get a brand new mortgage, bank card or mortgage, too). Sadly, activating a credit score freeze means it’s good to ship a considerable amount of PII, together with a replica of your picture ID and your SSN, to one among three foremost credit score bureaus.
In case you’re an organization that handles important PII of this kind:
- Act instantly when any anomalies are detected in your community. On this assault, the criminals had been apparently contained in the PurFoods community for greater than a month, however had been solely noticed after they’d obtained so far as scrambling information, presumably as a foundation for extorting cash from the corporate.
- Think about using a Managed Detection and Response (MDR) service when you can’t sustain by yourself. Good risk searching instruments not solely seek for and forestall the activation of malware, but additionally aid you to detect weak spots in your community comparable to unprotected or unpatched computer systems, and to determine and isolate behaviour that’s generally seen within the build-up to a full-blown assault. Having risk searching consultants readily available on a regular basis makes it more likely that you simply’ll spot any hazard indicators earlier than it’s too late.
- Be as fast and as clear as you may in any information breach notifications. Regardless of the suggestion that this was a two-pronged steal-data-and-then-scramble-it assault, recognized within the jargon as double extortion, PurFoods hasn’t made it clear what actually occurred, regardless that the corporate tooks a number of months to analyze and publish its report. For instance, we nonetheless don’t know whether or not the corporate acquired any blackmail calls for, whether or not there was any “negotiation” with the attackers, or whether or not any cash modified palms in return for hushing up the incident or for getting again decryption keys to get better the scrambled information.
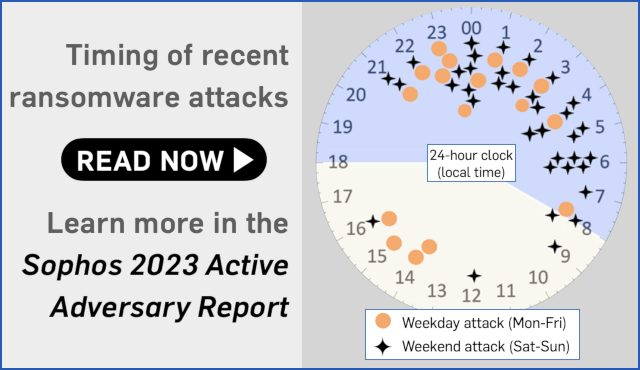
In accordance with the info within the newest Sophos Energetic Adversary report, the median common dwell time in ransomware assaults (the time it takes between the crooks first breaking into your community and getting themselves right into a place to compromise all of your information in a single simultaneous strike) is now down to simply 5 days.
That signifies that if your organization does get “chosen” by ransomware criminals for his or her subsequent money-grabbing assault, there’s a higher than 50% probability that you simply’ll have lower than every week to identify the crooks sneaking round preparing on your community doomsday occasion.
Worse nonetheless, the ultimate hammer blow unleashed by ransomware attackers is more likely to be at a deeply inconvenient time on your personal IT staff, with the file-scrambling denouement usually unleashed between 21:00 and 06:00 (9pm to 6am) in your native timezone.
To counter-paraphrase Mr Miagi of Karate Child fame: Greatest approach to keep away from punch is to be there on a regular basis, monitoring and reacting as quickly as you may.
In need of time or experience to deal with cybersecurity risk response? Fearful that cybersecurity will find yourself distracting you from all the opposite issues it’s good to do?
Study extra about Sophos Managed Detection and Response:
24/7 risk searching, detection, and response ?